
Using a RADIUS Server for Wi-Fi Security: 6 Best Practices
A RADIUS (Remote Authentication Dial-In User Service) server is one of the most important things you can use to keep your Wi-Fi safe and ensure that rules are followed. This dynamic server checks users’ passwords and makes setting up custom access rules easier.
When combined with digital certificates, it turns the login process for end users into one that doesn’t require a password but is still very safe. Using RADIUS and certificates together should make a strong and easy-to-use Wi-Fi security system, but administrators must consider some important things before setting it up.
This article will show administrators the best ways to set up a RADIUS server for Wi-Fi. We’ll explain what they need to think about and the steps they need to take to create a safe and effective login system.
What Is a RADIUS Server Used for?
RADIUS (Remote Authentication Dial-In User Service) is a networking protocol that provides users who connect to and use a network service with centralized authentication, authorization, and accounting management. RADIUS ensures secure access to wireless networks by validating the identities of users and devices before granting access. The capacity to handle user authentication and authorization substantially strengthens the security posture of a Wi-Fi network.
The RADIUS server configuration is of the utmost importance to establish a secure framework for Wi-Fi networks. Through accurate RADIUS server configuration, administrators can effectively manage user permissions, enforce stringent access control policies, and monitor network usage for auditing and invoicing. An appropriately configured RADIUS server enhances the network’s overall security by mitigating the likelihood of unauthorized entry and potential security violations.
Significantly, RADIUS servers are indispensable to the implementation of the 802.1X framework. 802.1X is a standard that ensures that only authenticated and authorized devices can connect to a network through port-based network access control. It increases security by mandating that users or devices provide authentication before granting access. Understanding the interdependent nature of RADIUS servers and the 802.1X framework is crucial for appreciating their critical contribution to protecting Wi-Fi environments.
What Is the AAA in RADIUS Server?
The AAA (Authentication, Authorization, and Accounting) server functions by a collection of guiding principles that guarantee regulated and secure entry to network resources. Verifying the identity of users and devices requesting access is known as authentication.
Authorization controls the degree of access that is allowed to verified entities. Accounting records the resources that users utilize while on the network. The operation of the AAA server serves as the foundation of secure network administration by implementing policies and protocols that protect the integrity of the network.
RADIUS servers are often considered an AAA server because of their built-in authentication, authorization, and accounting functionalities.
Compatibility of RADIUS Servers in the 802.1X Framework
On-premise RADIUS
Deploying an on-premise RADIUS infrastructure, often through Microsoft’s Network Policy Server (NPS), has been vital for organizations emphasizing detailed control over wireless network identification. However, this authentication is even stronger when organizations move past credential-based authentication.
When you use strong authentication methods like EAP/Protected Extensible Authentication Protocol (PEAP), users and NPS servers can verify each other using digital certificates. This stops names from being sent in plaintext and makes it harder for people who aren’t supposed to be there to get in. Using digital certificates requires a Public Key Infrastructure (PKI), and organizations have historically used on-premise PKIs through Active Directory Certificate Services (AD CS) to accomplish this.
On-premise RADIUS and PKI need special hardware, regular maintenance, and constant monitoring. To keep a system strong, administrators should follow best practices like carefully setting up event logging, ensuring that logs have enough space, and backing up regularly. This method is ideal for organizations with strict security requirements, providing a safe basis for Wi-Fi identification within their grounds.
Cloud RADIUS
In contrast, Cloud RADIUS is a versatile and expandable solution for enterprises aiming to capitalize on the advantages of cloud-based infrastructure. This technology can effectively control and verify network access from various locations, making it a suitable option for enterprises with dispersed workforces and remote access.
Cloud RADIUS solutions, exemplified as SecureW2’s Cloud RADIUS, provide a streamlined approach to implementation and upkeep, allowing enterprises to prioritize their fundamental business activities without requiring substantial hardware or infrastructure expenditures. A cloud-based approach enables smooth incorporation with different Identity Providers (IDPs) and offers improved scalability to adapt to changing business requirements.
Cloud RADIUS provides a quicker deployment and administration procedure that eliminates the need for large hardware infrastructure and specialized IT workers. Its features for seamless interaction with multiple cloud-based Identity Providers (IDPs) provide effective access control across varied user bases, supporting dynamic and adaptive network security.
Cloud RADIUS’s increased scalability enables organizations to meet expanding user needs and quickly react to changing business situations. However, dependence on third-party cloud infrastructure creates concerns about data security and compliance with industry-specific rules, requiring organizations to evaluate their selected cloud service provider’s security measures and regulatory adherence.
Challenges of Setting Up NPS With Azure AD
Setting up NPS with Azure AD poses several problems that administrators often need help with. These difficulties originate from the extensive technical requirements of merging the two systems, such as providing flawless attribute mapping, maintaining network connection, and properly handling certificates.
Even simple configuration errors might result in authentication failures, exposing the network to security risks. The distinct authentication processes of NPS and Azure AD may lead to problems, resulting in a fragmented security environment that makes access control more difficult.
Furthermore, synchronizing on-premise infrastructure with a cloud-based service like Azure AD requires careful consideration of protocol compatibility and data encryption, necessitating a proactive security management strategy.
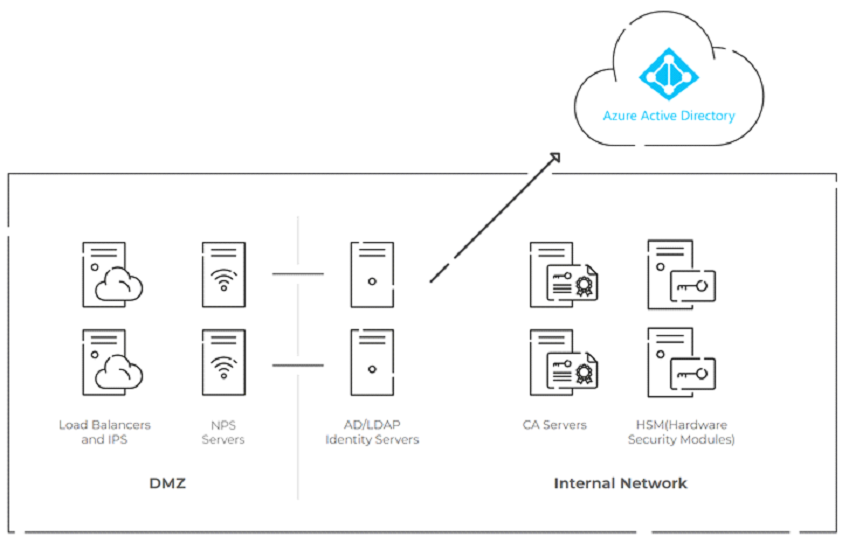
NOTE – The diagram above displays a complicated self-managed RADIUS architecture that integrates on-premise NPS, cloud-based Azure AD, and digital certificates for passwordless authentication, requiring a DMZ for security, PKI/CAs, and HSMs, potentially resulting in operational difficulties and high costs.
Cloud RADIUS, rather than just being a connection tool, is a full replacement for NPS, employing digital certificates to provide passwordless authentication. These certificates transmit just their public keys, making them immune to credential theft and improving overall network security by complying with the Zero Trust Network Security principles. Accepting such a transition implies significant modifications in network authentication approaches, emphasizing the critical necessity of strong security mechanisms and adaptive authentication methods in current cloud-based systems.
The seamless integration of Cloud RADIUS with Azure AD provides a significant benefit, boosting both security and user experience by utilizing existing policies inside Azure Active Directory. The real-time user lookup tool, together with the tight interaction with Azure AD, guarantees that only authorized users may access the network, bolstering the overall security posture of the system.
Cloud RADIUS also integrates Mobile Device Management (MDM) gateways and a robust access policy engine designed specifically for Azure Active Directory, aligning with current best practices for network security and simplifying the deployment of certificate-based security, facilitating a secure and seamless transition to cloud-based authentication solutions.
Cloud RADIUS from SecureW2 includes the necessary components of Public Key Infrastructure (PKI), comprehensive onboarding solutions for Mobile Device Management (MDM) and Bring Your Own Device (BYOD) scenarios and a fully functional RADIUS server for the seamless implementation of certificate-based authentication. This comprehensive method enables a secure and compliant cloud migration, satisfying current network security requirements while simplifying the installation of certificate-based security mechanisms.
Best Practices for Configuring RADIUS Server for Wi-Fi
Tie Your Existing Cloud Identity Infrastructure to Your Wi-Fi
Organizations everywhere use various identity platforms to categorize and maintain policies related to groups of users. These policies don’t need to be only linked to specific cloud applications; they can also be tied directly to your Wi-Fi login with the right RADIUS solutions.
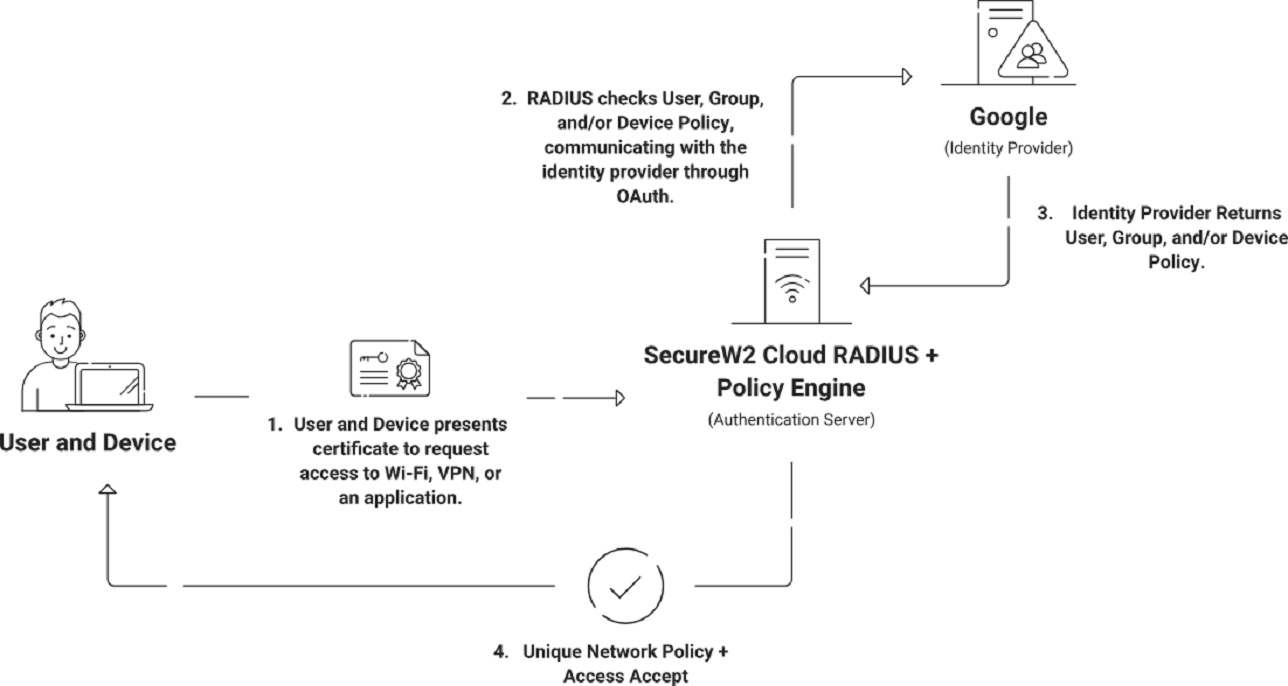
Integrating the RADIUS server with major Identity Providers (IDPs) like Azure AD is critical for building a strong authentication architecture. Organizations can speed up the user authentication process and implement tight access control rules by using the authentication features of these prominent IDPs. Integrating seamlessly with Azure offers effective user management, ensuring only qualified individuals are on the network. This connection also enables a centralized approach to identity management, simplifying the administration of user credentials and improving the network’s overall security posture.
Build Detailed Wi-Fi Access Policies
Setting up thorough Wi-Fi access policies is one of the most important practices for managing a RADIUS server. This gives you more control over who can connect and makes the network safer. Organizations can simultaneously use SecureW2’s Cloud RADIUS authentication service to check x.509 digital certificates and user, group, and device details in their Identity Provider (IDP) during the authentication process. Dynamic access control is possible with this interface. Network Policies decide what factors, like Time of Day, NAS-ID, User Roles, and more, can allow or refuse network access.
One common use for these policies is putting people into different VLANs based on which groups they belong to. For instance, organizations can give teachers and students different Wi-Fi access by setting up different user jobs and linking them to different VLANs.
Administrators can configure settings for SecureW2’s Network Policies based on many factors, such as RADIUS Client, User, Device Roles, device information, and even Time of Day. This level of detail lets organizations change their Wi-Fi access rules to fit their needs, ensuring users have a safe and personalized experience. Managers can easily set up and manage these rules through Cloud RADIUS. This makes their Wi-Fi networks safer overall.
Leverage Cloud Identity Infrastructure in Real-Time During Authentication
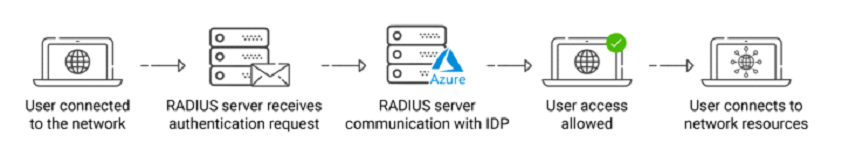
The RADIUS lookup process consists of several high-level processes that work together to enable safe and efficient user authentication throughout the network. Initially, the user attempts to connect to the network, which results in a request for authentication from the RADIUS server.
The RADIUS server communicates with the relevant IDP, such as Azure or Okta, to validate the user’s credentials and permissions. Following successful authentication, the RADIUS server allows the user access, allowing them to connect to network resources safely. This emphasizes the significance of a properly configured RADIUS server and its seamless interaction with main IDPs for a smooth and safe authentication procedure.
Understand Authentication Protocols During RADIUS Configuration
When setting up RADIUS, the different authentication methods are very important for ensuring users can access and protect data safely in network settings. These methods include several ways to verify the identity of people and devices wanting to connect to the network. Each has its pros and cons.
Some common authentication methods are EAP (Extensible Authentication Protocol), PAP (Password Authentication Protocol), and CHAP (Challenge-Handshake Authentication Protocol). PAP is an old authentication system that sends user details in clear text, meaning they can be intercepted and used by people who aren’t authorized to do so.
Even though CHAP is safer than PAP, it still has some problems, such as the fact that data sent over it is only partially encrypted and could be replayed. EAP, on the other hand, provides a framework for different identification methods, making it a more complete and flexible way to protect networks. Different authentication methods can be used with EAP, such as EAP-TLS, EAP-TTLS, and PEAP. This lets different security needs and infrastructure limitations be met.
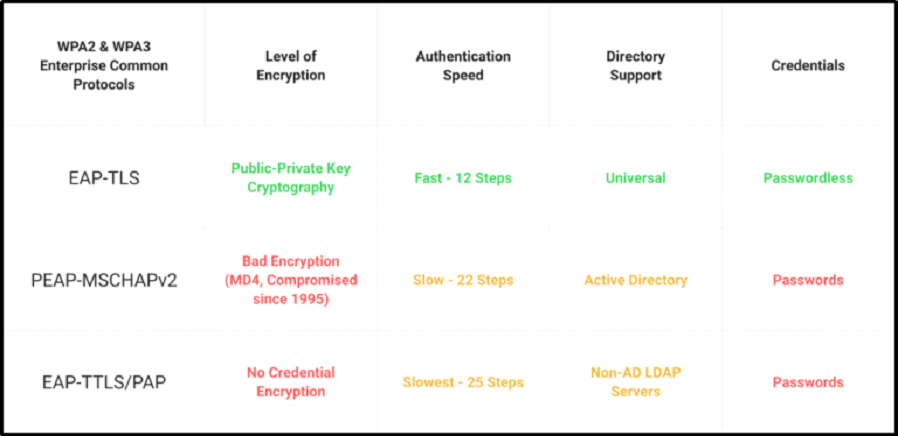
Due to its strong security measures and reliance on digital certificates, EAP-TLS is becoming more prevalent in cloud settings. EAP-TLS, built on the TLS protocol, uses digital certificates to ensure safe contact between the user and the network.
Unlike traditional methods that use passwords, EAP-TLS eliminates the problems of people stealing passwords and trying to get in without permission. EAP-TLS improves data security and stability by using digital certificates. This helps organizations lower the risks of unauthorized access and possible security breaches in the cloud. Using EAP-TLS in RADIUS configurations makes the authentication process safer and more reliable. This aligns with current security standards and shows how important strong authentication methods are for protecting private data and network resources.
Configure MAC Authentication Bypass for Devices That Can’t Support Certificates
When specific devices cannot support digital certificates, administrators can employ MAC Authentication Bypass as a recommended course of action. By enabling devices to establish connections to the Wi-Fi network using their MAC addresses, this approach provides an alternative means of authentication for users unable to employ certificates.
The configuration process for MAC Authentication Bypass in SecureW2’s management portal is uncomplicated. Administrators can enable this feature for particular user groups or devices, establishing a secure and accessible network environment by associating MAC addresses with authorized users.
SecureW2’s Cloud RADIUS mitigates the security risks associated with password-based authentication by prioritizing network authentication based on certificates. Certificates eliminate the possibility of credential theft by transmitting the public key exclusively over the air.
By providing passwordless authentication, Cloud RADIUS frees organizations from the constraints imposed by LDAP and Active Directory. It provides real-time user retrieval capabilities and native integration with key identity providers, enabling ultra-secure network authentication by contemporary security standards.
Cloud RADIUS ensures Zero Trust Network Security by furnishing device and user context via digital certificates. It also incorporates an industry-unique access policy engine specifically engineered for Azure, Okta, and G-Suite. This solution is a dependable option for organizations that place a premium on strong security protocols, as it facilitates network authentication through self-service setup software and a single-pane management interface.
Understand Where and How to Review RADIUS Event Logs
Monitoring and efficiently reviewing RADIUS events logs is an essential best practice for ensuring a secure and operational network authentication system. Logs of RADIUS events offer significant insights into enforcing policies, user authentication attempts, and potential security incidents. Administrators must comprehensively understand the location and procedure for scrutinizing these records to expeditiously detect and resolve any irregularities.
Using SecureW2’s Cloud RADIUS streamlines the procedure for retrieving and understanding RADIUS event logs. The portal provides a centralized interface through which administrators can easily examine and assess records, thereby obtaining insight into events about policies, authentication successes, and failures.
By adopting this streamlined methodology, administrators can elevate the overall network security posture and proactively mitigate potential risks. The event log functionalities of Cloud RADIUS make a valuable contribution to a holistic security strategy by furnishing the requisite transparency and insights to facilitate an informed and adaptable reaction to ever-changing network challenges.
Strengthening Wireless Security Through Robust RADIUS Configuration
A strong RADIUS server setup ensures quick and safe network identification. This setup authenticates users to Wi-Fi networks and lets different rules be used, like separating users into different VLANs to divide the network better.
Adding digital certificates to this framework for identification allows organizations to provide access without a password. This strengthens their defenses against possible breaches and makes connecting easier for users.
SecureW2’s Cloud RADIUS stands out as a system made just for Wi-Fi security. Along with its Public Key Infrastructure (PKI), Cloud RADIUS makes it easy to log in without a password, which aligns with current security standards.
This method was made to ensure that businesses can improve their networks’ security and make it easier for users to connect to Wi-Fi networks. With Cloud RADIUS, organizations can make rules that fit their specific needs. This makes it useful for making Wi-Fi login processes safer and more efficient.
Contact us now to improve network security and streamline your authentication framework.