IEEE 802.1X Authentication Methods Compared
There were almost 1800 significant security breaches in 2021 as per a news report by CNET and this number only rose during 2022, making network security a critical requirement for enterprises. From personal information to infrastructure to key data, everything is vulnerable to cyber-attacks and data compromise. Secure, fool-proof, and seamless authentication of end users is a critical requirement for any growing enterprise dealing with data of any kind. WPA or Wi-FI Protected Access is the authentication protocol put in place by the Wireless Alliance and secures end users in an organizational network.
The four Wireless Security Protocols at present are:
Wired Equivalent Privacy (WEP)
Wi-Fi Protected Access (WPA)
Wi-Fi Protected Access 2 (WPA2)
Wi-Fi Protected Access 3 (WPA3)
What is IEEE 802.1X Authentication?
IEEE 802.1X is an IEEE standard for Port-based Network Access Control. Set by the Institute of Electrical and Electronic Engineers Standard, it provides an authentication mechanism for devices that wish to connect to a LAN or a Wi-FI LAN. IEEE 802.1X authentication has three parties involved in the process of authentication. The user, the authenticator, and an authentication server. The Authentication servers run software that supports the RADIUS and the EAP Protocols. Our Cloud RADIUS server is a solution that authenticates end-users across organizations of any size.
The most commonly used EAP protocols are the WPA 2-PSK and the WPA2-Enterprise protocols across home networks and organizations. This article would list the differences between the WPA2- PSK and the WPA2- Enterprise network authentication via the 802.1X protocol, the WPA2- Enterprise protocols, and why they are widely accepted as the superior mode of authentication across organizations.
WPA2-PSK (Wi-Fi Protected Access Preshared Key 2) is a network protected by a single password for all. It is only as safe as the people using it. If it is obtained by unauthorized users through dubious means, the network can be compromised easily whereas the WPA2-Enterprise uses a RADIUS Server to authenticate users on its network. Based on the 802.1X protocol the WPA 2- Enterprise is considered the gold standard, as it provides maximum security by facilitating the use of digital certificates along with the RADIUS authentication server.
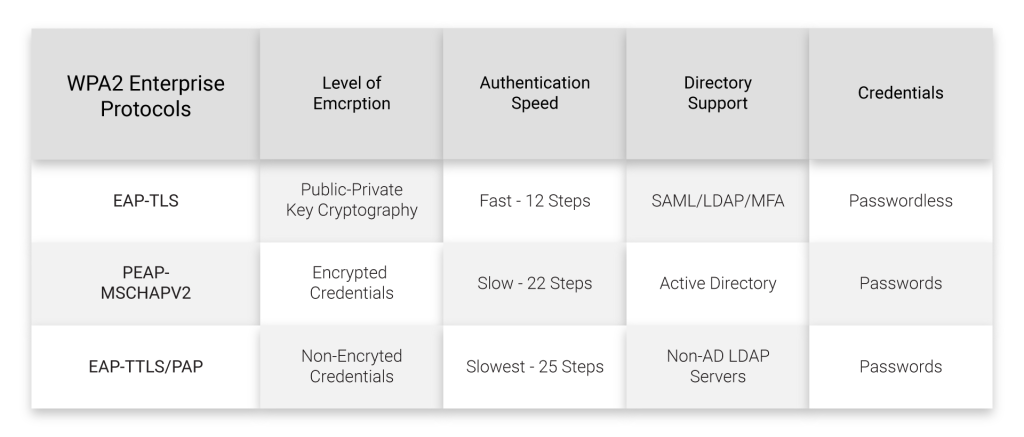
The most common WPA-2 Enterprise authentication protocols are
- EAP-TTLS/PAP
- PEAP-MSCHAPv2
- EAP TLS
Common 802.1X Authentication Methods
1. EAP-TTLS/PAP
EAP-TTLS/PAP is a credential-based authentication protocol like the PEAP-MSCHAPv2 and faces similar threats as devices on the PEAP-MSCHAPv2 protocol. An EAP-TTLS/PAP is vulnerable to MITM attacks and phishing based on credentials. End-users have to be extremely cautious and follow best practices and stop sharing passwords to avoid credential theft. An EAP-TTLS/PAP transmits credentials in the form of Cleartext through its tunnels. The Cleartext is unencrypted making it at risk and vulnerable to MITM or a phishing attack. A data thief can easily get access to a secured network if credentials are easily accessible.
2. PEAP-MSCHAPv2
PEAP-MSCHAPv2 requires credentials to authenticate users. A credential-based authentication is easy to set up and widely used. A user enters their credentials and these credentials are sent through encrypted EAP tunnels or “ extensible authentication protocol”. The encrypted tunnel prevents users from other networks from reading or getting access to the credentials.
However, what is easy is not safe all the time. Credentials are vulnerable to several attacks like a Man-in-the-Middle or a MITM attack where it can be intercepted by someone on the way to encryption. Hackers can also use various forms of attacks like trying to guess easy passwords and using a combination of letters, symbols, or words to guess a password or credentials. The PEAP-MSCHAPv2 protocol has been in use for many years making it more open to attacks.
The PEAP-MSCHAPv2 uses the MD4 algorithm for hashing and is obsolete due to cryptographic weaknesses. Cryptographic weakness renders the algorithm vulnerable to attacks and security threats as these credentials can be masked by a hacker. Once hacked, they can perform any action that the original user is authorized to perform on the network.
3. EAP-TLS
EAP-TLS is the best solution for strong and secure authentication of devices over a network. The EAP-TLS is a certificate-based security authentication that uses unique certificates for individual systems. Being highly secure, it is always on the guard to fight any attacks on the network and reduce vulnerability.
Information for authentication on the EAP-TLS is sent through a tunnel, however, is encrypted and cannot be accessed by an impersonator or a hacker. If the network is hacked, then the credentials that are obtained would be encrypted and cannot be decrypted rendering it unusable. Also, a certificate is unique for each device and cannot be shared among devices or users.
Why should an organization shift to certificate-based authentication (CBA)?
Encrypted credentials sent over cleartext are vulnerable to data theft as they are easier to decrypt and fall into the wrong hands. Credentials sent over cleartext are vulnerable to data theft as their encryption can be sidestepped leaving the password plain to see. Certificates do not have this disadvantage – even if intercepted, the attacker only receives one-half of the asymmetric key rendering it useless.
Configuring EAP-TTLS/PAP on an end-user device is very technical and easy to mess up. A small misstep, such as omitting Server Certificate Validation, introduces a weakness in your security perimeter – making the whole network vulnerable to threats.
Authenticate your network through EAP-TLS: A Zero Trust-based solution
The authentication method to secure a network server is crucial to the safety and security of an organization. Users are going to connect to a network daily and a lot of crucial and confidential data is passed through these networks. A network authentication process that is susceptible to MITM or phishing attacks can compromise the integrity of an organization, leaving it vulnerable.
The PEAP- MSCHAPv2 and the EAP-TTLS/PAP use passwords as credentials to authenticate a user on the network, thus making it vulnerable to security theft and compromising data. The EAP-TLS uses certificates to authenticate users on a network making it secure as it is impossible to duplicate them or use them in more than one system.
At SecureW2, we have solutions to fit your organizational needs. Right from small organizations to bigger ones, we have tailor-made solutions for all. Our solutions include a robust PKI and a Cloud RADIUS server designed for passwordless authentication to secure data over a network.
Click here to inquire about pricing