How to View RADIUS Event Logs
What is a RADIUS event log?
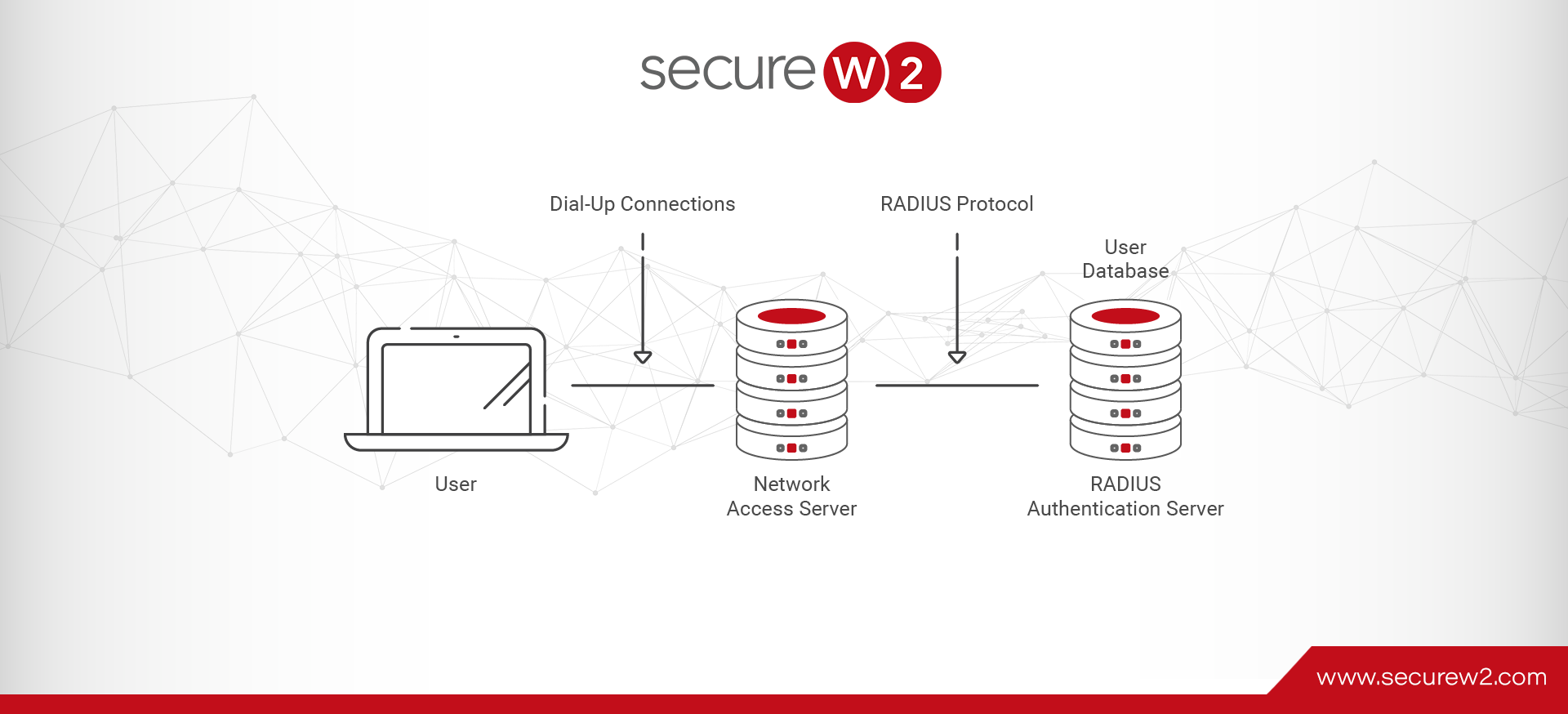
A RADIUS server is responsible for Authorization and Accounting in addition to its primary role of Authentication, hence its alternate name: “AAA server”. Given the importance of these tasks, it should come as no surprise that a RADIUS server is typically configured to log and store a record of all the requests it receives.
RADIUS event logs may be used for:
- Compliance audits
- Troubleshooting authentication issues
- Troubleshooting VPN issues
- Tracking use
- Tracking users
- Tracking devices
And more! RADIUS event logs are a powerful tool for managing your 802.1x network and users.
What information is included in a RADIUS Log?
The data contained within a RADIUS event log varies from RADIUS to RADIUS, but there are some common fields that you’re likely to find no matter your RADIUS provider.
- Date
- Time
- Name
- Client Type
- Record Type
- Authentication Type
RADIUS vendors with a robust management and reporting suite, like our own SecureW2 Cloud RADIUS, have the ability to add and remove data fields from event logs. Custom RADIUS event logs can be particularly useful for compliance audits.
In addition to event logs for authentication and authorization requests, RADIUS servers usually also log other event types like server startups, shutdowns, or interruptions of service. These make up a small fraction of the overall logs, but are particularly useful for investigating outages and the like.
How to view FreeRADIUS logs
FreeRADIUS is an open source framework for implementing your own DIY RADIUS. It requires a lot of technical expertise and hardware (or cloud server space) to configure and maintain, but it’s powerful and infinitely customizable.
During the configuration process for a FreeRADIUS server, admins are required to designate a folder for RADIUS event log output. FreeRADIUS doesn’t do anything with the logs, however, so you’ll need to manually process the raw data to a more human readable form if you plan to make extensive use of the logs.
How to view NPS logs
NPS is Microsoft’s pseudo-RADIUS that has seen widespread adoption due to its tight integration with the rest of the Microsoft environment. In particular, it plays well with Active Directory (AD), which is the IdP of choice for many organizations.
Viewing event logs generated by an NPS RADIUS is easy, if a little unintuitive. Rather than finding them in NPS, check the Windows Event Viewer (another system that’s part of the larger Windows Server package).
However, neither AD nor NPS have truly made the leap to the cloud. There are workarounds that allow you to use them in a limited capacity, but organizations that are using cloud directories like Google, Azure, or Okta should not use stopgap measures for network security. Limited support and antiquated systems leave your network vulnerable..
The best RADIUS event logging solution
Instead, use a built-for-cloud RADIUS like the aptly-named SecureW2 Cloud RADIUS. Not only has it been engineered for the ground up for cloud authentication, it also has an incredibly simple-yet-powerful management interface with unprecedented power over RADIUS event logging.
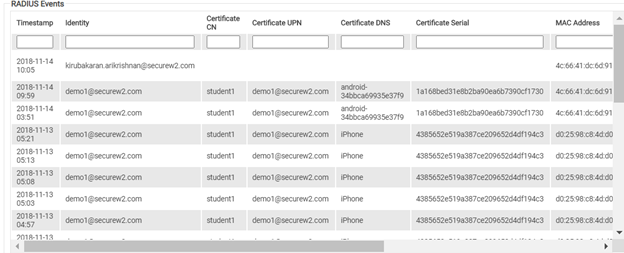
Unlike our competitors, our cloud PKI isn’t simply a layered directory with some added bells and whistles. It’s a full-featured PKI security suite that can integrate into your existing network infrastructure or be used as a turnkey solution.
But wait, there’s more! It comes with the industry’s #1 rated 802.1x onboarding software. So not only can you easily view RADIUS events, but you can easily see device connectivity issues and certificate enrollment status all in one place. No longer do admins need to manually scour through logs, everything needed to troubleshoot issues is available in our easy to use Cloud Management Portal.
Our Cloud RADIUS is powered by the Dynamic Policy Engine – a network access control solution that allows the RADIUS to interface directly with any cloud directory to confirm authorization requests. Instead of relying on insecure credentials or static certificates, you can make real-time policy decisions based on user attributes stored in the directory.
We have affordable solutions for organizations of every size. Check out our pricing page here.