
A Detailed Overview Of 802.1X Network Configuration
IEEE 802.1X
To deploy WPA in a wireless network, an access point uses 802.1X. A wireless client must be authenticated using WPA before it can establish a connection with the access point.
Switches use 802.1X to perform port-based authentication for wire-based networks.
WPA-PSK (pre-shared key, commonly known as WPA-Personal) and WPA/WPA2 Enterprise are the most popular settings for Wireless 802.1X. PSK is the most basic and weakest encryption method. The wireless access point is given a password, which is then shared with network users. The product’s target market is individuals using it in the comfort of their own homes. It can be broken with a simple brute force assault, and it’s vulnerable to any other popular attack method.
Applications of 802.1X range from centralized user authentication to protecting networks from cyberattacks to easing the process of introducing new network hardware. Formal education in networking is not required to set up devices that are 802.1X-compliant.
What is 802.1X?
The IEEE 802.1X protocol is an IEEE standard that facilitates port-based network access control (PNAC) on access points, both wired and wireless. The primary objective of 802.1X is to offer specific authentication limitations for every individual or equipment endeavoring to establish a connection with a LAN or WLAN.
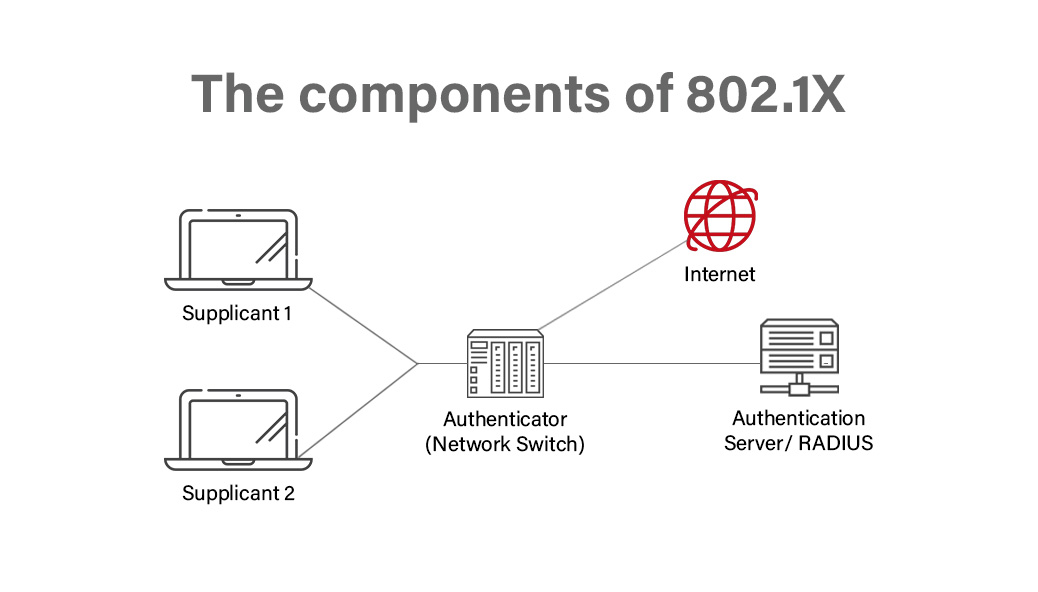
802.1X protocol triggers the network ports to ‘open’ for the user when the corporation validates their identity and approves their access. Then the verification of the user’s credentials or certificate is confirmed by the RADIUS server.
Finally, the RADIUS server and the organization’s directory establish a connection, often using LDAP or SAML protocol.
How Is 802.1X Used?
The IEEE standard 802.1X offers an authentication framework for wireless local area networks (WLANs). The 802.1X protocol leverages the Extensible Authentication Protocol (EAP) for message exchange during the authentication procedure.
The authentication server for 802.1X is commonly a RADIUS server that is compliant with EAP. It is capable of authenticating the client computer or the user using passwords or certificates. The authentication server provides a database of information required for authentication and informs the authenticator to deny or permit access to the supplicant.
Different Types of 802.1X Authentication
The authentication protocols that operate inside the 802.1X framework include EAP-Transport Layer Security (EAP-TLS), Protected EAP (PEAP), and EAP-Tunneled TLS (EAP-TTLS). These protocols allow the network to authenticate the client while also allowing the client to authenticate the network.
For more information, please refer to this WPA2-Enterprise Authentication Protocols Comparison.
The two EAP methods — Protected EAP (PEAP) and EAP-Tunneled TLS (EAP TTLS) — use a shared password for network authentication. The password may be a low-entropy one and may be drawn from some set of possible passwords, like a dictionary, which is available to an attacker.
For EAP-TLS, the end goal is simply to provide enhanced network security through digital authentication, i.e., certificates. Please click here to read more about EAP-TLS Certificate-Based Authentication.
Role of 802.1X in Network Security
When properly implemented, 802.1X is the most secure network authentication method presently accessible. The implementation of 802.1X network security when adding new devices to an existing network not only fortifies the network against potential cyber threats but also streamlines the process, saving valuable time, resources, and minimizing stress.
In order to establish connectivity with 802.1X-compliant equipment, no formal networking education is required. IT-friendly equipment possesses the capability to authenticate itself as a reliable hardware component on the network, thereby simplifying the setup process.
To establish network connectivity for your equipment, kindly contact the IT personnel and request for the 802.1X network access protocol that has been deployed, along with the present security certificate and/or password.
802.1X security is greatly influenced by the following factors:
- The device setup procedure is quite complex, and if performed by a non-IT user, it may pose a security threat. The methodology is intricate and can only be comprehended by an individual with significant proficiency in information technology.
- Whether the company uses certificate-based or credential-based authentication. The most secure implementation of 802.1X, certificate-based Extensible Authentication Protocol–Transport Layer Security (EAP-TLS), dramatically decreases the danger of credential theft for an enterprise.
Prerequisites for Windows RADIUS Server 2019
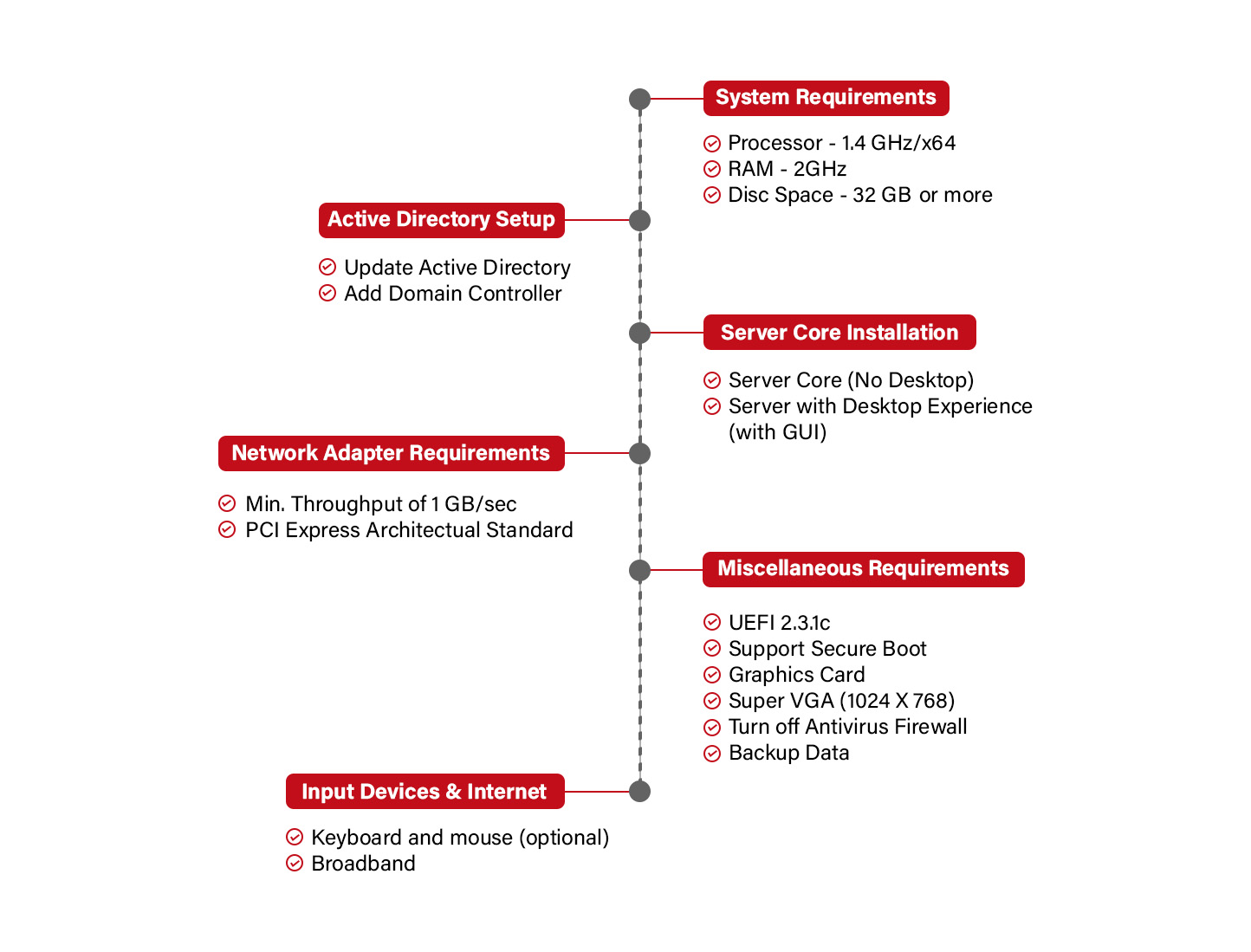
Steps to Configure Windows RADIUS Server 2019
Windows Server 2019 is the operating system that bridges on-premises and cloud environments.
Let’s dive deeper into each step involved in configuring Windows Server 2019:
Step 1: Install and Set Up Windows Server 2019
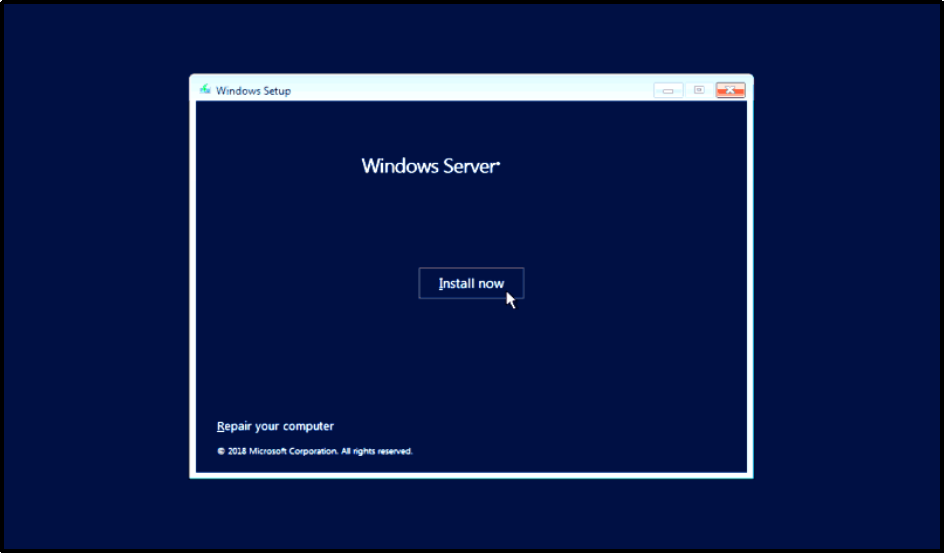
- Download Windows Server 2019 from Microsoft’s website.
- Accept license requirements and click Next.
- Select a language, time, currency, keyboard, and input method in Windows Setup. Click Next when finished.
- Click on Install Now.
- Choose the Windows Server 2019 edition to install.
- The server should reboot after the first configuration.
- The built-in Administrator account password will be requested. Click on Finish.
- The server should reboot after the first configuration.
- The built-in Administrator account password is requested and updated. Continue with Finish.
- Access Windows Server 2019 desktop after a few seconds.
- Click Yes in the Network window on the right of the server desktop to allow network connection.
Installation of Windows Server 2019 is complete.
Step 2: Install and Configure Active Directory Domain Services (AD-DS)
- Open Windows Server 2019.
- Click Start.
- Click Server Manager.
- Navigate to Role Summary.
- Click Add Roles and Features.
- Select Role-based or Feature-based Installation.
- Navigate to the Before You Begin page and click Next.
- Go to Select Server Roles.
- Select Active Directory Domain Services.
- Navigate to the Select Server Roles page.
- Select the Active Directory Domain Services.
- Click Next.
- Click Install on Confirm Installation Selections.
- Navigate to the Installation Results page and click Close.
Installation of AD-DS is complete.
Step 3: Install AD-CS, NPS, and IIS
For configuring AD-CS, Click Here; for NPS, Click Here; and for IIS, Click Here
Note: A certificate-based network requires a variety of components to operate. The user must build trusted servers and certificate authorities (CA) to ensure that devices may enroll for certificates, authenticate users, manage the certificate life cycle, and segment users for various group rules.
Also, the installation of AD-CS must share the domain with the already installed AD-DS.
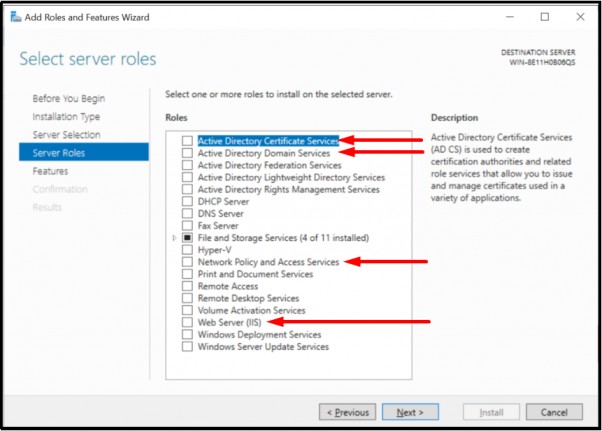
- Go to the Server Manager page.
- Click Add Roles after choosing Roles.
- On the page called “Before you Begin”, click Next.
- Select NPS and AD CS.
- Click on Next.
- Click on Next on NPS.
- Select NPS from the list of Role Services.
- Click on Next.
- Select Create a self-signed SSL certificate, then click Next.
- Click Next on the AD CS page.
- On the Select Role Services page, choose Certification Authority and click Next.
- On the Specify Setup Page, choose Enterprise and click Next.
- On the Specify CA Type page, choose Root CA and click Next.
- On the Set Up Private Key Page, click Create a new private key and hit Next.
- Click Next on Configure Cryptography for CA.
- Enter details on Configure CA Name page and click Next.
- On the Set Validity Period page, enter the time frame and click Next.
- On the page to configure the certificate database, click Next.
- On the Web Server (IIS) page, click Next.
- On the page Select Role Services, click Next.
- On the page that says Confirm Installation Choice, click Install.
- Close the window.
Installations of AD-CS, Web Server (IIS), and NPS are now complete.
Step 4: Configure NPS for RADIUS Authentication
The client computers and devices such as laptops, tablets, phones, and other machines running client operating systems, are not considered to be RADIUS clients.
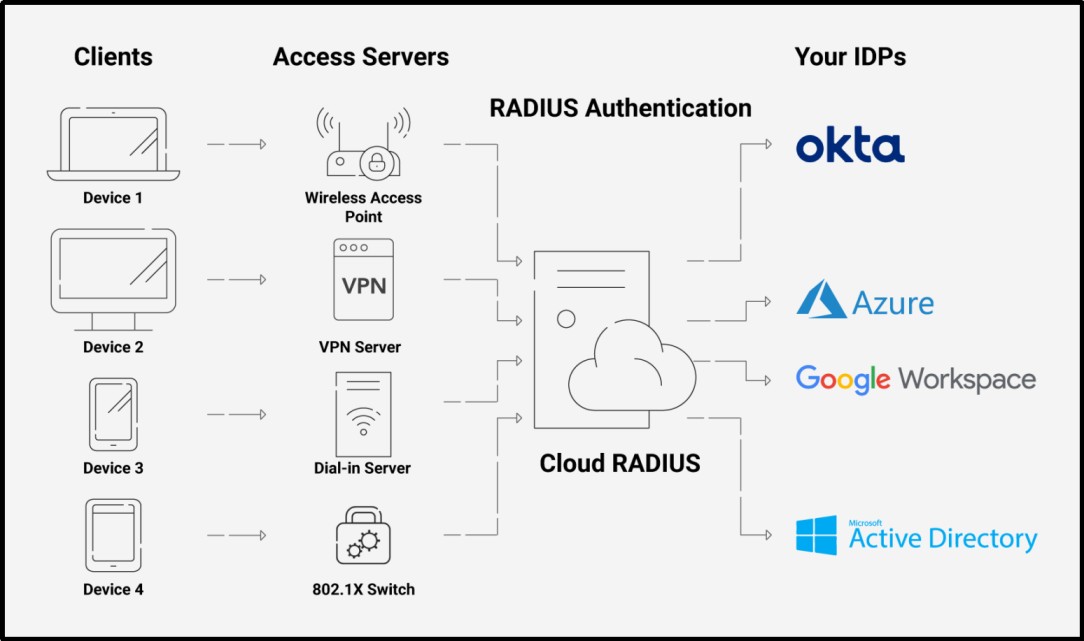
RADIUS clients are network access servers like wireless access points, switches that can handle 802.1X, virtual private network (VPN) servers, and dial-up servers. They use the RADIUS protocol to connect to network policy server (NPS) servers.

- Click Start and choose Administrative Tools.
- On the Network Policy Server, click the NPS button.
- Click OK after choosing Register Server in Active Directory.
- Select OK.
- On the NPS (Local) page, choose RADIUS server for 802.1X wireless or wired connections.
- Tap 802.1X.
- On the page for setting up 802.1X, choose Secure wireless connections.
- Enter ‘user’s name,’ then press the Next button.
- On the Configure 802.1X page, add RADIUS clients and click Next.
- On the New RADIUS Client page, type the following.
- Name IP Address Secret Kept in Common (Manual):
- Name
- IP Address
- Shared Secret (Manual)
- Click OK, then click Next.
- On the Configure 802.1X page, select Microsoft Protected EAP (PEAP).
- Tap Configure.
- On the Edit Protected EAP Properties page, choose Secured password and click Edit.
- Enter the number of authentication retries, then click OK and Next.
- Tap Groups and Click Next.
- Click Next once more, then click Finish.
- Restart NPS.
Step 5: Define Network Policies for Users/Devices
Using the Network Policy Wizard, a user can add new conditions, restrictions, and settings to the network policies.
- Go to the NPS console and press the NPS button (local).
- Click Policies and open them up.
- Network Policies can be chosen.
- Choose New.
- Type the name of a policy.
- Choose “Unspecified“ for the Type of Network Access Server when using Netscaler or “RCdevs OpenLDAP” when using OTP.
- Click Add under Specify Conditions.
- Click Add after selecting Windows Groups.
- Click Add Groups and then click OK.
- Choose NAS Identifier from the list of conditions.
- Enter a name, and then click Next to move on.
- Choose Access Granted in the Specify Access Permission section.
- For the most security, choose MS-CHAP v2 under Configure Authentication Method.
- Click on Next.
- In Configure Settings, choose Standard for RADIUS attributes.
- Click Add.
- Enter the attribute’s value in String, then click OK.
- Click Next, then click Finish.
Using our CloudRADIUS, administrators may establish and apply a wide variety of rules, including lookup policies implemented at the time of authentication.
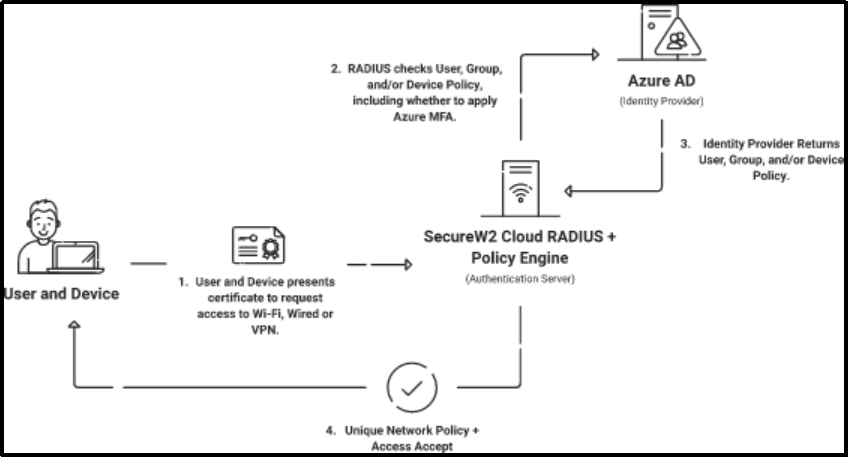
The phrase ‘selective access’ aptly elucidates one of many “must-haves” for the RADIUS-on-the-cloud. For instance, an admin may determine whether to allow or deny persons and devices based on the time of day or wish to limit access to devices running a specific operating system.
Step 6: Implement 802.1X Authentication for Zero Clients
Refer to the steps below to implement 802.1X Authentication for Zero Clients:
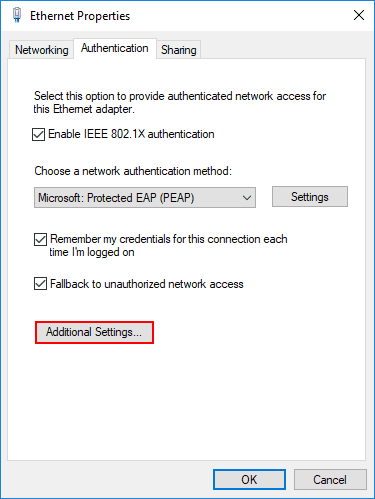
- Open the Network and Sharing Center by hovering over the Control Panel and clicking on it.
- Click Change Adapter Settings.
- Tap Properties and then click on Local Area Connection.
- Choose Authentication and click Enable IEEE 802.1X authentication.
- Choose the protocol from the dropdown menu.
Step 7: Configure Wireless Connection Request
- Open the Network and Sharing Center by hovering over the Control Panel and clicking on it.
- Click on Manage Wireless Networks.
- Choose Manually Create a network profile.
- In Network Name, type in the SSID and click Next. Click on Change Connection Settings.
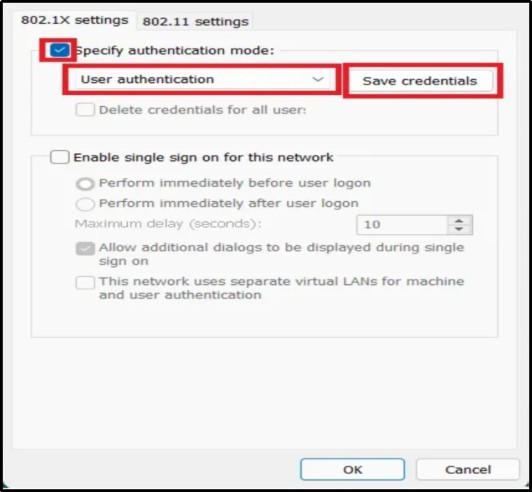
- Click on Settings and then on Security. Click OK after choosing the Trusted Root CA.
- Go to Settings > Advanced.
- Click OK after choosing “Specify Authentication Mode.”
Non-Cloud Compliance of Windows RADIUS Servers
Neither the Network Policy Server (NPS) nor Active Directory (AD) was conceived with cloud-based network authentication in mind. Using what has historically been an on-premise RADIUS solution to manage cloud-based resources would need a large investment in both IT man-hours and network infrastructure. We have found this to be a major challenge for businesses looking to migrate Active Directory to Azure while maintaining 802.1X compatibility. Setting up and overseeing such pursuits is difficult; they also take up a lot of time and money.
In order to host NPS in the cloud, you need to combine Windows NPS as a RADIUS proxy with a cloud-based RADIUS solution.
A user would send their authentication request to the cloud RADIUS, and in turn, it would be forwarded to NPS for final authentication. This process requires a specific configuration of RADIUS policies to match NPS.
Once configured, users would send their authentication requests to the cloud-based RADIUS and they would be authenticated securely with Microsoft NPS.
In addition, due to its physical accessibility, the NPS server on-premises is susceptible to various physical security concerns, including attackers, natural catastrophes, and even power outages.
Furthermore, the expenses of securing physical locations’ on-premises RADIUS are seldom less expensive than Cloud RADIUS.
Modern Cloud 802.1X: Cloud RADIUS
Cloud computing fosters a proactive and creative approach, two traits crucial to success in today’s competitive environment. Cloud computing does so by enabling rapid file access, more straightforward data analysis, and better security.
A 2020 Centrify and CensusWide survey revealed that before March 2020, 43% of companies surveyed had no intention to migrate to the cloud entirely. In a turn of events, pre-pandemic and post-pandemic statistics show that 48% are streamlining their cloud migration plans due to the COVID-19 pandemic, while 36% want digitization using cloud technology.
Hence, experts believe the upcoming years will see many corporate migrations to cloud-based services.
Security storage on the cloud makes it convenient for employees to access work systems, platforms, and data from any location. Cloud computing also enables businesses to reduce their extensive IT spending.
For years, network managers depended on Windows Server for network authentication, but with recent technological breakthroughs, it is impossible to overlook its flaws.
Moving to the cloud has significant advantages over remaining in an on-premises system, and no solution demonstrates those advantages better than our groundbreaking Cloud RADIUS. By implementing a cloud-based NAC such as SecureW2’s Cloud RADIUS, the admin may circumvent the shortcomings of on-premise authentication. We have affordable options for organizations of every size. Click here to see our pricing.




