Does FreeRADIUS support Mac Auth Bypass?
Mac Auth Bypass is used to manage devices that do not support 802.1X like smart appliances used at home, medical IoT devices like patient bedside monitors, fitness trackers, and printers. These devices, collectively known as the Internet of Things (IoT), are fast becoming an integral part of our day-to-day life both workwise and for our personal consumption.
These devices are designed with a very narrow scope in mind. A fitness tracker will track the steps you walked and your heart rate, whereas a smart refrigerator will keep track of the items stored, what temperature is perfect for preserving a particular food item, etc. The ability to track and monitor to such a minute level is what makes IoT devices so useful. However, they often do not support 802.1X authentication because they use non-standard operating systems, though they need to access the organization’s network to work. Adding unsecured devices to the network makes it vulnerable, especially as IoT devices are gateways for multiple types of cyber attacks.
Some of the most common attacks that IoT devices are vulnerable to are:
- Man-in-the-Middle (MITM) Attacks
- Eavesdropping
- Brute-force password attacks
- Privilege Escalation
IoT devices are an often neglected part of security because they themselves rarely handle sensitive data. What makes it dangerous to network security is that these devices need to connect to the network to run and without the proper network security protocols in place, anyone can use an IoT device to gain entry to the network, opening the door to catastrophic damage. It’s time we start taking seriously the task of securing and monitoring these devices for better security of a company’s network infrastructure.
Remote Authentication Dial-In User Service (RADIUS), or AAA (Authentication, Authorization, and Accounting) server is an IAM solution that determines if a user or a machine that is trying to connect to a network is authorized to access a network and the level of access they are to be provided. RADIUS does this by verifying the login credentials or certificates for machines that support 802.1X. The access level granted to the user or machine is determined by referring to Identity Providers (IDP) like Azure AD, Google, or Okta. However, RADIUS alone cannot IoT devices as it can verify devices that support 802.1X configuration. In order to get the IoT devices authenticated through RADIUS, a MAC auth bypass needs to be enabled in RADIUS.
MAC authentication bypass (MAB) can identify, authenticate, and determine the level of access of a device for IoT devices that do not support 802.1X configuration. When MAB is used with a RADIUS server it’s called RADIUS MAC authentication bypass. RADIUS MAC auth bypass can help minimize security risks as well as makes the IoT devices visible and easier to monitor and control. In this article, we discuss how to securely authenticate IoT devices with MAB and whether or not that’s supported by FreeRADIUS.
MAC Auth Bypass to Secure IoT Devices
MAC auth bypass, also known as MAB, is one solution that can help improve the security of these devices and help you manage these devices’ network access. Let‘s take a look at how it works.
MAC Auth Bypass
MAC Authentication Bypass (MAB) is an alternative protocol to authenticate devices that do not support the 802.1X protocol. In this protocol, the MAC address (Media Access Control Address) of a machine is used as the unique identifier to authenticate a device before allowing it access to a network. Though it is not the most secure authentication method, the visibility and entity-based access control help bring the otherwise unmanaged IoT devices under your network security purview. Access management with MAC auth bypass can be managed dynamically, their activity can be monitored and access revoked in real-time in case any threat is detected. Also, MAB is port-based, allowing a company to limit the access of the devices to only the degree that they need to function.
MAC auth bypass uses MAC address filtering (an access control solution that consists of a list of approved MAC addresses) to check if a particular MAC address has access to the network, and what level of access the device is allowed.
How RADIUS MAC Auth Bypass is Used to Authenticate Devices
Below are the steps that MAB takes to authenticate a user/machine before granting access to a network.
1. Initiation
The first step is done at the switch and RADIUS is not involved. Upon identifying that a device is trying to connect to the network, the switch submits an EAPoL identity request 3 times at an interval of 30 seconds to the endpoint. When there is no response from the endpoint after the third attempt, the switch attempts to use MAB to authenticate the devices as it reaches the conclusion the endpoint does not have an 802.1X supplicant.
2. RADIUS Mac Authentication
Once the switch determines that a device does not have a supplicant, it then initiates MAB. First, the switch accepts a single packet from an interface to determine the origin of the endpoint’s MAC address. After identifying the source MAC address, the packet is discarded and a RADIUS access-request-message is created with the device’s MAC address as the identity. This access-request message is then sent to the RADIUS server so that it may perform MAC authentication.
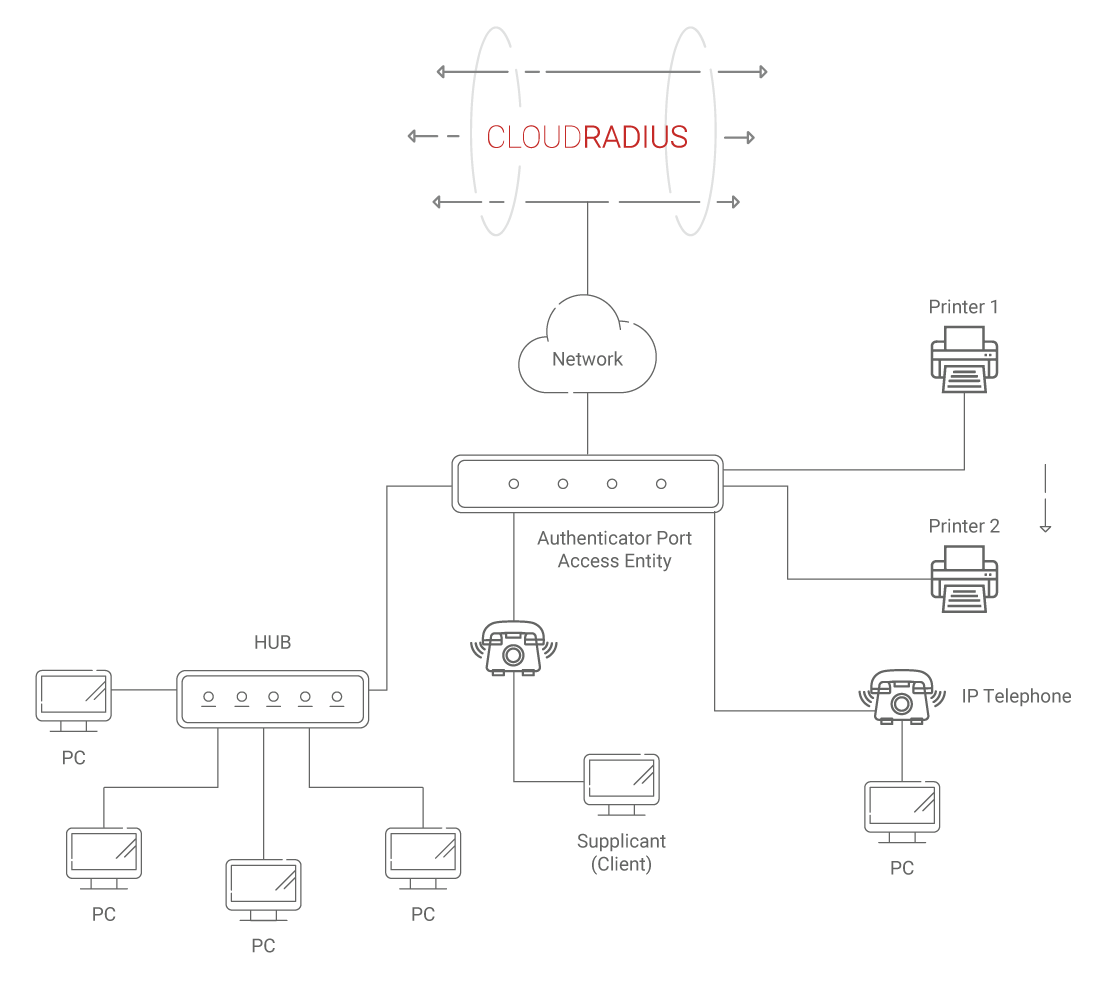
3. Authorization
The last step is where the RADIUS authentication server decides if the machine requesting access can be granted entry to the network and the level of access to the network the client/machine is to be given. Authorization options like Downloadable ACLs (dACLs), Dynamic VLANs (dVLANs), and Security Group Tags (SGT) are applied by RADIUS to determine and create and transmit access-accept to grant the user/machine access to the network.
FreeRADIUS & MAC Auth Bypass
MAC auth bypass can be used with FreeRADIUS for authenticating the machines that do not support 802.1X. There a multiple ways MAC auth bypass can be used in FreeRADIUS. Some of the modes are as follows.
1. MAC auth Bypass as a Stand Alone Protocol
This is the protocol where FreeRADIUS does MAC auth bypass directly, or as the only protocol for authentication. In this method, the MAC address of the machine is enough to authenticate before granting access to the network.
2. MAC Auth Bypass or 802.1X Alternatively
This protocol uses MAB and 802.1X alternatively, meaning either of the protocols can be applied at the time of authentication. In this mode, either the MAC address or valid login credentials can be used to log in to the network. The user can access the network using either of the options.
3. MAC Auth Bypass & 802.1X as a Combination
In this method, both MAB and 802.1X protocols are used to authenticate a device before granting access. If a machine is not able to authenticate using the 802.1X protocol, a MAC address is used to identify a user. And when 802.1X protocol is used, the MAC address is required along with digital credentials before getting access to the network.
4. Web Auth & MAC Auth
This method allows you to authenticate a machine using both web auth and MAC auth protocol. Web auth uses a web page login to authenticate users trying to access the network. After connecting to the switch, when a user opens a web page, the switch directs the user to a login page. Once the user enters the requested login credentials, the switch forwards the request to the RADIUS server that authenticates the machine and allows access to the network.
FreeRADIUS supports a number of MAB options for you to authenticate your IoT devices without 802.1X. However misconfiguring MAB is very possible and can have dire consequences. That’s broadly true of RADIUS as well, which is why you might consider a managed RADIUS service if you don’t already have experience setting up and running a FreeRADIUS installation.
Cloud MAC Auth Bypass with Dynamic RADIUS
MAC auth bypass is not the most secure authentication protocol. However, for IoT devices that do not support 802.1X and otherwise are not under the purview of network security, this is a very effective way to get better visibility and to bring these devices under effective management. When MAC auth bypass is used with a dynamic RADIUS like SecureW2 that supports cloud identity lookup, it can be implemented similarly to 802.1X with both VLAN assignments and a dynamic access list.
SecureW2 dynamic RADIUS is deployed in a cloud environment and what makes it unique is that it is integrated into your existing PKI infrastructure for identity lookup. It can do improved, certificate-based authentication runtime-level policy enforcement, and reinforced security by directory checks via a lightweight API designed to reduce request size and optimize authentication speed. In a typical certificate-based RADIUS authentication process, the RADIUS server references the certificate revocation list(CRL) to verify if a certificate is, however, a dynamic RADIUS will directly look up the directory to verify if a user is current and to make decisions on the user privileges. When MAB is implemented with a dynamic RADIUS, you can trace network activity on these devices, and limit network access with a dynamic access list in real-time.
SecureW2’s Cloud RADIUS with MAB and MAC address filtering helps you get better control over your IoT devices that do not support 802.1X authentication protocol. Managing and accounting for them with MAC auth bypass and MAC address Filtering to extend your network visibility to these unmanaged devices gives you better control over your network. Talk to our industry experts to know how our solutions can help make your IoT devices more secure.