
Configuring RADIUS with Azure AD
In a bid to keep up with the rapid expansion of cloud computing, Microsoft rolled out Azure AD so their clients are able to migrate their AD-domain environments to the cloud. Cloud-based solutions are on the rise because of improved security measures, reduced costs, and increased versatility compared to on-prem solutions.
While Azure AD is designed for controlling user access to the network and web app SSO, it doesn’t integrate with RADIUS servers natively, making the transition from on-prem Active Directories difficult for those using 802.1x Wi-Fi.
With Active Directory, it was simple to set up 802.1x. Your Active Directory credentials could be entered in clients, and users could start authenticating against the RADIUS. Sure, it was difficult for a lot of users, and would leave users vulnerable to MITM attacks, but at least it was straightforward and worked. With Azure AD, it seemed there was no easy solution like there was for on-premise AD.
Luckily, there is a RADIUS solution for Azure AD that is cloud-based, takes less time to implement, is more secure, allows you to switch from passwords to certificates, and it’s a fraction of the cost! SecureW2’s PKI services provide gateway APIs, allowing you to enroll Intune managed devices for certificates automatically. In addition, our RADIUS solution is simple to set up, take it from one of our customers.
Below we’ll show you how to set up your Azure AD network for 802.1x RADIUS authentication, which isn’t that hard to do.
How to Configure RADIUS 802.1x Authentication with Azure AD
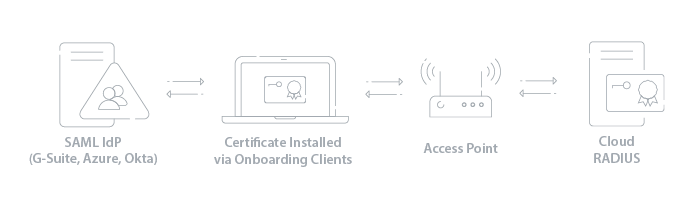
For this setup, we are going to use Cloud RADIUS so we can utilize EAP-TLS and authenticate with x.509 digital certificates. This will not only give us the best Wi-Fi security possible, but it will also give us the most flexibility in terms of what infrastructure we can integrate with. Certificates can seem difficult to set up, but Public Key Infrastructures (PKI) can actually be set up in a matter of hours if you use a Managed PKI like the one Cloud RADIUS comes with.
Integrate a PKI with your RADIUS
Integrating a PKI involves generating a Root and Intermediate CA used for issuing and managing certificates, and importing it into the RADIUS server’s trust list. These CA’s will contain our Certificate Revocation Lists (CRLs) which tell the RADIUS server who’s certificates aren’t allowed access. We don’t have to worry about setting this all up however, as Cloud RADIUS comes out the box integrated with SecureW2’s industry-renowned Managed PKI.
Microsoft offers their own way to handle certificates with AD CS, but it pales in comparison to cloud solutions because of its required on-prem connection. The on-prem hardware restricts AD-domain environments from seamlessly transitioning to the cloud because their programming is just not made for cloud migration.
Configure Policies on RADIUS
First the authentication policy needs to be configured on the RADIUS. This policy specifies the type of protocol that the authenticating user is requesting access through. In this situation, it only authenticates the EAP-TLS requests. After the RADIUS confirms the authentication request, the authorization process starts.
After completing the authentication process, users begin the authorization process to be authorized for network access. If they have a valid certificate and are approved for network use, they can connect to the network. This connection process can be as simple as Access_Accept-ing all approved users, or segmenting them based on an organization’s role policies.
Again, given the luxury of Cloud RADIUS already being configured for EAP-TLS certificate-based authentication, we don’t have to worry about setting this up.
Configure Azure as IdP
Azure can be configured as the IdP for Cloud RADIUS to authenticate against when a device is requesting network access. Once all end user devices are issued with certificates, Cloud RADIUS will be able to verify approved users and grant them network access.
Managing 802.1x Authentication with Azure
Deploying a certificate-based network makes it much easier for organizations to transition their environments to the cloud. However, many people are turned away because they believe certificates are too complex. Cloud RADIUS comes with all the software you need to seamlessly use Azure AD for 802.1x authentication and management.
Automated Authentication with Identity Lookup
Identity Lookup allows the RADIUS server to check the status of the user in the organization to ensure that only users active in the organization are authorized for network access. This is an awesome security feature, and it’s exclusivity to AD and LDAP environments made it one of the reasons why organization’s were hesitant to move to the cloud. But times have changed, as technology like Cloud RADIUS allows you to perform Identity Lookup with SAML-based Identity Providers.
With our intuitive management portal, it’s really easy to gain visibility into your network traffic. Not only does certificate-based authentication put a name to every network connection, but you can also gain access to all the onboarding and authentication logs all in our management portal. You can even grant lower level IT admins the visibility they need to troubleshoot authentication and onboarding issues. Organizations often reduce their Wi-Fi connectivity tickets by 30-50% when they switch to Cloud RADIUS, and it’s easy to see why
Integrate Azure AD with Cloud RADIUS for Better Network Management
Organizations are quickly adapting to cloud-based services for their environment, but Azure clients have trouble setting up 802.1x authentication. Fortunately, Azure clients can integrate their networks with Cloud RADIUS for better security and user experience. As mentioned before, Cloud RADIUS comes with SecureW2’s industry-leading onboarding software that streamlines device authentication and ensures your network stays protected from cyber attacks. Cloud RADIUS is also incredibly affordable, check out our pricing.




