
How to Implement PAM With Cloud RADIUS
The average employee has access to at least 52% of an organization’s confidential data. The latest Verizon DBIR 2022 states that almost 80% of organizations have experienced employees abusing and misusing business applications through their access privileges. Privilege abuse accounts for at least 2.5% of accidental rather than intentional breaches.
However, intentional breaches are highly malicious, with higher possibilities of compromised confidential records and data. With more and more cloud applications, organizations should add a layer of security to protect their network using privileged network access.
Read on to learn more about Privileged Access Management (PAM), its attributes, and its differences from Identity Access Management (IAM). Later, see how certificate-based authentication creates sufficient user access privileges and enhances network security.
What Is Privileged Access Management (PAM)?
Privileged Access Management helps organizations assign special access privileges above and beyond those given to a standard user. PAM is a comprehensive security mechanism that comprises users, processes, and technology to allow, control, monitor, and audit users and devices on a network.
With PAM, you can regulate users’ access to specific resources. For example, an employee from the human resources department cannot access confidential codes, and an engineer cannot access personal employee data as it does not pertain to their work.
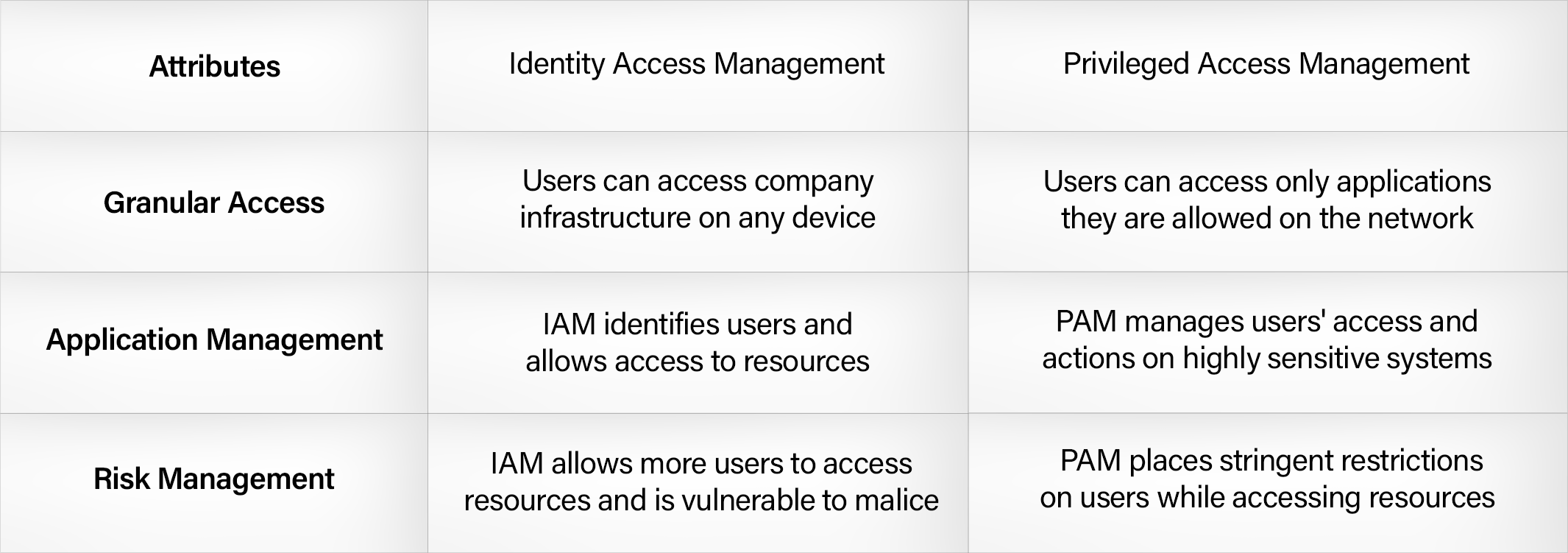
Privileged Access Management (PAM) vs. Identity Access Management (IAM)
Privileged Access Management falls under the broad purview of Identity Access Management (IAM). PAM and IAM work together to provide granular network control, user and device visibility, and audit over access privileges. IAM controls and provides authentication of identities to ensure that the correct user has access at the right time.
PAM adds an extra layer of granular visibility — i.e.; the admin can see which user is using what device at any time. Admins can also monitor user sessions and audit privileged identities. PAM is the core element in identity management that is vital to protect organizational assets in an increasingly remote, work-from-anywhere environment.
How to Create Attribute-Based Policies for Access Control
Attribute-Based Access Control has emerged as an extremely critical solution for secured access to enterprise-related data and applications. The network landscape has become very complex due to many devices, remote access, IoT, and cloud apps, rendering role-based access non-effective.
Attribute-Based Access Control assigns specific access policies based on granular attributes that result in accurate decisions. A directory or an X.509 digital certificate can store information such as names, email addresses, and locations. It can also store environmental attributes like the AP from which a user accesses the network, time, device, and the last authorization time.
Attribute-based control can be cumbersome to apply to directories as they limit the amount of information stored on them. X.509 certificates can be deployed with any type of information that you need to create custom attributes for ABAC policies with precision.
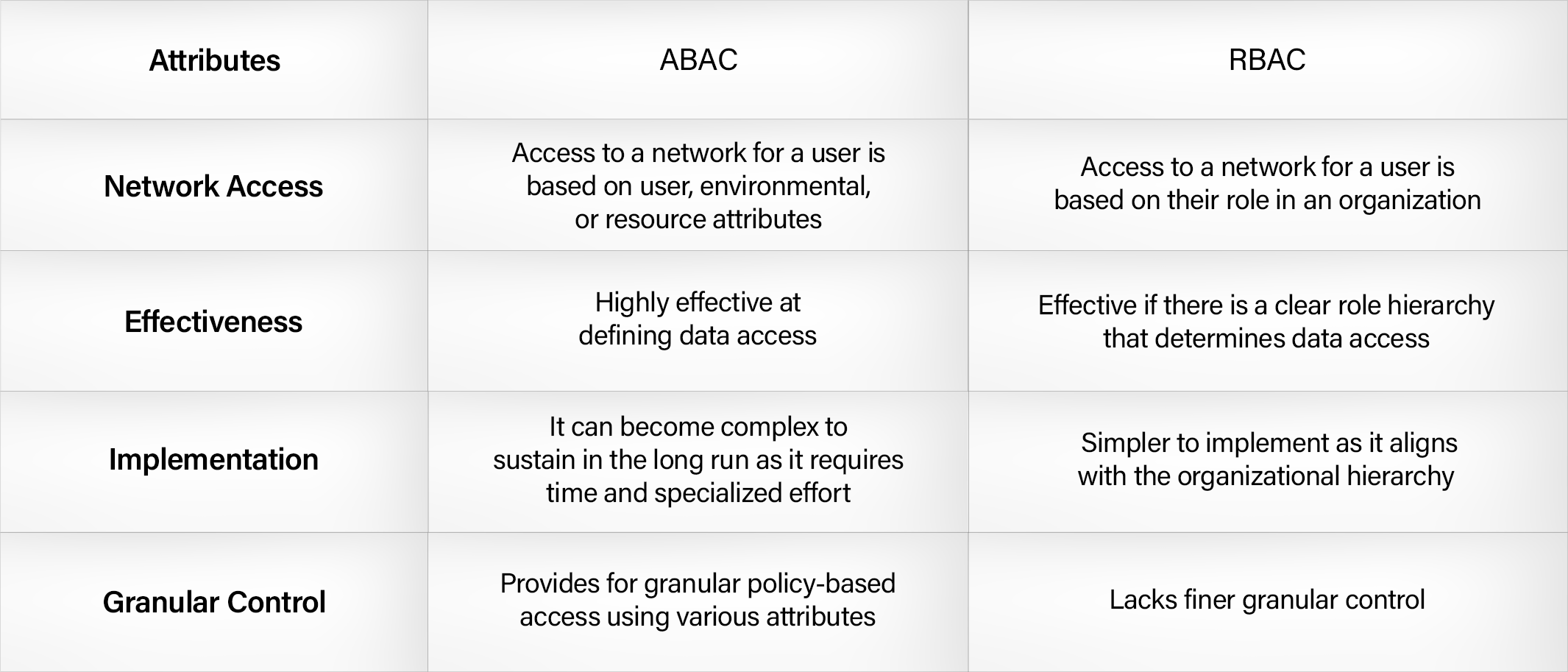
How Attribute-Based Access Control Differs From Role-Based Access Control
ABAC, or Attribute-Based Access Control, provides access control based on specific attributes like name, email address, and environmental attributes. A digital certificate is embedded with specific attributes that can be applied to set policies for granular access.
RBAC, or Role-Based Access Control, provides user access based on their roles in the organization. RBAC would be a hassle to implement in the cases of inter-company transfers and hierarchical changes, requiring immediate access revocation.
How Digital Certificates Lend Attributes for Advanced Access Control
Digital certificates enable admins to give advanced access control to devices or users in the following ways:
- Providing granular access control
- Providing specific access-based profiles
Providing Granular Access Control
A digital certificate can be embedded with user information such as email address, location, and position in or affiliation with an organization. Certificates can also be revoked or replaced with a fresh certificate upon role changes or employees quitting their positions. These attributes would present the exact user or device information to an admin for finer access control.
Providing Specific Access-Based Profiles
Access-based models can be set up with digital certs to establish lexical, transactional, and structural profiles. These attributes may be set up for the same roles in an organization. Highly confidential information and applications alone may be secured by certificates and classified into a certain profile. This would ensure that only a certain profiled user can access privileged information.
Implementing Effective PAM With SecureW2
Privileged Access Management is perceived as tedious and perhaps complex. However, SecureW2 provides a comprehensive NAC suite with all the tools and software needed to configure 802.1X EAP-TLS authentication and simplify the management of user certificates across networks.
With SecureW2’s 802.1X EAP-TLS authentication, you can customize user certificates and assign them access controls at the outset. Our vendor-neutral solutions can be easily deployed out of the box, making them cost-effective and seamless.
Click here to learn about our pricing options to unlock network control options for your organization.