NPS Cloud Integration Explained
Network Policy Servers (NPS) integration with cloud environments has become crucial for modern administrators. As organizations migrate more aspects of their infrastructure to the cloud, the issue of effectively integrating NPS into this dynamic framework has risen to the forefront. This article explores the realm of NPS cloud integration, illuminating the various options available to administrators attempting to bridge the divide between on-premise NPS systems and cloud-based services.
Administrators have these primary alternatives when integrating NPS with the cloud, each with its own benefits and drawbacks. The first option involves migrating NPS functions to cloud-hosted infrastructure, in line with the broader trend of decentralizing resources and increasing scalability. Alternately, an extension that enables NPS interaction with Active Directory (AD) in the cloud provides a path to seamless connectivity, although with considerations regarding compatibility and reliance on traditional AD components.
Throughout this analysis, we intend to shed light on the specifics of these options, providing insights into their pros and cons and guiding administrators toward decisions that align on-premise NPS capabilities with the limitless possibilities of the cloud.
Challenges of On-Premise NPS Servers
Despite the widespread use of Network Policy Servers (NPS) for this purpose, deploying them locally has many downsides. Here, we’ll discuss the unique restrictions and difficulties of using NPS servers inside an organization’s physical premises. These characteristics reduce the effectiveness of NPS implementations and create challenges for businesses, especially SMEs, when attempting to manage their network infrastructure efficiently.
- Complex installation process of NPS extensions
- Requirement of technical expertise for setup and maintenance
- Challenges faced by small and mid-size organizations
- Limitations and vulnerabilities of on-premise setups
Complex installation process of NPS extensions
The complex installation procedure for NPS extensions is a significant deficiency of on-premise NPS servers. These extensions are necessary for integrating NPS with cloud environments and maximizing the potential of cloud-based network access control. However, installation and configuration of these extensions frequently necessitate technical expertise and a comprehensive understanding of NPS architecture. This complexity can present difficulties for IT teams during the deployment phase, leading to potential delays and misconfigurations.
Requirement of technical expertise for setup and maintenance
A further disadvantage of on-premise NPS servers is the need for technical expertise in installation and ongoing maintenance. NPS configurations involve policies, authentication mechanisms, and network protocols. Managing these configurations and resolving problems requires IT professionals proficient in NPS functionalities. Setting up and maintaining on-premise NPS servers can be daunting for organizations lacking dedicated IT resources or limited technical expertise.
Challenges faced by small and mid-size organizations
Small and medium-sized businesses often need help with handling on-premise NPS servers. These groups may also have a limited number of IT tools in terms of people or hardware. So, they need help finding efficient tools and people with the relevant skills to set up, maintain, and fix problems with NPS systems. This can lead to less-than-ideal speed, more downtime, and possible security holes, putting these organizations’ network access control at risk.
Limitations and vulnerabilities of on-premise setups
On-premise NPS setups may also have some problems and security holes. First, they are often limited by the actual infrastructure’s ability to grow and change. Adding more servers to meet increasing network needs can be expensive and time-consuming. Second, on-premise setups might need the robust security measures like strong access controls, network segmentation, incident response planning, detailed logging and auditing, and more that cloud-based solutions don’t. Organizations that only use on-premise NPS systems can face severe threats to their networks and data security because of these flaws.
Challenges of NPS Integration in the Cloud
While migrating Network Policy Server (NPS) functionality to the cloud offers many advantages, it poses several challenges that can harm network security, management, and efficiency. These disadvantages highlight the complication of NPS integration in the cloud and the need for a simplified solution such as SecureW2’s Cloud RADIUS.
- Security Concerns and Compliance
- Configuration Complexity
- Latency and Performance Issues
- Scalability and Cost Management
Security Concerns and Compliance
Integrating a cloud-based NPS raises security concerns due to data traversing external networks. Ensuring the same level of security as an on-premises solution necessitates careful consideration of encryption protocols, access controls, and compliance requirements, particularly for industries with stringent regulations. Maintaining data privacy and protection in the cloud requires a comprehensive security strategy.
Configuration Complexity
Typically, integrating NPS into the cloud necessitates complex configuration procedures, such as the establishment of virtual networks, firewall rules, and identity providers, when integrating NPS into the cloud. Incorrect configurations can result in access disruptions, security holes, and compatibility issues. This complexity necessitates knowledge of NPS and cloud architecture, which might overload IT resources.
Latency and Performance Issues
A cloud-based NPS may induce latency as authentication requests move between on-premises resources and cloud servers. Access delays can hinder productivity and irritate users. To effectively balance performance considerations, network architecture, data centers, and routing strategies must be optimized to minimize latency while ensuring reliable access.
Scalability and Cost Management
Integration with the cloud promises scalability, but managing resources effectively and controlling costs can be difficult. Monitoring and capacity planning are required to expand NPS to meet user demand. Without adequate optimization and resource utilization strategies, cloud resource overspending is possible.
Creating Network Policies in NPS and Their Verification
Network Policy Server (NPS) is a key part of letting users connect to a network by applying company policies and verifying users’ identities. Let’s look at the steps needed to make network rules in NPS and how to make sure they work.
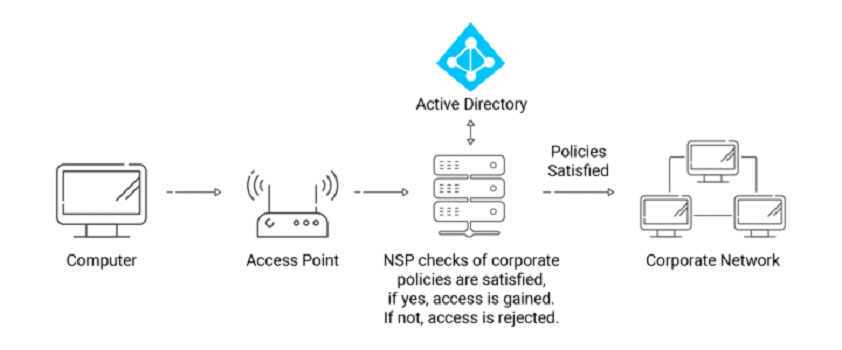
Understanding the Basic Flow of NPS
When a computer wants to connect to the corporate network, it sends a request to the access point. The request is then sent to NPS by the entry point. NPS is a policy server that checks the user login needs and company policies set up. Connecting to Active Directory can check if the individual is part of the company. NPS gives entry to the business network once all the policies have been satisfied.
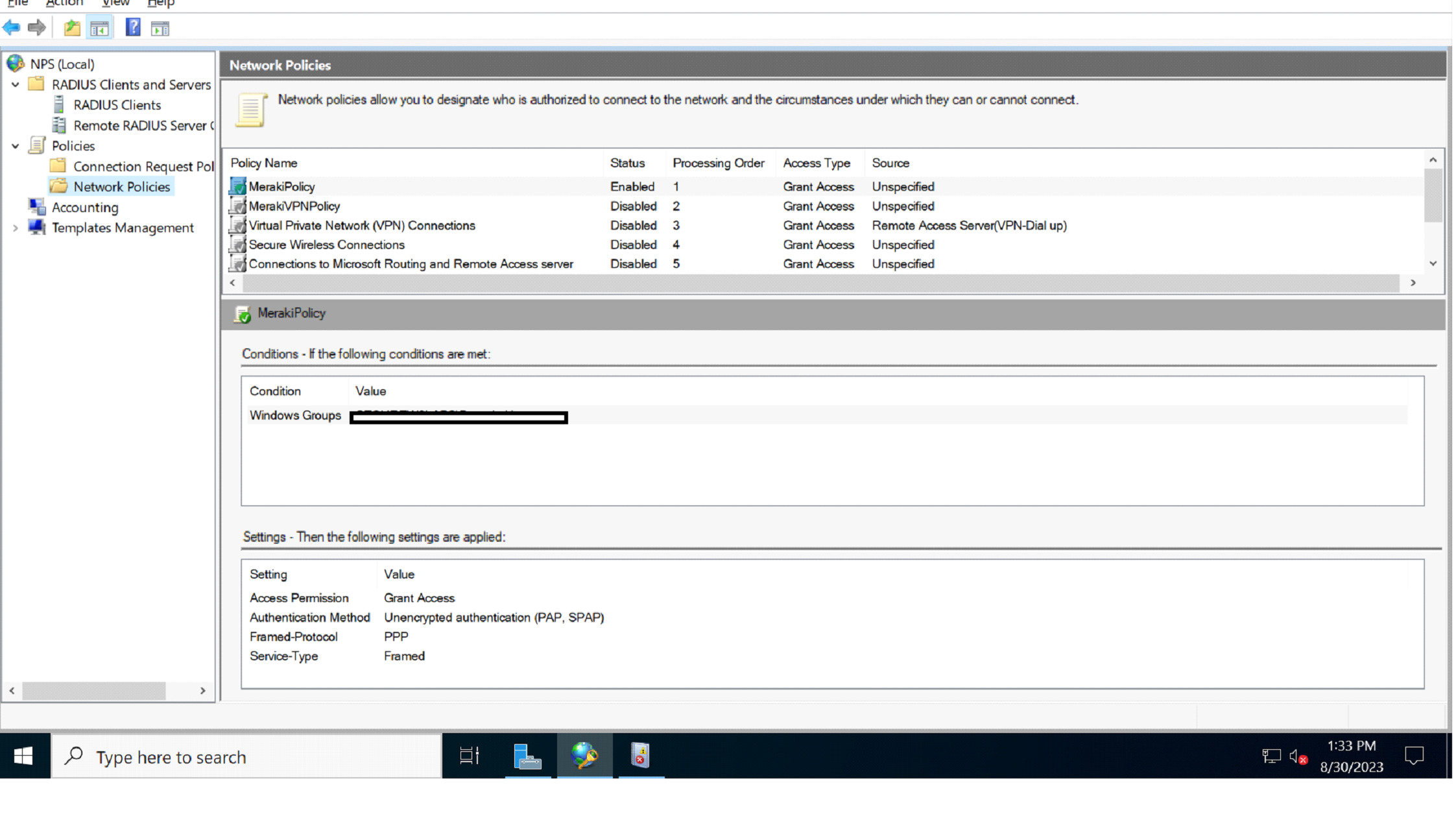
NPS as a Policy Server for Corporate Policies and User Authentication
NPS acts as a policy server, which lets organizations make and enforce their own rules. These rules can have conditions like checking client certificates or ensuring a security program is up to date. NPS allows organizations to set rules at a fine-grained level, ensuring they are followed and keeping the network secure. Also, NPS authenticates users to ensure that only those allowed to can join the business network.
Integration of NPS with Active Directory for User Validation
To verify users, NPS works with Active Directory (AD), a service for managing users that acts as a directory. AD has a list of all the people who are allowed to use the company resources. To ensure the person has access, NPS checks to see if they appear in AD. This interface lets NPS check user details and apply rules based on the user’s name within the AD domain.
Overview of the NPS and Active Directory Setup Process
A short overview of how virtual machines are used to set up NPS and Active Directory. This lets them set up the necessary machinery to apply policies and verify users. The text talks about setting up NPS to work with Aruba access points as clients. This ensures that NPS and the access points can talk to each other without problems.
NPS Extension for Cloud Integration
Integrating Network Policy Servers (NPS) and cloud services such as Azure Active Directory (AD) presents certain restrictions and considerations. Importantly, Azure AD cannot communicate directly with NPS, necessitating the continuous involvement of Active Directory (AD). This implies that even if an organization has largely migrated to Azure AD, traditional AD is still required for NPS functionality. Moreover, the precedence of AD over Azure AD persists, highlighting AD’s prominent role in the NPS configuration. These limitations emphasize the difficulties in achieving seamless cloud integration with NPS and the ongoing interdependence between on-premise and cloud components for effective network access control.
Integrating NPS with Azure Active Directory (AD)
Integration of NPS with Azure AD is one of the most important parts of cloud integration. PowerShell coding is used to copy users from Azure AD to Active Directory (AD). This syncing process allows user names and characteristics to be synchronized between the cloud-based Azure AD and the on-premise AD, creating a single system for managing users.
Three Methods of Replication
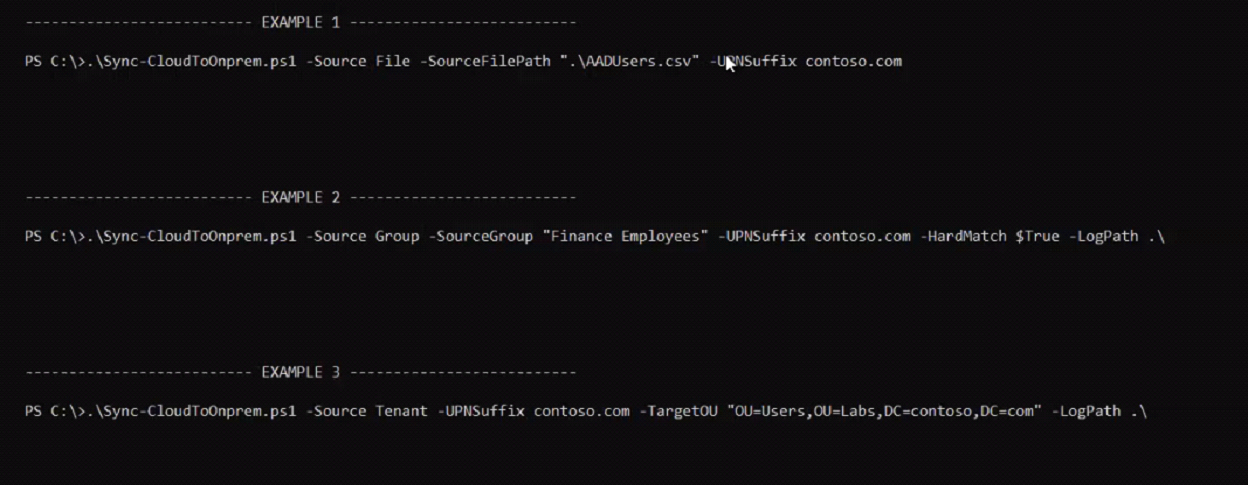
File-based Replication
A CSV file comprising user information, including identities and passwords, is used in this method to replicate Azure AD users to AD. Due to the fact that credentials are stored within the file, there may be more secure options than this one.
Group-based Replication
This procedure replicates particular groups from Azure AD to AD. By selecting specific categories, organizations can ensure that only desired users and their associated permissions are replicated. This method offers greater control and granular replication based on group membership.
Tennat-wide Replication
With tenant-wide replication, all Azure AD users are replicated to Active Directory. This approach benefits organizations that require a complete replication of all Azure AD tenant users. However, it is essential to observe that if the replication of all users is not meticulously managed, duplicates may result.
Feature-Rich Cloud RADIUS
SecureW2 offers Cloud RADIUS, which serves as a powerful authentication mechanism for digital certificates. It plays an important role in verifying user credentials stored within IDPs. This seamless connection enables businesses to utilize their cloud infrastructure and identity management solutions, increasing network access control efficiency and simplifying user authentication procedures.
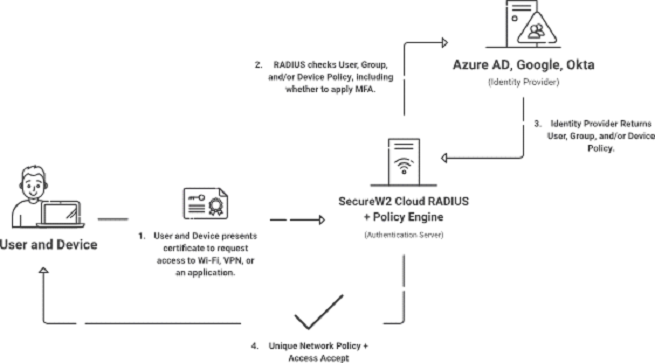
Organizations may avoid the limitations of on-premise NPS servers by using Cloud RADIUS, benefitting from better security, easier administration, and streamlined operations. It offers a stable and secure cloud-based option that satisfies the changing requirements of network access management.
SecureW2’s Cloud RADIUS system has a full set of features that change how network access control is done. One of the most important features is the real-time user lookup against popular cloud-based identity providers like Azure, Okta, and G-Suite. With this feature, organizations can strictly enforce access rules and ensure that only authorized users can access the network.
Also, Cloud RADIUS makes certificate-based security work without a password. By using strong cryptographic methods, organizations can improve authentication security while making it easier for users and managers to keep track of passwords.
Empower Your Network Security with Cloud RADIUS
The complexity and limitations of on-premise NPS servers demonstrate the need for cloud-based alternatives. Cloud RADIUS from SecureW2 offers a compelling choice by integrating seamlessly with prominent cloud identity providers such as Azure, Okta, and Google. This integration enables businesses to leverage the strength of their existing cloud infrastructure, thereby simplifying network access control and enhancing overall security.
SecureW2’s solution eliminates the challenges associated with on-premise NPS deployments, providing enhanced scalability, flexibility, and management simplification. Consider SecureW2’s Cloud RADIUS to achieve seamless NPS integration in the cloud and unleash the full potential of your network access control system.Embrace the advantages of cloud integration, and your organization’s network access control processes will be more secure, easier to manage, and more efficient.
Contact us today and take the plunge into the cloud with Cloud RADIUS.