Passwordless RADIUS Authentication With Your Identity Provider
Credential-based authentication is the method nearly all businesses employ for their networks, as it has been the industry standard for decades. When setting up a WiFi network, it’s easy for businesses to set up an SSID and password and call it a day. But unfortunately, the inherent flaws and antiquities that come with passwords are rarely accounted for – often leaving networks with lackluster security.
Former employees, disgruntled workers, or hackers can leak out passwords and leave your entire network vulnerable to attacks. This can be disastrous for companies with sensitive information on their networks.
This begs the question: What are the alternatives to passwords?
What is Passwordless Authentication?
To be considered a worthy alternative to passwords, a system must swap the use of traditional alpha-numeric passwords with a more secure form of authentication. Passwordless authentication can take a number of different approaches, each of which has its own advantages, some examples being:
- Fingerprint Scan
- PIN
- Security Tokens
- Magic Links
- Certificates
- Any combination of the above.
Multi-Factor Authentication
Multi-factor authentication (MFA) requires 2 or more forms of identity for a user to be authenticated: something you know (a password), something you have (a Yubikey), or something you are (a fingerprint scan).
MFA has proven to be highly effective against preventing unwanted network access from unknown sources. With each added layer of complexity, it is exponentially more challenging for a malicious individual to gain access to your network.
Of course, added complexity works both ways. With more layers of authentication needed, there is bound to be more confusion for the user. MFA simply isn’t as scalable as other authentication methods, as the increase in authentication methods comes with an increase in potential errors.
Certificate-Based Authentication
The gold standard of passwordless authentication relies on x.509 digital certificates. A device equipped with a certificate is automatically authenticated when in range of the network and it cannot fall prey to any credential attacks thanks to public key cryptography. It’s more convenient for users and provides much stronger security to protect the network.
The key to using certificates effectively is an effective onboarding software. Allowing users to configure certificates manually is asking for a huge influx of IT support tickets. The process requires high level IT knowledge to comprehend; it’s simply an inefficient process when left to the user.
SecureW2’s JoinNow onboarding solution allows users to self-configure their devices in minutes with a few simple clicks. The user connects to the secure network, is prompted to prove their identity with their existing credentials, and then the JoinNow solution configures the device automatically and equips the user with a certificate that can be set to last for years.
With certificates, a user’s only interaction with the authentication process will be the initial configuration process. After that, they are always automatically authenticated and can browse without issue.
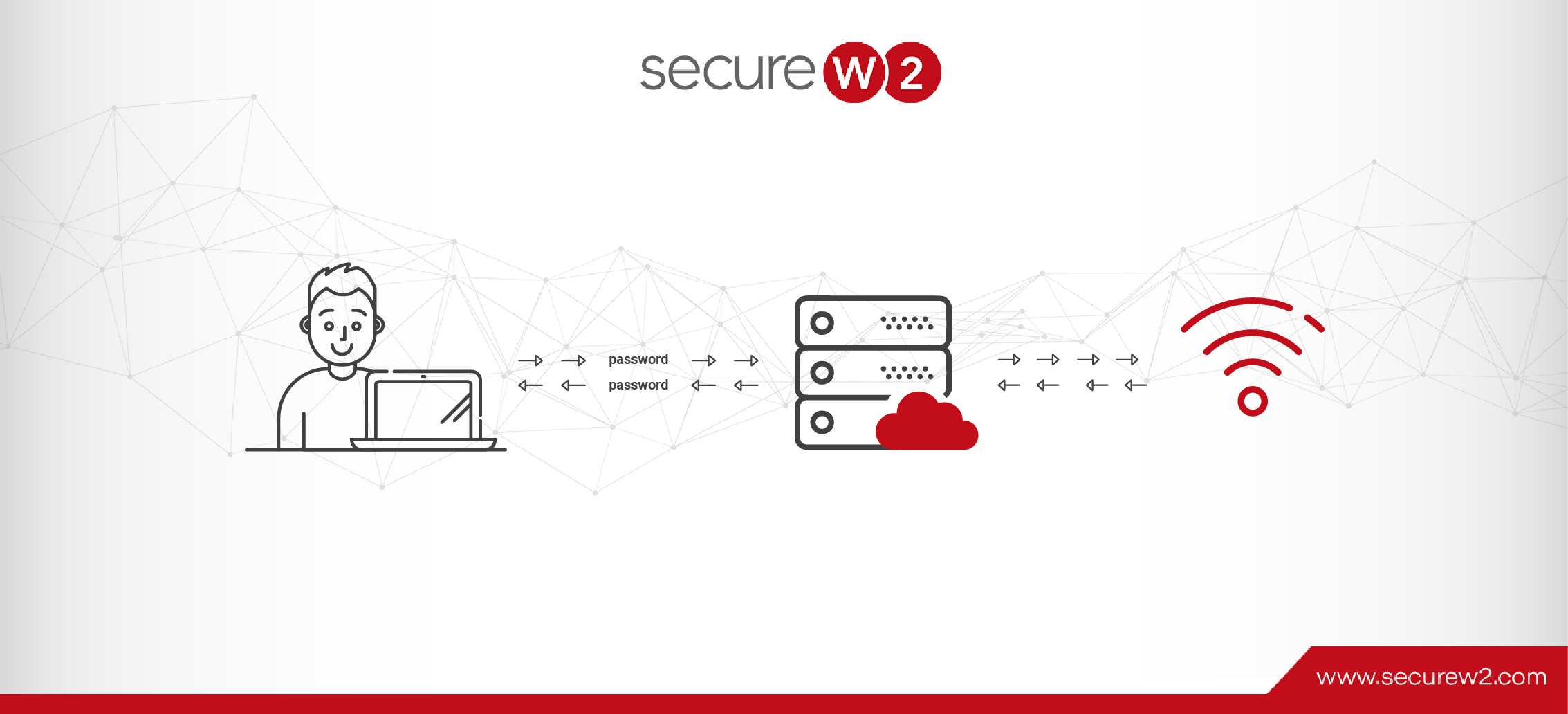
RADIUS Server Certificate Validation
In order to properly integrate certificates, a RADIUS server must be used to verify their legitimacy. A wireless RADIUS server uses a protocol called 802.1X, which governs the sequence of authentication-related messages that go between the user’s device, the wireless access point (AP), and the RADIUS server.
A key security mechanism to employ when using a RADIUS is server certificate validation. This takes the reliance on passwords for a RADIUS system and guarantees that the user only connects to the network they intend to by configuring their device to confirm the identity of the RADIUS by checking the server certificate. If the certificate is not the one which the device is looking for, it will not send a certificate or credentials for authentication. This prevents users from falling victim to an Evil Twin proxy attack.
Now, with our industry-first Dynamic Cloud Radius, you can even use certificates with cloud IDPs like Azure, Okta, and Google for passwordless authorization. It enhances certificate-based authentication by making an additional check in the user directory. Dynamic RADIUS can then make policy decisions based on user attributes stored in their directory, a method that reduces your reliance on certificate management.
RADIUS Authentication with SecureW2
With SecureW2, your organization can have a top-of-the-line RADIUS-backed network that is fully functional in a matter of hours. By removing the risks associated with password based authentication, your company will be on track for complete network security.
Our solution can integrate with any existing network infrastructure you might already have, including your IDP, to eliminate any headaches usually associated with integration. We have affordable solutions for organizations of all sizes; check out our pricing here to see if we can be of service.