IP Spoofing Attack: Explained
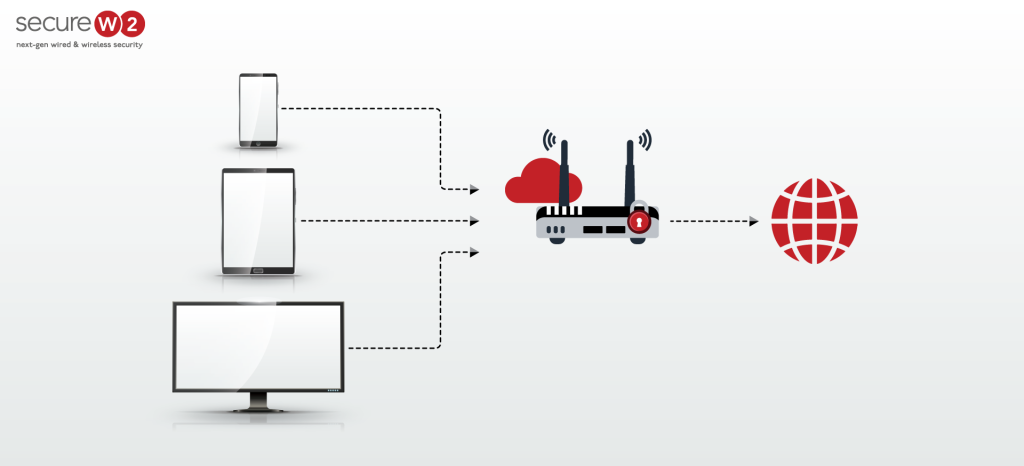
One nasty strategy that needs our attention in the ever-changing environment of cybersecurity threats is IP spoofing. Given the increasing integration of the digital sphere into our everyday lives, it is important to comprehend the consequences of IP spoofing attacks. Consider the case when a cybercriminal sets up a phony coffee shop with a free […]
Read Story