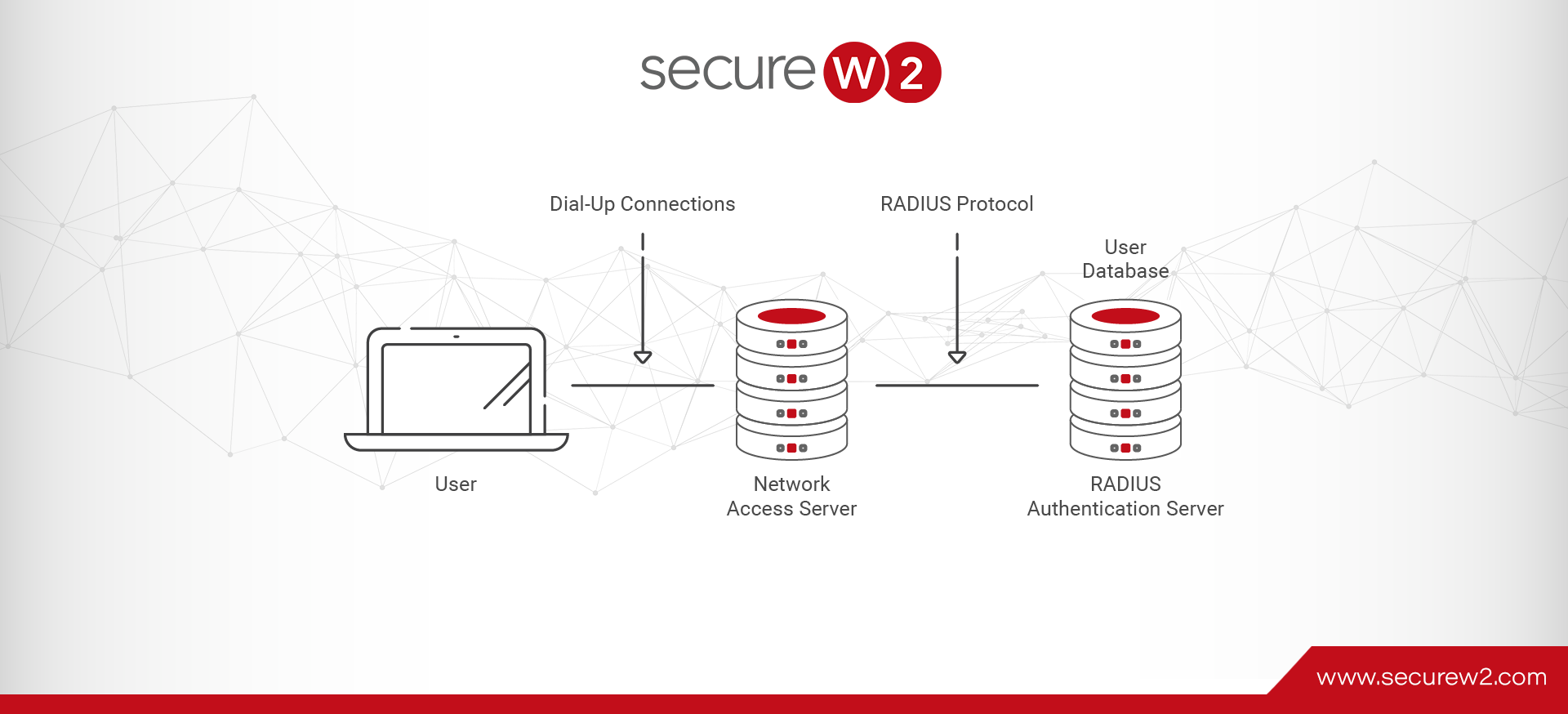
SecureW2’s Cloud RADIUS vs. JumpCloud’s RADIUS
Maintaining a secure RADIUS Server is paramount to network security and ensuring only approved users are able to connect. While there are many RADIUS options available, the general consensus in network security is that cloud RADIUS setups are superior to on-premise servers.
A cloud RADIUS requires less maintenance overtime and offers greater cost savings. But there are many cloud vendors that vary in what they offer to customers. So we have taken time to compare two reputable RADIUS options: SecureW2’s Cloud RADIUS and JumpCloud RADIUS.
End User Experience
JumpCloud
While configuring for RADIUS authentication is a process for end users, it is not particularly difficult to complete, especially if provided a configuration guide. But it is still an extra step in the process and can lead to misconfigurations or support ticket requests. Normally this would be fine, but misconfigurations make users vulnerable to Man-in-the-Middle attacks. According to IBM’s X-Force Threat Intelligence Index, 35% of exploitation activity involves Man-in-the-Middle Attacks.
To authenticate to JumpCloud RADIUS, end users must provide credentials in the form of a username and password. There are countless security vulnerabilities that credentials cause, and overall, they are not a strong method of authentication security, but we will focus on the user experience.
To authenticate with credentials, the user must manually enter their username and password to connect. The manual entry process is cumbersome, but not nearly as bad as password reset policies. As an organization, you want to follow security best practices, but with credentials, this can be annoying.
Password reset policies require users to create a new password after a set amount of time, usually between 60 and 90 days. Frequently resetting your password and reconnecting every device is highly irritating and often leads to an uptick in IT support ticket requests. The InfoTech Research Group found that 40% of IT service desk volume is password related, with an annual cost of $118 per person spent on password resets. Additionally, you’d hope that users would follow password best practices by choosing a unique and complex password every time. Unfortunately, most users value convenience over security and opt for a password that is easy to remember or very similar to their expired password.
SecureW2 Cloud RADIUS
To be configured for RADIUS authentication, SecureW2 provides the JoinNow onboarding solution. The onboarding client can be completed by any user in a few minutes and guarantees accurate configuration for everyone. There are only a few simple steps, and in the end the user is equipped with a certificate for authentication.
Between the two most common authentication methods, certificates and credentials, certificates are far superior in every way. We will discuss the authentication security comparison in the next section, but from a user experience standpoint, certificates are much more user-friendly.
To authenticate with a certificate, the user has to do nothing other than be in the network’s proximity. The certificate is automatically authenticated when in range of the RADIUS and requires no interaction from the end user. Unlike credentials, certificates are not something that has to be memorized and it cannot be forgotten, lost, or stolen.
Certificate lifetimes are also significantly longer than passwords. While passwords have to be reset after a set time period, certificates are configured with an expiration date at the discretion of the organization. Certificate lifetimes can range from 1 to 20 years, depending on how the organization wants to operate. As a result, the typical end user experience with certificates is completing the onboarding client once and never again having to worry about authentication.
Authentication and Security
JumpCloud
JumpCloud relies on credential-based authentication and supports two authentication methods: EAP-TTLS/PAP and PEAP-MSCHAPv2. Now there are significant differences between EAP-TTLS/PAP and PEAP-MSCHAPv2 (which you can read about here), but we will focus on the overall differences between credential and certificate authentication.
The failings of passwords have become much more apparent as technologies and hacking methods continue to improve. Credentials are easily exploitable and vulnerable to a myriad of attacks. One of the most common ways credentials are overcome is through dictionary attacks that send thousands or millions of password requests until they finally get it right. If an attacker has the computing power, this is an easy attack to execute.
Another common attack method is to perform an Over-The-Air (OTA) attack, such as an Evil Twin attack. As credentials are sent through the air, attackers will attempt to intercept that communication and steal credentials for their use. JumpCloud enables certificate trust with their RADIUS, which protects against OTA attacks by requiring a user’s device to authenticate a server certificate. Unless they get confirmation of the validity of the server certificate, they will not send credentials through the air.
The greatest failing of credential security is that it relies heavily on the user to maintain security. In nearly every cybersecurity infrastructure configuration, the weakest link is the human component. People are prone to writing down their password, giving it to friends, or losing it through phishing attacks. By integrating people with cybersecurity, an organization creates a huge security blind spot that can be exploited.
SecureW2 Cloud RADIUS
Certificate authentication is the flagship of Cloud RADIUS. Once a user has completed the JoinNow client, their device is distributed a certificate. Unless you have a valid identity in the IDP, you cannot gain access.
Certificates require EAP-TLS authentication, which is far greater than other EAP methods because of public private key encryption. With this form of encryption enabled, your network is immune to all OTA attacks. If a bad actor intercepts a certificate in the air, it is unusable because they do not have the private key to decrypt it. While it is recommended to use server certificate validation to avoid sending credentials to a bad actor, there is a layer of protection against it.
Unless you are an approved network user, there are no options for gaining a valid certificate. They cannot be stolen over the air, transferred from a device, or discovered in a dictionary attack. And the authentication process requires no manual effort from the end user. Certificate-based authentication eliminates the human component from cybersecurity and replaces them with ironclad security measures.

RADIUS Configuration
JumpCloud
To configure the JumpCloud RADIUS, network administrators must configure within the management platform provided to them. The step-by-step process is spelled out for admins to follow with ease. They connect to the identity provider to give identity context (it’s recommended to use JumpCloud identity management).
The RADIUS is then connected to the wireless access points of the organization to direct authentication traffic to the right place. Then each client device must be manually configured to send identifying information to the RADIUS and connect to the network. This must be done by the IT staff or else the network is at high risk for Over-the-Air credential theft. And here is where admins can also provision network access at scale and restrict specific networks, VPNs, or applications to specific groups of employees. They can also segment through dynamic VLAN tagging. By segmenting the network, the organization is able to control access to certain materials and ensure every has access as needed.
SecureW2 Cloud RADIUS
Cloud RADIUS with SecureW2 is easily configured with the aid of a configuration guide and our white-glove deployment team. The solution is vendor-neutral and connects with identity management vendors, access points, and network infrastructure from every major vendor, with integration guides for nearly every vendor. The entire configuration process can be easily completed and ready to authenticate in a couple hours.
To configure client devices, end users can self-configure because of SecureW2’s super easy to use onboarding software clients. The end result of implementing the onboarding client is every user accurately configured for authentication. During this process, they are segmented into user groups that are designed by the admins. Based on their identity and role within the organization, they are granted access to certain applications, files, VPNs, etc., and are able to navigate the network with ease.
A secure RADIUS server is the gatekeeper to your network and a constant defender of your valuable data. Cloud RADIUS solutions offer the best user experience, cost less over time, and provide a greater range of security measures. There are many options available and some fit better in a particular network setup than others. Check out our pricing page to see if our Cloud RADIUS solution is right for your unique organization.