Implement 802.1X for Managed Chromebooks
In today’s digital-first classrooms, K-12 schools must manage and secure massive fleets of Chromebooks. These devices are crucial for student learning, but standard password-based Wi-Fi network authentication exposes networks to attack and increases IT effort. For schools, guaranteeing safe and smooth access is more than a technical need; it is critical for continuous learning.
802.1X with certificate-based authentication is the appropriate approach for eliminating password flaws while providing robust security. However, handling certificates on 802.1X Chromebooks, which do not permit app installs, may take a lot of work. SecureW2’s new approach solves this problem by combining seamless 802.1X authentication with a simple onboarding procedure.
Read the case study of the Antelope Valley Union High School District, which used SecureW2’s platform to protect its large Chromebook fleet, substantially reducing IT effort and enhancing network security.
What is 802.1X, and Why is It Important?
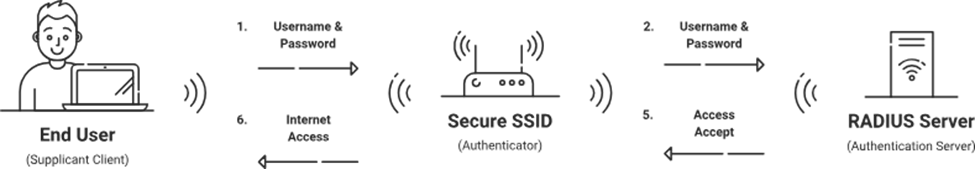
802.1X is an IEEE standard for port-based network access control (PNAC) that aims to improve network security. It creates a secure communication channel between devices (clients) and the network by demanding authentication before allowing access. This standard is a gatekeeper, allowing only authorized people and devices to join the networks.
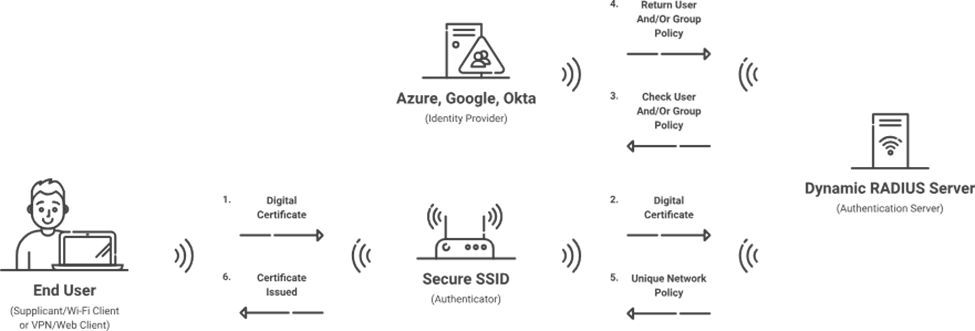
The RADIUS server, which interacts with cloud directories such as Azure AD or Google Workspace, is an integral part of 802.1X. When a person or device tries to connect, the RADIUS server verifies their identity using secure techniques like certificates before granting access.
Key Benefits of 802.1X:
- Preventing Unauthorised Access:1X guarantees that only authorized devices or users can access the network, defending against risks such as rogue devices or attackers seeking entry.
- Granular Access Control: Role-based rules allow organizations to determine which resources individuals may access depending on their responsibilities, ensuring that sensitive data is secured.
- Enhanced Security:1X enhances network security by replacing weak password-based authentication with certificate-based approaches, which avoids typical threats such as credential theft, phishing, and brute-force attempts.
802.1X, with its rigorous authentication method, has become a cornerstone of secure network administration, particularly in schools, corporations, and healthcare facilities where sensitive data protection and frictionless access are vital.
Authentication Methods for 802.1X
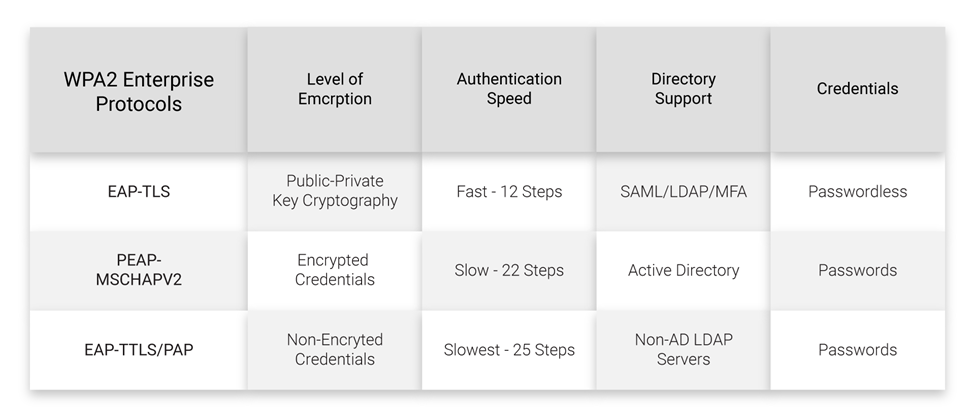
802.1X uses the Extensible Authentication Protocol (EAP) framework to authenticate people or devices to the network. Your EAP protocol substantially influences network security, user experience, and overall network speed. Here’s a summary of the most prevalent EAP techniques and why EAP-TLS is considered the gold standard for secure authentication.
An overview of EAP protocols
EAP-TTLS/PAP:
- This method sends plain text credentials (username and password) across a secure tunnel.
- Why it’s insecure? If the tunnel is breached, credentials can be intercepted, rendering it susceptible to man-in-the-middle (MITM) attacks.
PEAP-MSCHAPv2:
- It combines a secure TLS tunnel and password-based authentication.
- Weaknesses: vulnerability to password theft and brute-force attacks.
- User experience could be better since passwords must be updated or re-entered regularly.
- Due to the dependency on user-entered credentials, it is vulnerable to phishing attacks.
EAP-TLS:
- Mutual authentication uses digital certificates (both client and server).
Why it is the gold standard:
- Certificates are untransferable and associated with specific devices or individuals, reducing the risk of credential theft.
- Automated certificate lifecycle management guarantees that renewals and revocations are completed smoothly, boosting network security and decreasing administrative costs.
- Eliminates the need for passwords, resulting in a better user experience and increased protection against typical threats such as phishing and brute force.
EAP-TLS Is the Future of 802.1X Authentication
EAP-TLS provides better network security by employing certificate-based authentication. Certificates, unlike passwords, cannot be guessed, stolen, or phished, making them suitable for modern, security-conscious organizations. EAP-TLS and automated certificate lifecycle management reduce the need for human configuration while defending against changing cyber threats.
Organizations wanting to improve network security should prioritize EAP-TLS, particularly in contexts with sensitive data, such as schools, hospitals, and enterprises.
Challenges for Chromebook 802.1X Authentication
Chromebooks have been popular in K-12 schools and other organizations due to their low cost, management simplicity, and integration with Google Workspace. However, these devices provide distinct issues for establishing secure 802.1X authentication, owing to limitations on typical onboarding approaches.
Key Limitation: No App Installations
Unlike other devices, Chromebooks do not enable third-party app installs during onboarding, complicating certificate deployment and authentication. This restriction makes safeguarding network access using traditional techniques such as manual installs or proprietary software impossible.
Unique Solution: SecureW2’s Extension
SecureW2 tackles this issue with a custom industry-exclusive Chromebook extension that facilitates 802.1X authentication without requiring app installs.
The SecureW2 solution has several key characteristics, including:
JSON Protocol Support:
- Administrators may configure Chromebook policies directly in the JSON file, allowing for smooth certificate enrollment.
- This ensures that Chromebooks may be provided and authorized without manual intervention.
SCEP Protocol for Certificate Enrolment:
- SecureW2 supports the Simple Certificate Enrolment Protocol (SCEP), which enables Chromebooks to seek and obtain digital certificates securely.
- This automated procedure eliminates the need for IT workers to provide certificates, saving time and lowering errors manually.
Why it works
By connecting directly with Google Admin Console and taking advantage of protocols like JSON and SCEP, SecureW2 allows schools and organizations to:
- Streamline certificate onboarding for big fleets of Chromebooks.
- 1X with EAP-TLS provides safe, passwordless authentication for Wi-Fi networks.
- Overcome device restrictions while maintaining high-security levels.
This innovative solution has been successfully deployed in K-12 institutions such as the Antelope Valley School District, where administrators can easily enroll thousands of Chromebooks. Interlinking certificate-based 802.1X authentication with SecureW2 allows schools to meet network security requirements while maintaining usability.
How SecureW2 Simplifies Chromebook Onboarding
Chromebooks’ unusual architecture makes onboarding them for secure 802.1X authentication difficult, but SecureW2 streamlines the process with an automated, seamless solution. Organizations may use SecureW2’s Managed Device Gateway to offer certificate-based authentication via JSON and SCEP protocols without needing third-party apps. Here’s a step-by-step tutorial for the procedure:
Step 1: Configure SecureW2’s Managed Device Gateway.
The Managed Device Gateway connects your identity provider (IdP) with the Chromebook fleet, guaranteeing safe certificate issuing and authentication.
Set up IDP in the SecureW2 Management Portal:
- Integrate Google Workspace or any other compatible IDP into SecureW2.
- Use Google Verified Access API to verify Chromebooks as managed devices during authentication.
Enforce network policies and access levels:
- Use role-based access policies to control which network resources specific individuals or groups can access.
- Use granular controls to protect guest access and ensure organizational compliance.
Step 2: Configure Google Admin for Auto Enrolment
The Google Admin is essential for automatically deploying certificates to managed Chromebooks.
Connect to Wi-Fi and enroll.
- The admin user connects the device to an Open/PSK Wi-Fi network.
- The device is enrolled under the Google Domain.
Initial Onboarding Policies (Google Onboarding OU)
- Place the device in the Google onboarding Organisational Unit (OU), which applies the following minimal policies:
- Allow administrative users to log in to the desktop.
- Configure and deploy the JoinNow MultiOS Chrome Extension.
- Allow public sessions.
Post-onboarding Policies (Public Session Google OU)
- After the device has been onboarded, transfer it to the Public Session Google OU.
- Implement the following minimal policies:
- Allow public sessions.
- Prevent administrative users from logging in.
- Re-deploy the JoinNow MultiOS Chrome Extension with settings.
Authentication Process
- The JoinNow MultiOS Chrome Extension is launched upon login.
- It checks for a valid certificate. If unavailable:
- The plugin uses Google Verified Access API to obtain a Google Token.
- The Google Verified Access API checks the device and provides the Google Token to the extension.
Certificate Enrolment
- The JoinNow MultiOS Chrome Extension prompts the device to generate a public-private key pair using the TPM.
- Create a certificate signing request (CSR).
- The JoinNow MultiOS Agent provides the Google Token, device details, and CSR to the JoinNow Enrolment Portal over HTTPS.
- The enrolment portal
- Validates the Google Token with Google to obtain the identifying Google Device ID.
- Enrolment data is used to determine the certificate policy.
- Creates a signed certificate and delivers it to the extension.
- The JoinNow MultiOS Chrome Extension installs the granted certificate.
Connect to secure WiFi.
- The device connects to the secure Wi-Fi network using the given certificate.
- It performs an 802.1X/EAP-TLS authentication against the CloudRADIUS infrastructure.
- SecureW2 CloudRADIUS enforces the necessary network policy and allows access to the secure Wi-Fi network.
Step 3: Key Technical Configurations.
SecureW2 enables advanced configurations that allow for easy onboarding and proper certificate deployment.
Using JSON or SCEP protocol:
- Use JSON to set up custom policies that automatically enroll Chromebooks in SecureW2.
- Utilise SCEP for efficient certificate issuing while minimizing manual IT involvement.
Creating custom JSON policies:
- In the SecureW2 Management Portal, create JSON policies that specify enrolment parameters like SSIDs and certificate templates.
- Push these policies to Chromebooks using the Google Admin Console.
Configure and Push Wi-Fi Settings:
- Use SecureW2’s interface to pre-configure Wi-Fi network settings for 802.1X authentication.
- Automatically send these configurations to Chromebooks to ensure they connect to the correct network using EAP-TLS.
Organizations may reduce manual interventions by automating enrolment with SecureW2’s Chromebook extension, ensuring Chromebooks easily authenticate to secure networks. This technique simplifies device management and improves security by enabling passwordless, certificate-based authentication.
Why EAP-TLS is Perfect for K-12 Chromebook Fleets
For K-12 schools with large fleets of Chromebooks, EAP-TLS (Extensible Authentication Protocol-Transport Layer Security) is the gold standard for safe network authentication. EAP-TLS replaces passwords with certificates, ensuring robust security and streamlining device management, making it excellent for educational settings.
Specific Benefits for K-12 Institutions
Role-Based Access Control:
- EAP-TLS provides granular access control, allowing IT managers to assign different network permissions based on users’ responsibilities (e.g., students, instructors, and staff).
- Students, for example, may be restricted to academic materials while professors are granted access to administrative tools.
Simplified Integration with Roaming Platforms:
- EAP-TLS works flawlessly with roaming platforms like Eduroam, which is commonly used in educational institutions.
- This enables K-12 schools to give students and staff safe and automated Wi-Fi connectivity, even when they visit partner universities.
Native Integration with Cloud Directories:
- SecureW2 improves EAP-TLS by supporting cloud directories such as Google Workspace and Azure AD.
- This simplifies Chromebook fleet management by allowing users to authenticate using their current cloud credentials.
Additional Features of SecureW2 for K-12
Automated certificate lifecycle management:
SecureW2 automates certificate issues, renewal, and revocation, guaranteeing that expired or compromised credentials are quickly updated without IT involvement.
This reduces the downtime that typically comes with manual certificate management.
Detailed reports and logs:
SecureW2 logs contain detailed information about onboarding and authentication events, including onboarding status, certificate issuance history, and RADIUS authentication records.
This enables K-12 IT teams to easily resolve network connection issues and maintain compliance.
BYOD onboarding for unmanaged devices:
While Chromebooks are typically managed, students and staff may bring their own devices (BYOD).
SecureW2’s self-service onboarding portal allows unmanaged devices to securely enroll in certificates, ensuring that all devices on the network fulfill the same authentication standards.
EAP-TLS provides a secure, scalable, and efficient network environment for K-12 Chromebook fleets, allowing schools to improve learning outcomes while reducing security concerns. When combined with SecureW2’s advanced capabilities, schools receive a comprehensive solution suited to their specific needs, from managed network or device authentication to smooth BYOD onboarding.
The Future of Chromebook Authentication with SecureW2
As K-12 schools grow digital ecosystems, SecureW2 provides future-proof authentication with unmatched scalability and flexibility. Whether adding more Chromebooks or integrating new cloud platforms, SecureW2’s solutions adapt to changing demands, allowing for the smooth administration of expanding device fleets.
SecureW2’s vendor-neutral approach provides interoperability with any major Wi-Fi solution or network infrastructure, allowing schools to use their preferred hardware and software while preserving top-tier security. This flexibility enables schools to upgrade their networks without worrying about authentication compatibility.
Read the complete guide on Chromebook certificate auto-enrollment for more information on how SecureW2 can ease certificate-based 802.1X authentication for Chromebook fleets.
Make Network Security Simple and Secure for Chromebooks
Managing Chromebook fleets in K-12 contexts can be difficult due to app installation limits, password-based authentication risks, and IT resource constraints. SecureW2 overcomes these issues by providing a smooth, secure solution incorporating EAP-TLS and certificate-based authentication for Chromebooks.
SecureW2 streamlines network security by automating certificate enrolment, implementing role-based access controls, and providing extensive reporting. Thus, schools can focus on education while ensuring their networks are secure.
Learn how SecureW2 can improve your Chromebook authentication. Contact us to learn how we’ve helped K-12 institutions like yours!