How To Auto Deploy RADIUS WiFi With Group Policy
Imagine entering your office and instantly connecting to a secure WiFi network without entering passwords or configuring security settings. Sounds like magic, right? That’s the beauty of RADIUS and Group Policy functioning together. RADIUS, short for Remote Authentication Dial-In User Service, serves as a gatekeeper, ensuring that only authorized users can access your network. Group Policy is Windows Server’s unsung hero, silently administering and customizing settings across all PCs in your domain.
Now imagine the power of automating this secure Wi-Fi rollout—no more manual setups for each device. Instead, with a few clicks, any device in your organization connects to the network, authenticated and safe. This is more than simply comfort; it is a game changer regarding network security and efficiency. Let’s look at how you can leverage this potential and make WiFi deployment as simple as possible.
This article is intended to be your go-to resource for auto-deploying Group Policy RADIUS authentication. We’ll go over the processes required to check that your network architecture supports RADIUS, set up a RADIUS server, and set up the appropriate certifications. We’ll also cover how to establish and maintain Group Policy Objects (GPOs) for delivering RADIUS Wi-Fi settings, as well as how to migrate to cloud-based solutions like Microsoft Endpoint Manager (Intune).
Understanding RADIUS Authentication
RADIUS (Remote Authentication Dial-In User Service) is a client-server protocol and software that allows remote access servers to interact with a central server to authenticate dial-in users and grant them access to the desired system or service.
RADIUS allows an organization to store user profiles in a centralized database that all distant servers can access. A central database improves security by allowing a corporation to establish a policy to implement in a single managed network point. A central database also makes tracking consumption and maintaining network statistics easier for invoicing. RADIUS, developed by the former networking vendor Livingston Enterprises in 1991, is now the de facto industry standard utilized by the top networking equipment makers. In 2000, the Internet Engineering Task Force accepted the RADIUS protocol as a draft standard specified in RFC 2865.
How Does RADIUS Authentication Work?
With the RADIUS protocol, a Network Access Server (NAS), which serves as a client of the RADIUS servers, allows remote network users to access their networks. The NAS requests RADIUS authentication, authorization, and configuration data from the RADIUS server whenever a remote user establishes a connection. After that, the RADIUS server confirms the user’s credentials and reacts appropriately. Numerous access methods are supported by these centralized authentication methods, such as controlled network access switches that follow the 802.1x standard, dial-in servers, VPN servers, and wireless access points. To provide secure network access, end users communicate indirectly with the RADIUS servers through the NAS.
Understanding Group Policy
A collection of Group Policy settings known as Microsoft’s Group Policy Object (GPO) specifies a system’s appearance and behavior for a specific user group.
You may use the Group Policy Management Console (GPMC) with a software snap-in that Microsoft offers. The selections provide a Group Policy Object (GPO). Organizational units (OU), domains, and sites are some Active Directory containers linked to the GPO. With the GPMC, you may establish a GPO that specifies registry-based policies, security settings, program installation and maintenance settings, scripting settings, and folder redirection settings.
Types of GPOs
GPOs are divided into three types: local, non-local, and starter.
Local Group Policy Objects. A local GPO is a collection of group policy settings that only apply to the local machine and its users. Local GPOs are included by default on all Windows machines.
Non-local Group Policy Objects. A non-local group policy object (GPO) is used when policy settings must be applied to one or more Windows PCs or users. Non-local GPOs are applied to Windows PCs or users when joined to Active Directory objects such as sites, domains, or organizational units.
Starter Group Policy Objects. Introduced in Windows Server 2008, starter GPOs are Group Policy configuration templates. These objects allow an administrator to establish and save a pre-configured set of parameters that serve as a baseline for future defined policies.
Preparing for Group Policy RADIUS Authentication
Configuring a safe and efficient RADIUS Wi-Fi network involves numerous key stages. The preparatory steps are outlined here, focusing on setting RADIUS Authentication with WPA2-Enterprise.
WPA2-Enterprise with 802.1X authentication is used to verify people or machines within a domain. The procedure includes the following components:
Supplicant (wireless client): This client authenticates against the RADIUS server using the Extensible Authentication Protocol (EAP) technique.
The Authenticator (access point): sends authentication communications between the supplicant and the computer authentication server.
RADIUS server: This server performs user authentication and delivers Access-Accept signals to the access point to authorize network access.
Access Control and EAPOL Exchanges
Access points process Extensible Authentication Protocol Over LAN (EAPOL) exchanges between supplicants and transforms them to RADIUS Access-Request messages. These communications are routed to the RADIUS server’s IP address and the specified UDP port. To reduce latency, place the RADIUS server and access points in the same layer-2 broadcast domain.
Supported RADIUS Attributes
When setting WPA2-Enterprise with 802.1X, the following RADIUS attribute details appear in Access-Request messages:
- User-Name
- NAS-IP-Address
- NAS-Port
- Called-Station-ID: Contains the access point’s BSSID and SSID.
- Calling-Station-ID: Contains the MAC address of the wireless device.
- Framed-MTU
- NAS-Port-Type
- Connect-Info
RADIUS Server Requirements
To support WPA2-Enterprise, the RADIUS server must:
- Obtain a certificate from a trustworthy Certificate Authority (CA).
- Configure each gateway access point as a RADIUS client with a shared secret.
- Maintain a user database for authentication.
RADIUS Configuration (Windows NPS + AD)
Setting up Windows Network Policy Server (NPS) entails:
1 – Add the NPS role to Windows Server:
- Install the Network Policy Server (NPS).
- Register the NPS server with Active Directory.
2 – Add a trustworthy certificate to NPS:
- Obtain a certificate from a trustworthy CA, set up a PKI, or create a self-signed certificate (not recommended for production).
3 – Adding access points as RADIUS client to the NPS server:
- Gather the LAN IP addresses for all gateway access points.
- Add each access point as a RADIUS client in NPS by entering its IP address.
4 – Setting up a policy in NPS to support PEAP-MSCHAPv2:
- Create an NPS policy.
- Change the policy process order.
- Disable auto-remediation.
Auto-Deploying RADIUS Wi-Fi with Group Policy
- Access your Domain Controller by logging in.
- Open Group Policy Management.
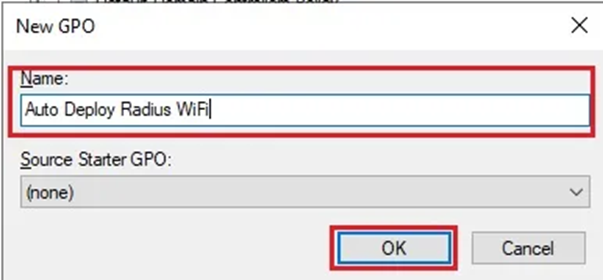
- Find Group Policy Objects, then choose New with a right-click.
4. After giving your policy a distinctive name, click OK.
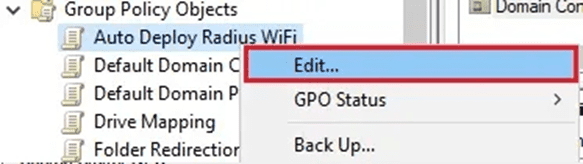
5. Find your new policy. After doing a right-click, select Edit.
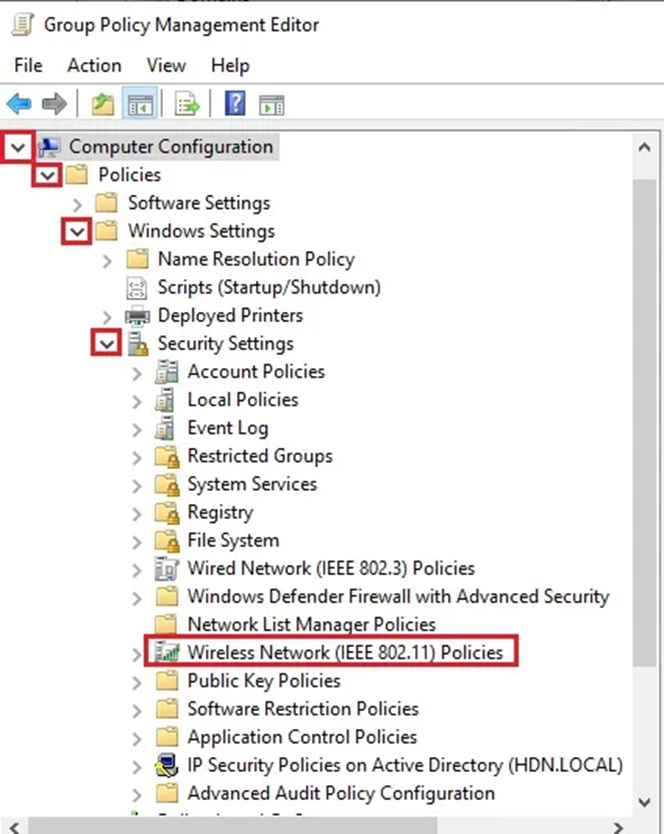
6. Extend to the subsequent Policies > Windows Settings > Security Settings > Computer Configuration > Wireless Network (IEE 802.11 Policies).
7. Extend to the subsequent Policies > Windows Settings > Security Settings > Computer Configuration > Wireless Network (IEE 802.11 Policies).
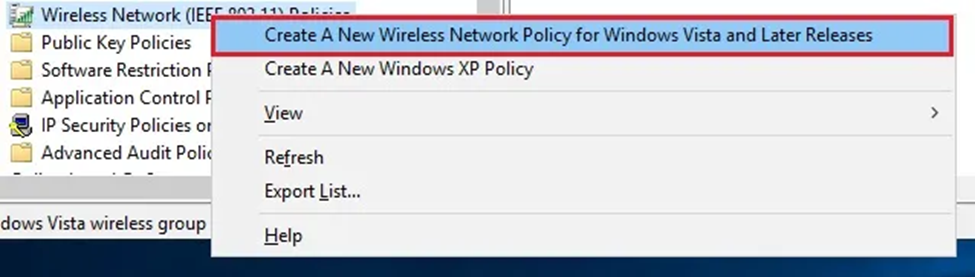
8. Give your policy name a clear and detailed meaning.
9. Select Add from the General Tab.
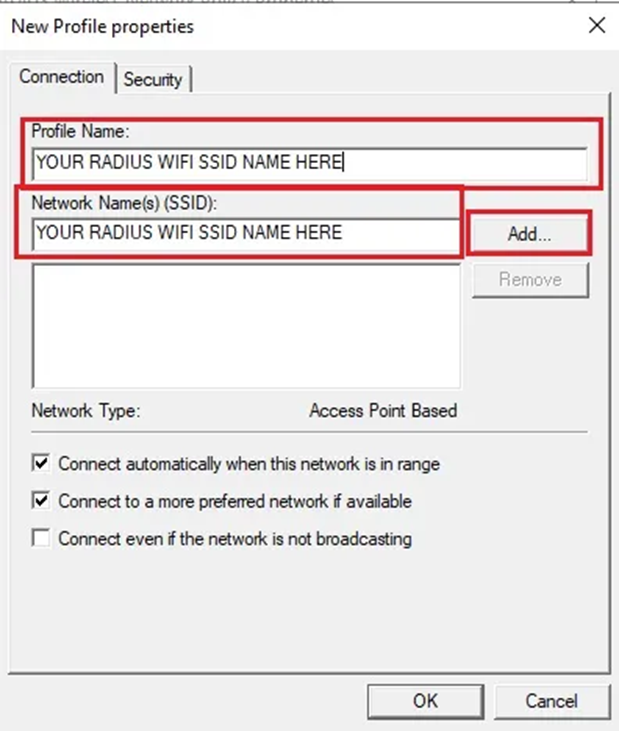
10. Give your new profile a name. In my opinion, you might call it your Radius Wifi SSID. After entering your SSID, click Add.
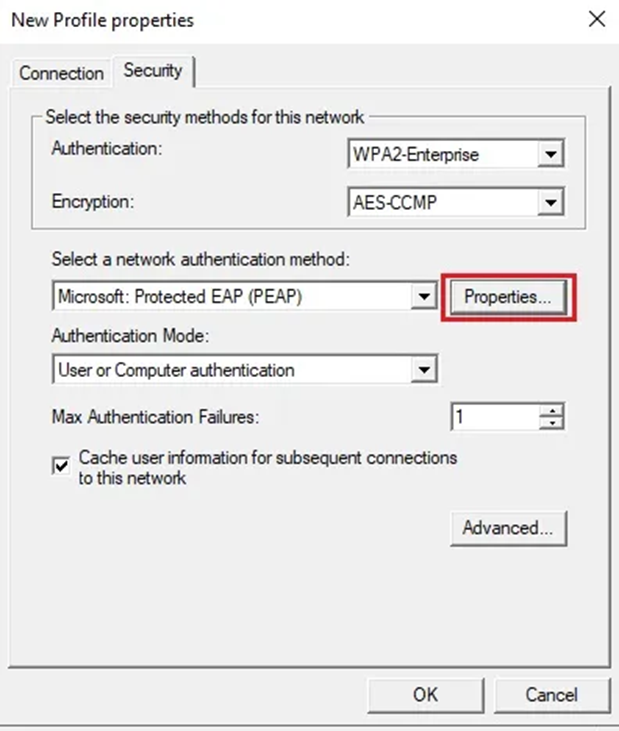
11. Select the Security tab. Next, select Properties.
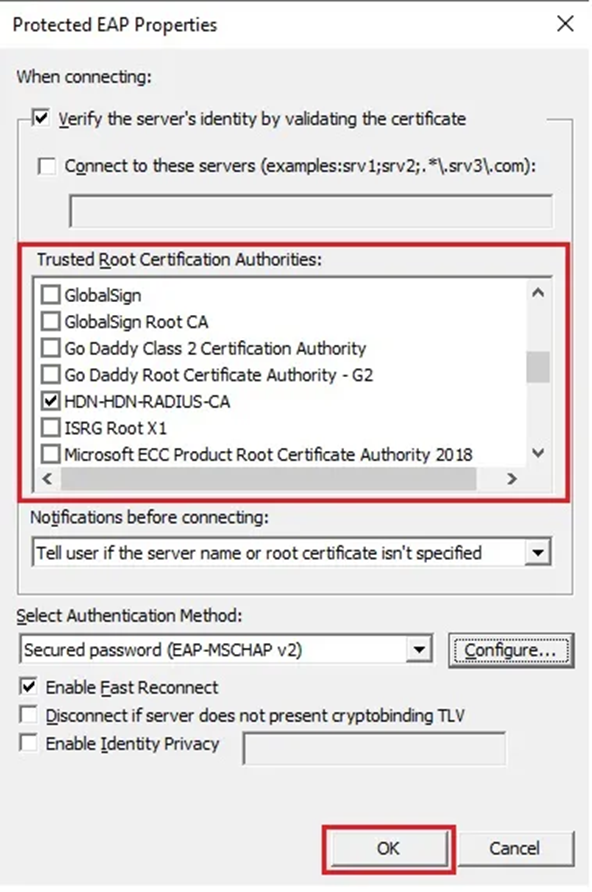
12. For your RADIUS, find the Trusted Root Certification Authority and choose it by clicking OK.
13. After selecting “OK” on each menu, select “Apply.”
14. Connect your Auto Deploy Radius Wi-Fi Policy to the OU containing the workstations now.
15. After performing the group policy update, restart the computer. Your RADIUS Wi-Fi SSID should now be automatically recognizable to your users.
Migrating from On-Premise GPO to Cloud-Centric Intune
What is Intune?
A complete cloud-based solution called Intune is made for setting up, controlling, and safeguarding endpoints in an organization, including PCs, servers, and mobile phones. Intune includes the following services: Windows Autopilot for automating device setup and configuration; Azure Active Directory for storing device and user information; Configuration Manager for on-premises management and application deployment for PCs and servers; Co-management to integrate Intune and Configuration Manager, allowing either to manage different workload groups; Desktop Analytics for actionable insights on applications, drivers, and updates; and the Endpoint Manager Admin Centre, a web interface for managing all Intune components.
Steps for Migration
Migrating Group Policy Objects (GPOs) to Intune can help you streamline administration operations and improve security compliance across your organization’s devices. In this part, we’ll walk you through the procedures for backing up your GPOs from the Domain Controller and importing them into Intune, guaranteeing a smooth transition and optimal policy application.
- Go to your Domain Controller and search for Group Policy Management.
2. Go to the Group Policy Objects OU. There, you will see the Group Policy Objects that you have in place.
3. Clicking on Group Policy Objects displays all of the Group Policy Objects in your domain. Choose the GPOs you wish to back up by right-clicking them and selecting Save Report. Save the file as .XML.
4. Select the location where you want to backup the Group Policy Objects. Set a description to assist in identifying between backups if you have more than one. Also, ensure that the format is set to XML Document.
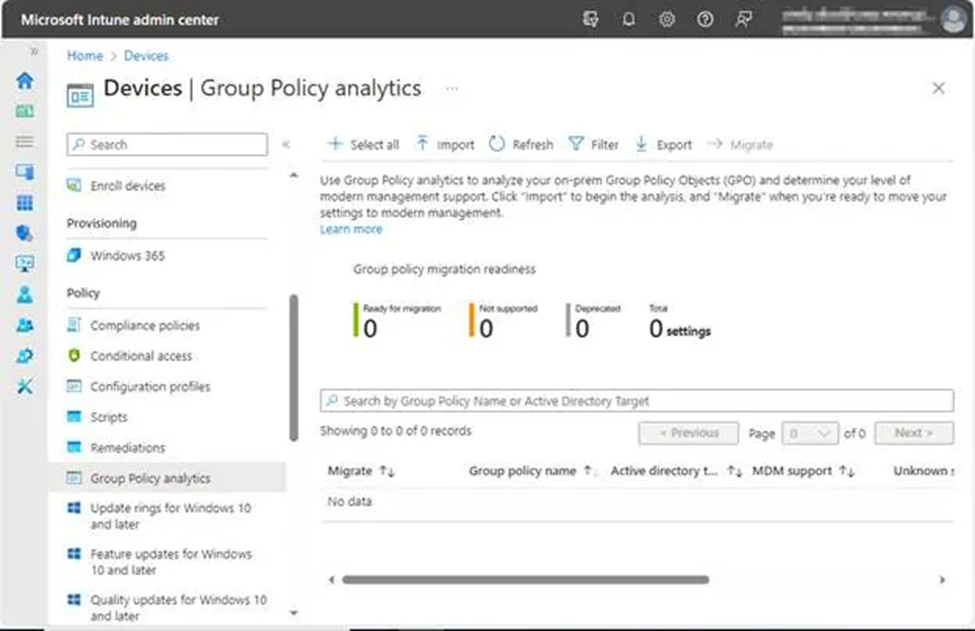
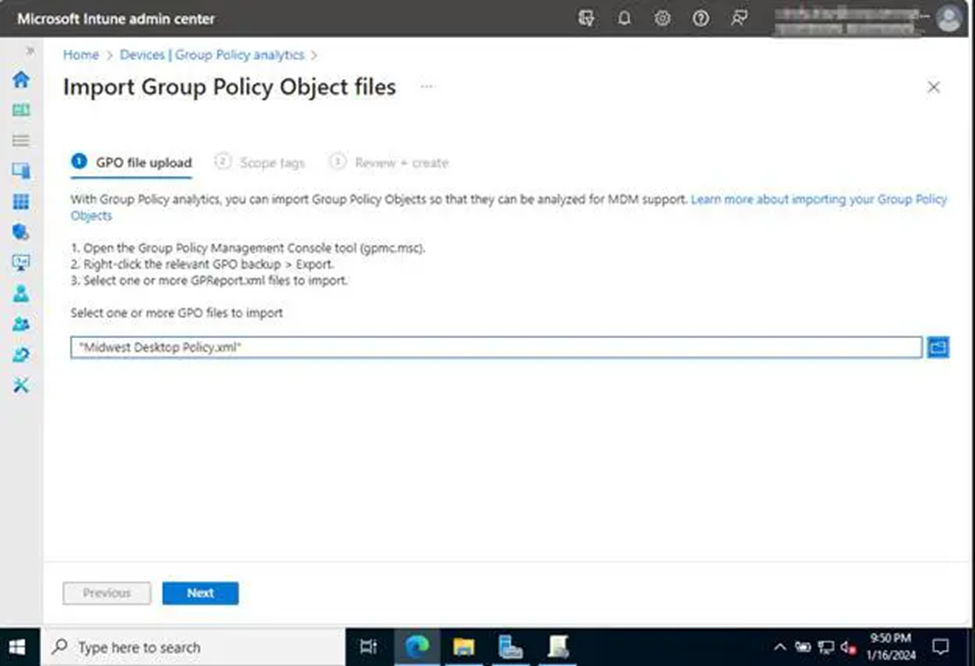
Now that you have your.XML files, let’s go to Intune and import the GPOs. Navigate to https://intune.microsoft.com/devices > Group Policy Analytics.
5. Click Import > You will be sent to the following screen, which contains information on Group Policy Analytics as well as instructions for exporting and importing your GPOs. Find it, select the XML files we saved previously for import, then click Next.
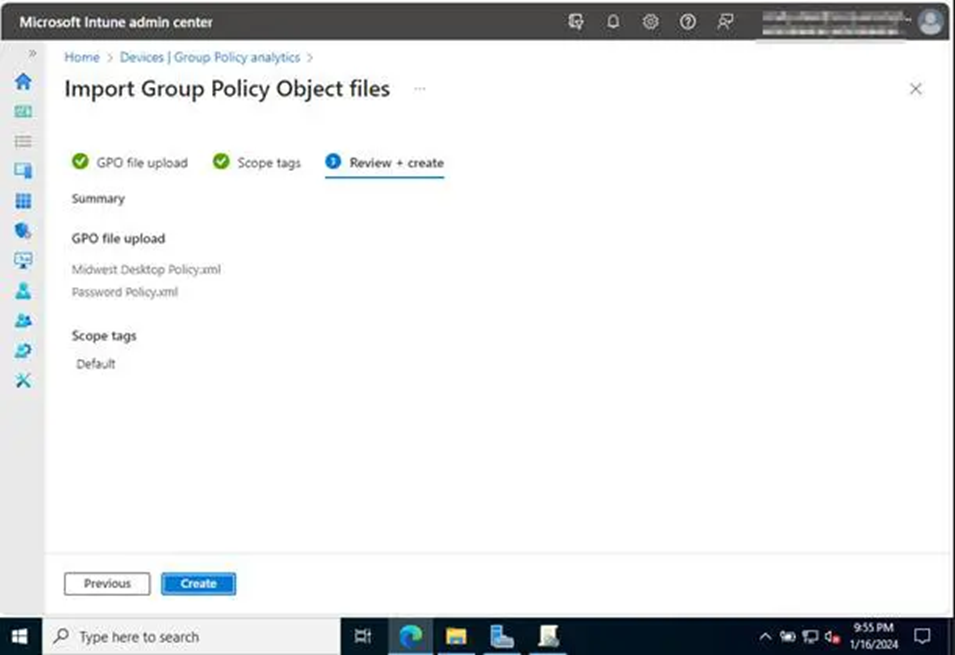
6. After selecting Next, you will be required to provide any scope tags.
7. Check that you’ve included all the imports and scope tags and allocated them to the appropriate locations. When you’re done, click Create to see your results.
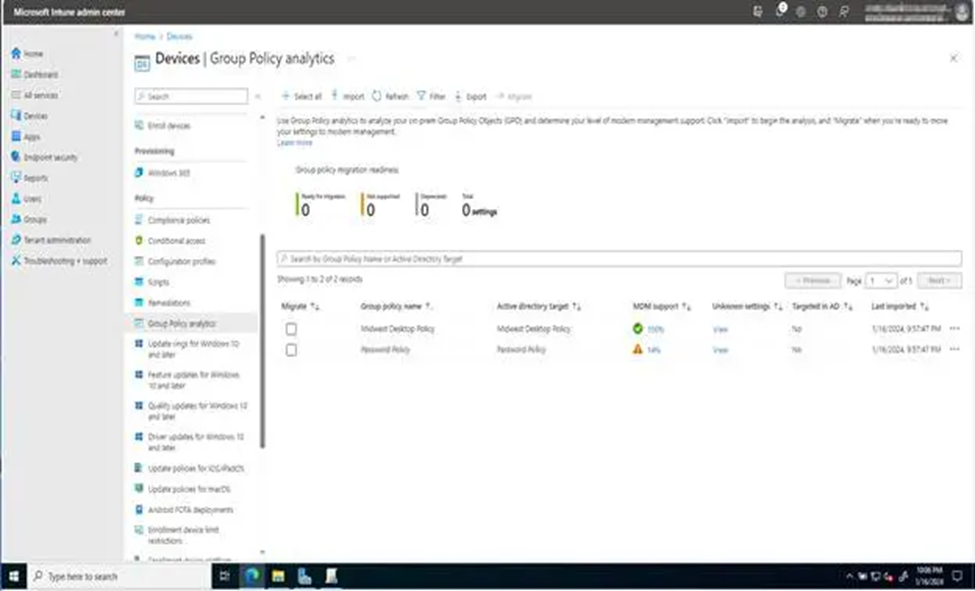
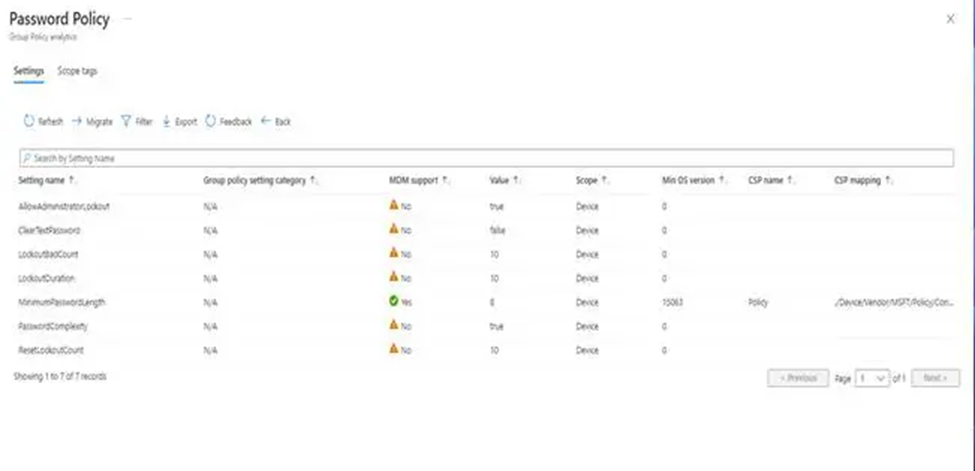
8. Once we’ve imported those, your Group Policies will appear on the screen. In this situation, we’ve included both the Midwest Desktop Policy and the Password Policy. We can see that Midwest Desktop Policy fully supports MDM, which implies that all GPO settings may be converted to CSP.
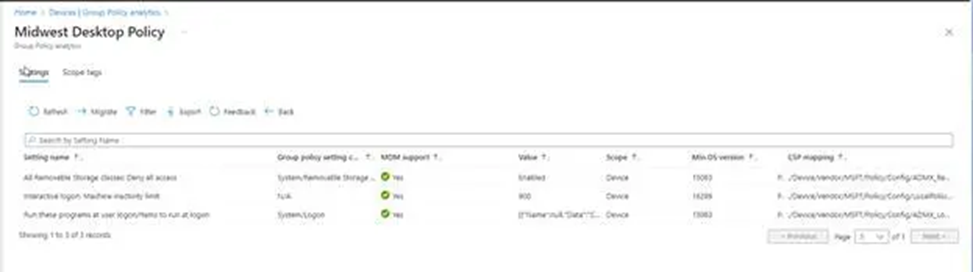
9. Click 100% under MDM Support to learn more about the policies that may be moved. You may see the minimum operating system (OS) version required, the CSP Mapping (which displays the OMA-URI route for the on-premises policy), and other settings-related information.
10. After clicking on 14% under MDM Support, I’m taken to GPO Analytics, which doesn’t produce outstanding data. The reason we see “No” under MDM support is because these GPOs do not have settings that can be converted into MDM settings.
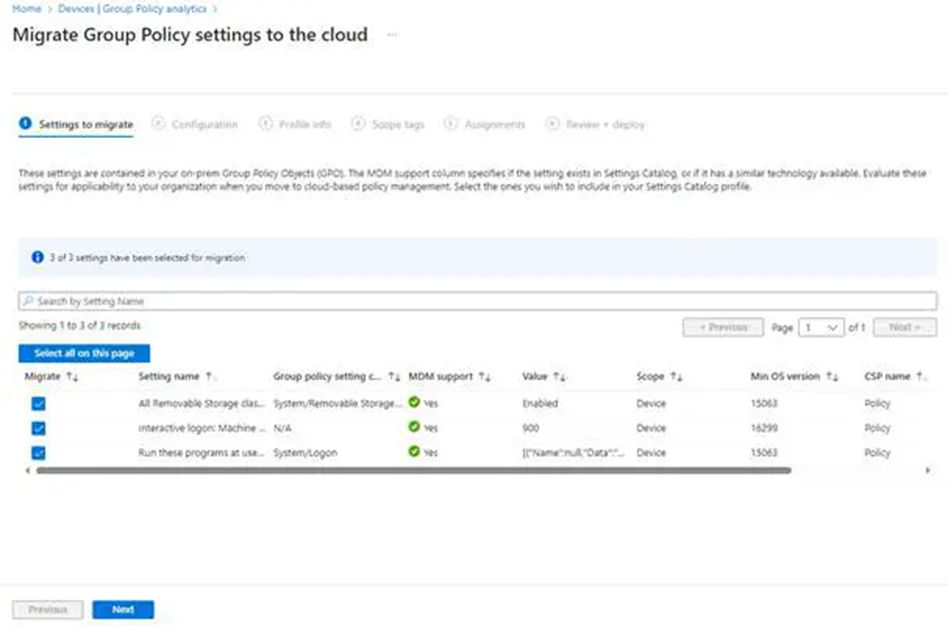
11. Return to Group Policy Analytics and choose the GPO with 100% MDM support, then select Migrate.
12. Once you click migrate, you will be sent to the following screen, where you may select all of the settings you wish to move to Intune.
Note: You should test these settings with a trial group before migrating and activating them in your environment.
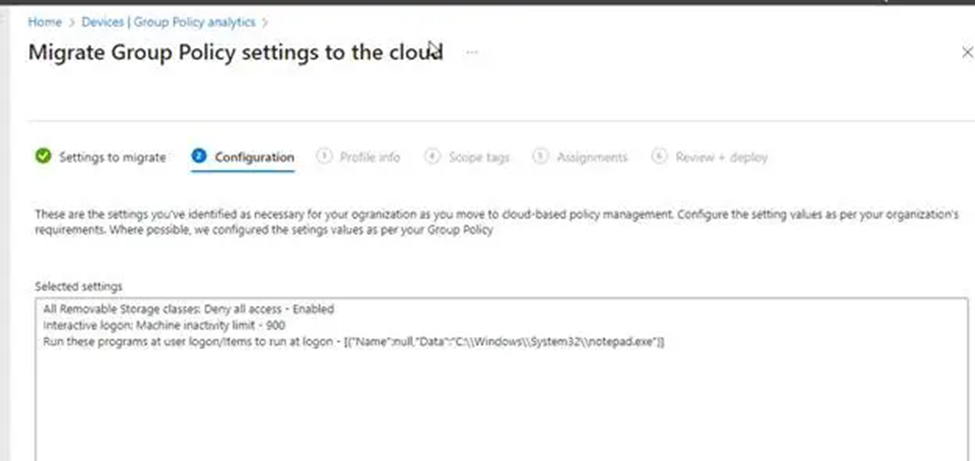
13. Next, on the settings page, we’ll see where GPO Analytics has set catalogue policies based on our imported GPOs.
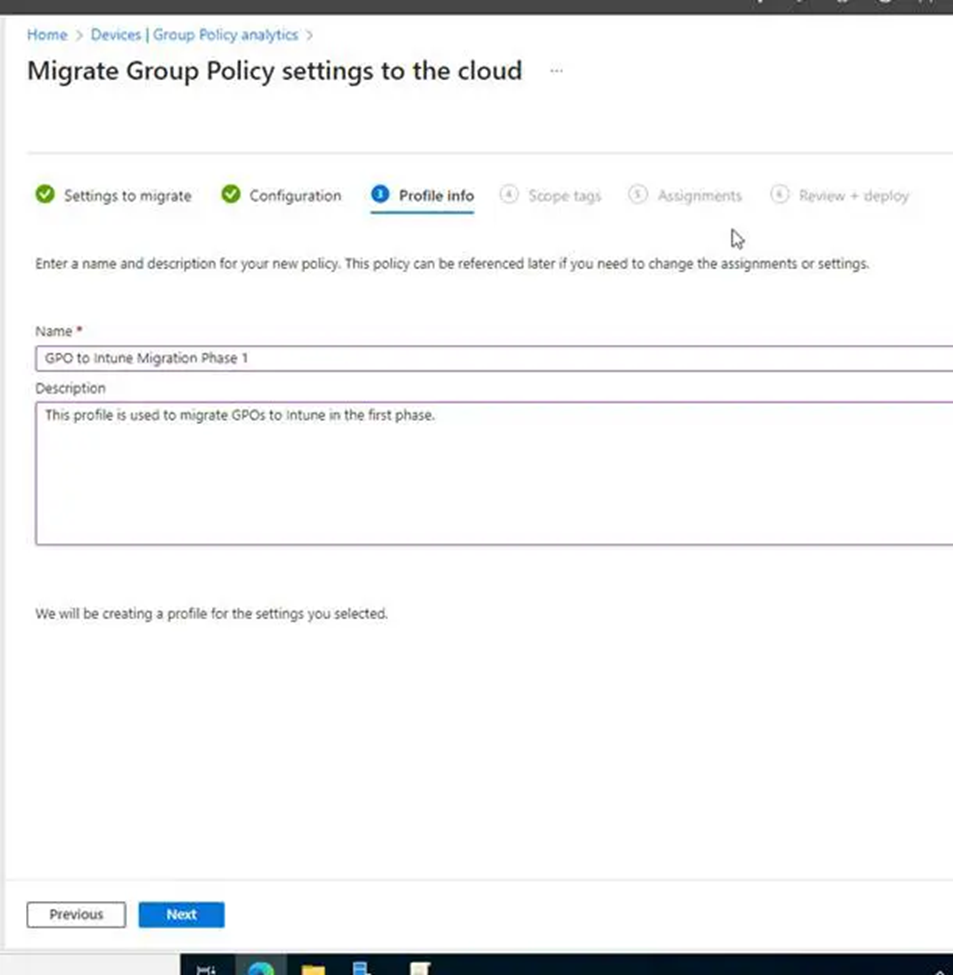
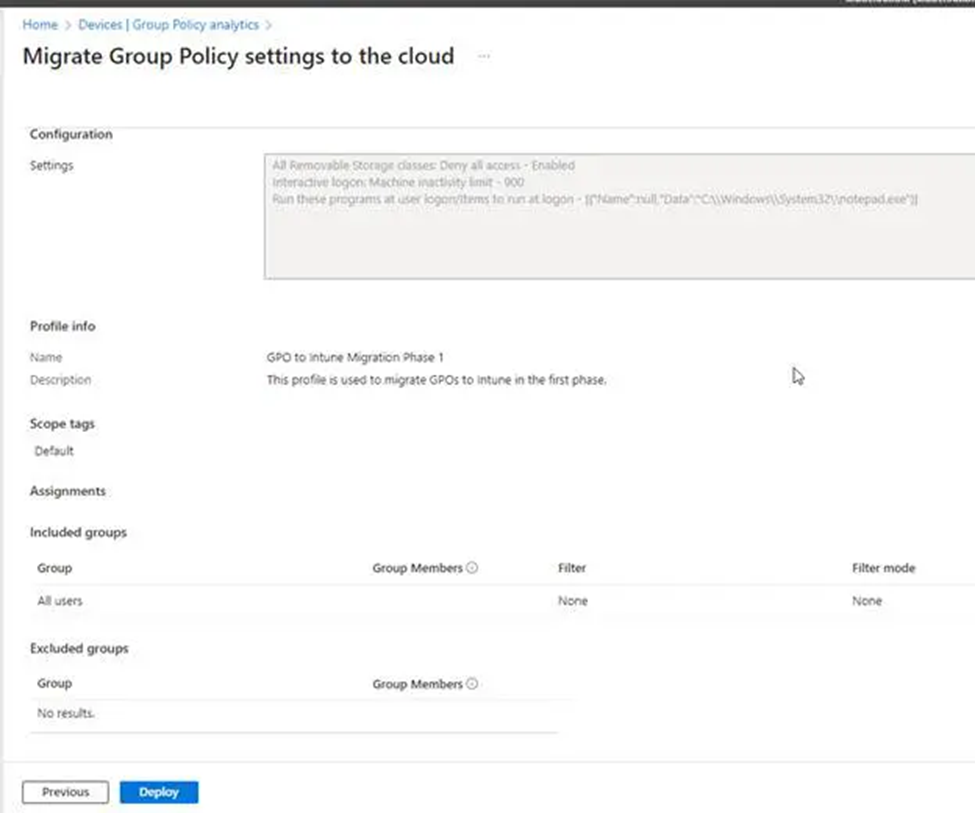
14. The following settings will take us to the Profile details page, where we may name and describe this migration for future reference. Click Next to proceed.
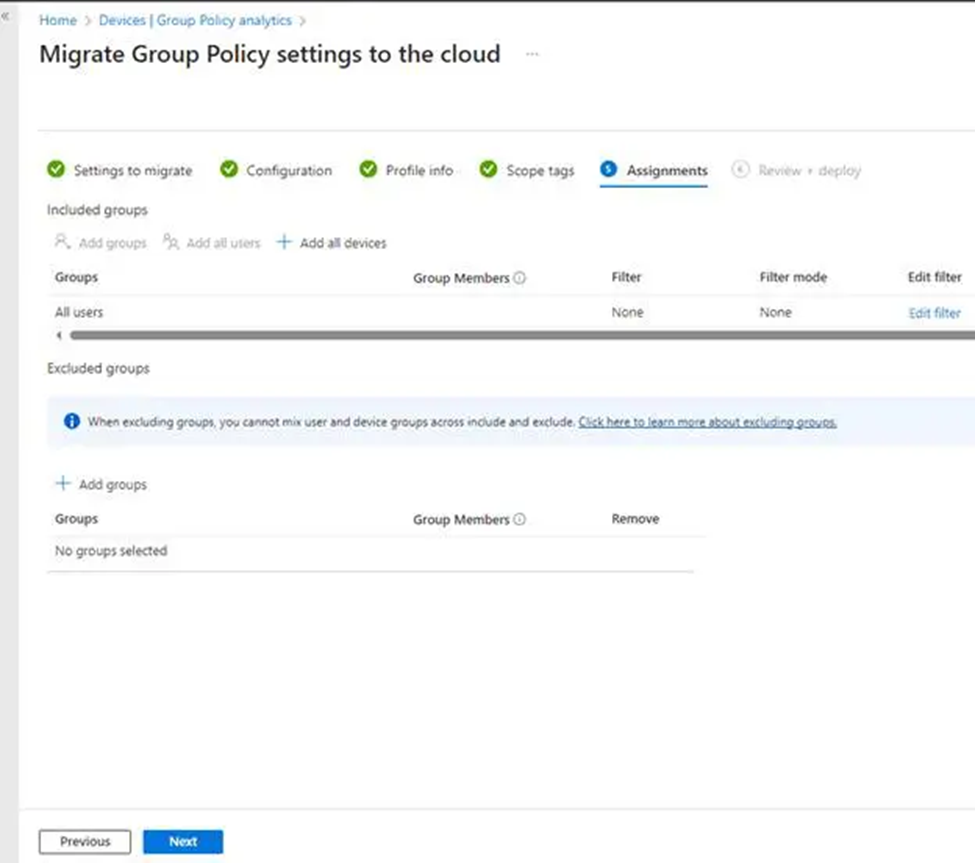
15. We didn’t have any scope tags, so click Next and go to Assignments. Here, decide who gets these settings. you can pick Add all users; however, keep in mind that you should test this before deploying it to your whole system. Click Next to review your migration.
16. Review and verify that everything appears to be in order, then deploy when ready.
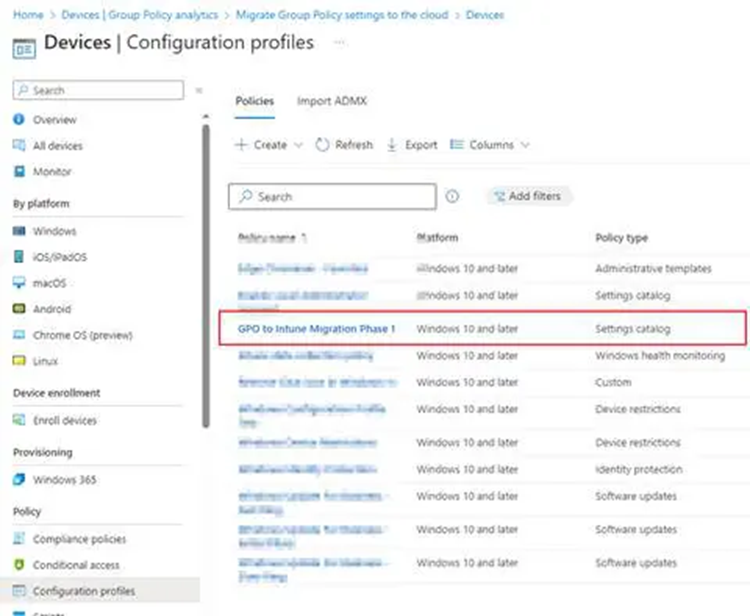
17. After deployment, we can see that our GPO migration is now listed in the Configuration Profile under the profile name we assigned it before. The settings also moved correctly.
Device Compliance Policies in Intune
Policies for intune compliance are separated into two categories:
Compliance policy settings are tenant-wide customizations that function similarly to a built-in compliance policy that each device gets. The settings for compliance policies determine how the policy operates in your Intune environment, including how to handle devices that don’t have a specific device compliance policy assigned to them.
Device compliance policies are separate collections of platform-specific rules and settings that you apply to groups of users or devices. Devices report the status of device compliance by analyzing the policy’s requirements. One or more noncompliance-related actions may follow a noncompliant status. Microsoft Entra Conditional Access control may also use that status to prevent that device from accessing organizational resources.
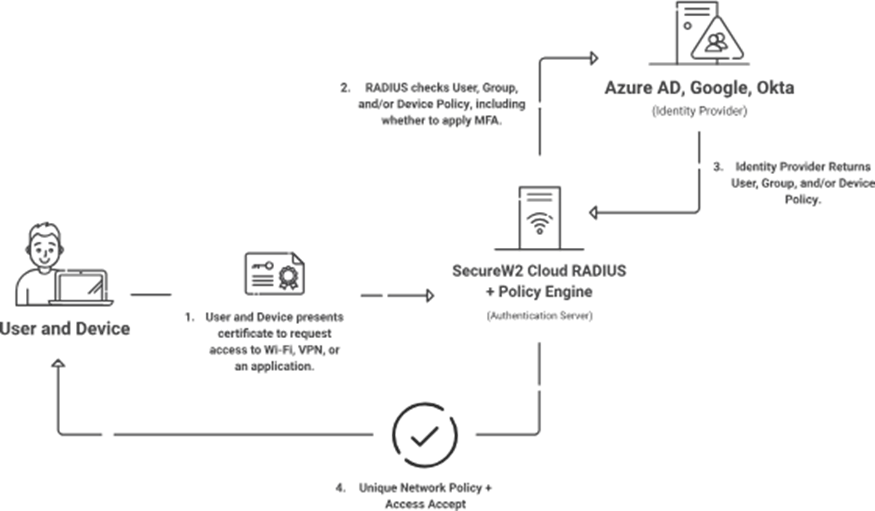
Simplifying Secure Wi-Fi Deployment with SecureW2
Migrating your network to RADIUS authentication and auto-deploy Wi-Fi settings using Group Policy may improve security and manageability. Following the procedures provided in this tutorial will help you smoothly transition to a more secure and efficient network architecture. SecureW2 supports organizations with cloud migration with our managed PKI and Cloud RADIUS, which integrate smoothly with various MDMs, including Intune. We also make setting up and administering RADIUS Wi-Fi deployments easier, ensuring your network is safe and manageable.
Contact us now to learn more about seamless migration and secure WiFi implementation.