Certificate Enrollment for Azure AD Conditional Access
Cloud-based network solutions are gaining popularity for multiple reasons, some of which are the ease of scaling, cost efficiency, and organizations going global with remote work – especially owing to the pandemic that forced us to restructure work culture. This has raised many security concerns too, with most organizations’ networks now being accessed from multiple locations.
In this article, we will take a look at Conditional Access in Azure AD, and why certificate-based authentication is better than credential-based authentication. We will also discuss a brief overview of how certificate enrollment for Azure AD Conditional Access works.
Azure AD (Azure Active Directory)
Azure AD is a cloud-based enterprise identity access management (IAM) solution that allows the use of authentication protocols like single sign-on, multifactor authentication, and conditional access to better manage network security. Azure AD is a real-time directory that stores client information like account details of users, their credentials, security groups for role-based access management, permissions, and company policies. Azure AD can be used to access external resources like Microsoft 365, the Azure portal, and other varied SaaS applications as well as internal resources like the intranet.
Azure AD Conditional Access
The policies within Azure AD that are used for developing better security for role-based access management are what is known as Azure AD conditional access. These are a set of rules or conditions that allow using multiple signals from different authentication methods, like biometrics and OTP. to enforce company policies and identity-based access management. In simple terms, it’s like a list of if-then conditions that help determine the identity of a user before granting them access.
Azure AD conditional access is applied to ensure any company data is accessed by only the users that are authorized to access the information. For example, only an HR person in the payroll department will have access to the salary and bank details of employees. The core utility for conditional access in Azure AD is to first empower users with the right data to perform their role at an optimal level, and finally to protect company data from any unauthorized access.
The general conditional signals applied by Azure AD conditional access are:
- User Groups or Security Groups for role-based access
- IP-based for defining location-based access
- Device Based
- Application Based
- Microsoft Defender
- Real-Time Risk Assessment & Access Control
These factors are taken into consideration when defining authentication protocols that are required to access the network. For example, users belonging to the IT administrators’ user group may be asked to do MFA authentication because of the level of sensitive information they access. Defining the policies that best fit your organization’s need help you regulate the access to your network to relevant users only.
Developing a Conditional Access Policy in Azure AD
Developing a conditional access policy in Azure AD is determined by the company policies that you want to implement. For example, an IT admin, in order to access network policy data, may have to use MFA authentication from a pre-defined device only.
In that condition, multiple policies are applied, one is the policy of authenticating the user with MFA authentications and the second policy defined to access the data is a device-based policy that requires the user to log in from a particular device. Both policies have to be satisfied to gain access.
These “if-then” conditions that are used in creating the conditional access policy in Azure AD can largely be divided into two primary categories.
1. Assignment
The assignment is related to the who, what, and where conditions of the Conditional Access Policy. Assignment conditions allow you to choose the user groups and applications to define the roles of users and the applications to which they are granted access. There are multiple signals like sign-in risks involved, device platforms used, location of the devices used, and the client platforms where access is needed. These conditions are used to define and implement role-based access policies like blocking access to a certain client application from unmanaged devices.
2. Access Controls
Access Control manages the implementation of conditional access policies that are in place. An admin user can grant or revoke access to users, devices, or locations depending on the policies that have been defined.
Using the option “Grant” access control allows network administrators to “Grant Access” or “Block Access” in order to enforce the company policies. Grant access policies can be defined using both the conditions “AND” and “Or”. That means you can define policies that say a user has to do MFA authentication using an OTP “AND” when logging in from a particular device, or OTP “Or” biometrics. Block Access policies allow you to block a user, location, or device in case of suspicious activity.
Security Challenges in Azure AD
Azure AD conditional access is an effective mechanism for enforcing company policies. But when used with a password-based authentication protocol, Azure AD suffers all the security issues of passwords like man-in-the-middle attacks, phishing, or malware attacks to name a few.
Let’s take a look at what are the benefits of authentication with 802.1X certificates in comparison to authentication using passwords.
Benefits of Certificates Vs Passwords
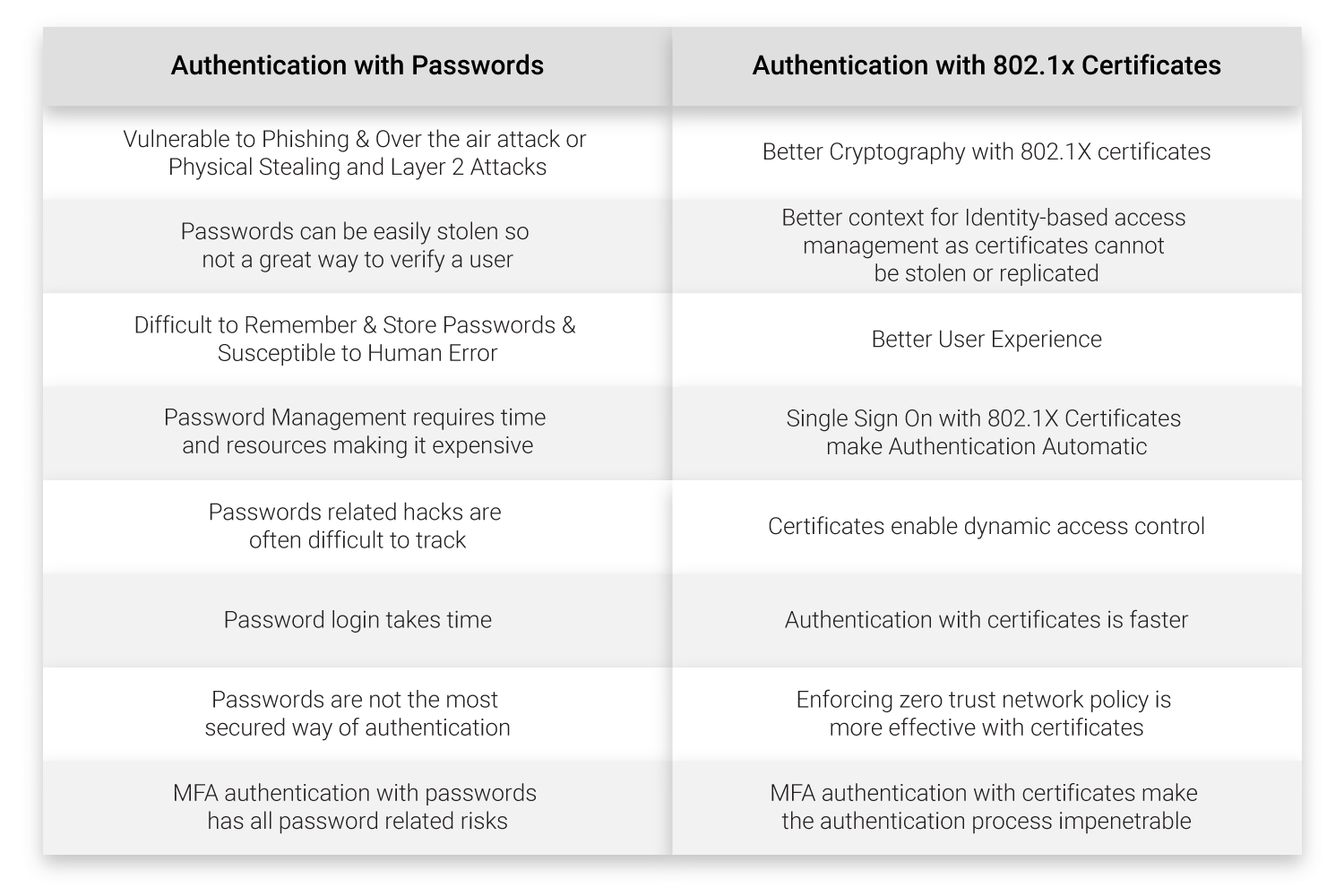
Azure Conditional Access with Azure Certificate-Based Authentication
Azure AD conditional access, when implemented with an 802.1X digital certificate, can eliminate the vulnerabilities of password-based authentication and make MFA authentication more secure. The use of certificates with Azure Conditional Access can be done in two ways.
- For an on-premise environment, 802.1X certificates can be used by syncing it with an LDAP server
- Using Azure AD to issue certificates by creating a SAML application in Azure Portal.
Enabling Certificate Enrollment for Azure AD with SecureW2
At SecureW2, we provide a platform for organizations of any size to implement passwordless network security based on Azure AD with the use of 802.1X certificates. Our JoinNow Connector PKI was built to seamlessly manage the entire certificate lifecycle, from issuance to revocation, and will eliminate the security vulnerabilities that are attached to the use of passwords for authentication.
Our solutions help you with a varied list of features that can be used with Azure AD conditional Access that include but are not limited to Azure MFA auth, Intune auto revocation, and Windows Hello for Business login. Talk to our team of experts to know more.