Can I Use Azure With A RADIUS Server?
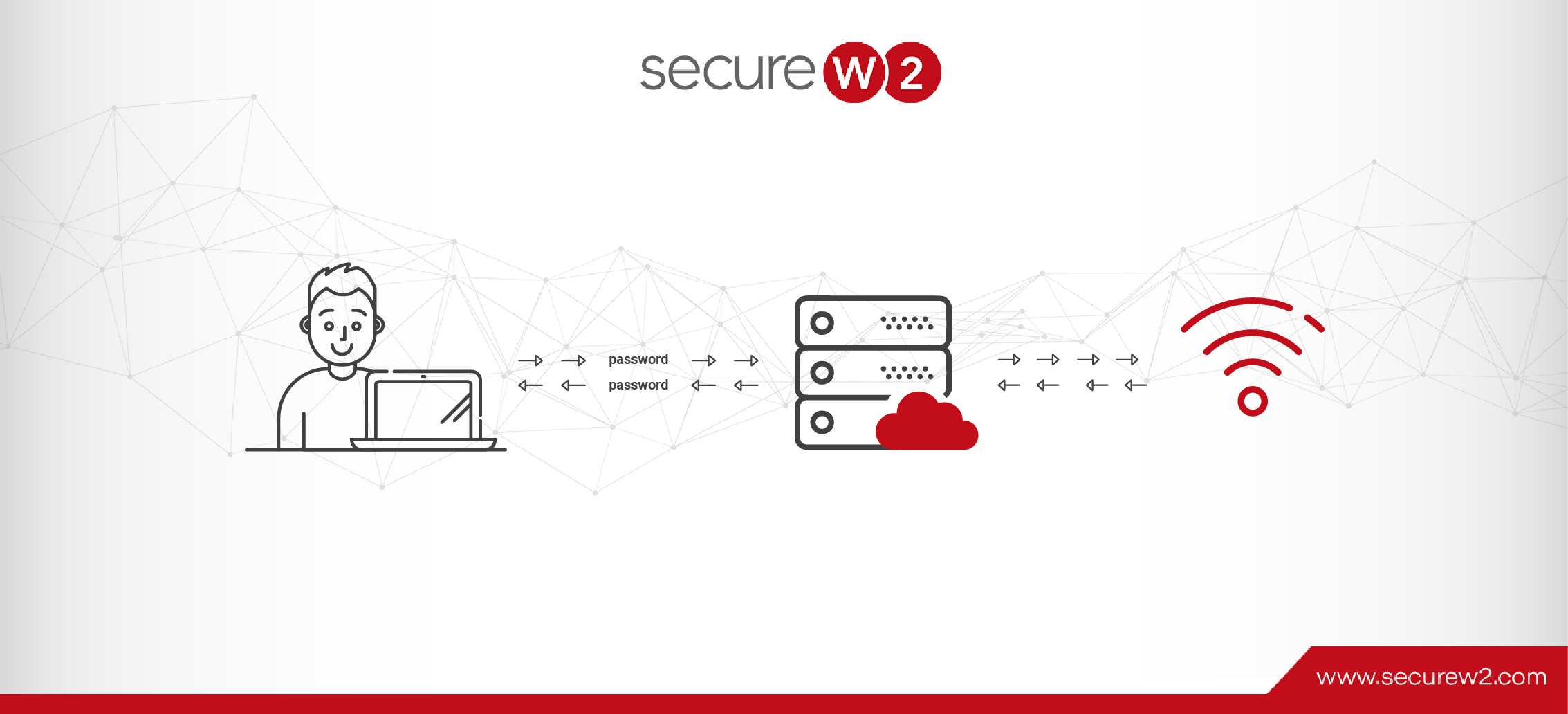
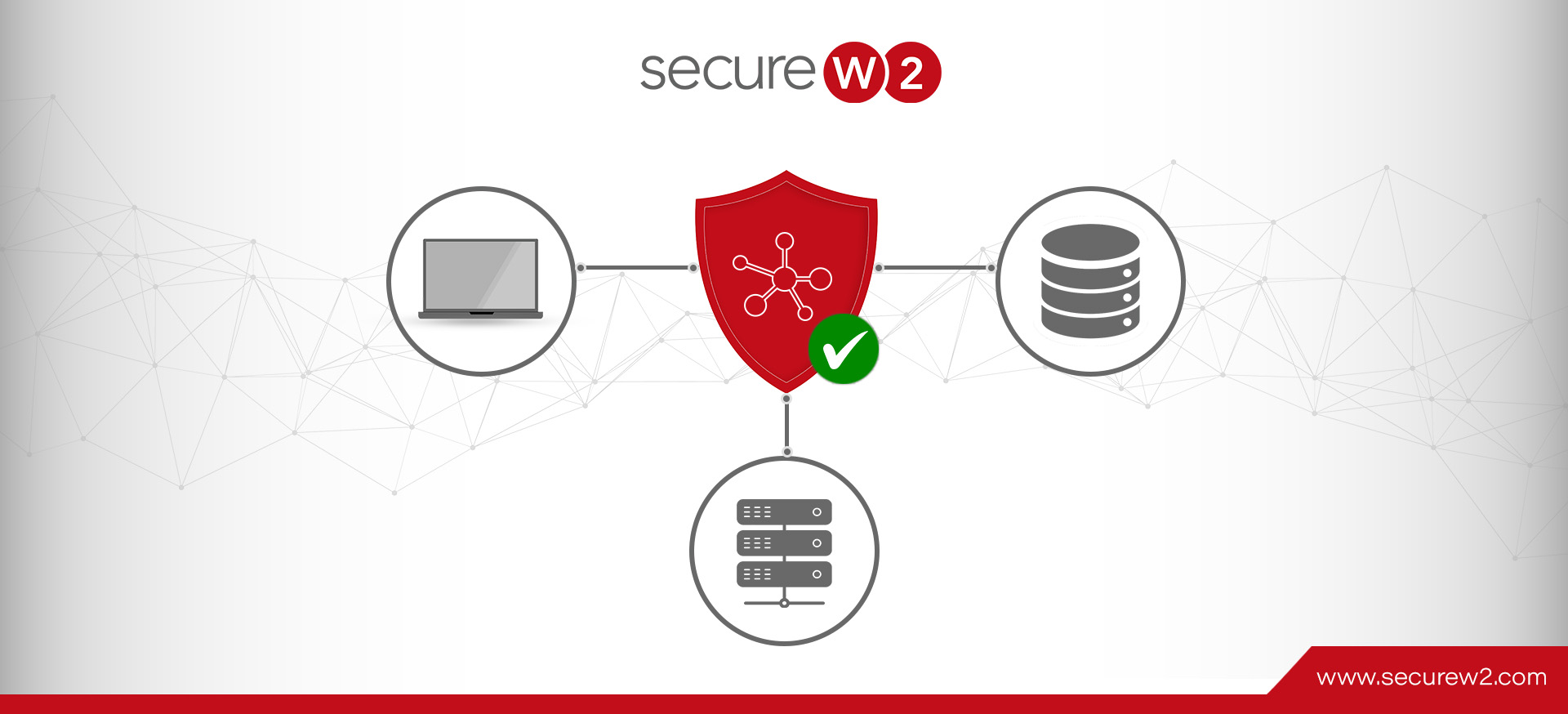
A RADIUS server is essential to network security since it is a gatekeeper, requiring user and device authentication before allowing access to wired networks, VPNs, or Wi-Fi. To carry out this function, an identity database, like Azure AD (Entra ID), one of the most popular cloud-based identity providers available today, must be connected to the […]
Read Story