Passwords have repeatedly proven ineffective in securing organizational networks, as they can be easily stolen or duplicated to conduct over-the-air attacks. Password-based network security leaves your data and networks vulnerable to MITM and brute force attacks, which could result in data and credential theft, resulting in loss of money and goodwill.
EAP-TLS lets you leverage digital certificates instead of passwords, eliminating the risk of data and credential theft. Digital certificates are phishing-resistant and cannot be stolen or duplicated. SecureW2s PKI solutions integrate seamlessly with Meraki Access Points to provide a comprehensive EAP-TLS-based secure network. It is equipped to distribute digital certificates for all the endpoints in a network seamlessly for effective 802.1X authentication.
Transitioning from password to certificate-based authentication has never been easier, with many of our customers getting it done in less than a couple of hours. First, we will highlight the high-level configuration steps we will cover in this guide, then cover each step in more detail.
- Configuring SecureW2 PKI Services
- Configuring and managing a PKI is difficult. This is why we designed our PKI Services to be completely turnkey. Everything that’s required for EAP-TLS (Certificate Authorities, CRL, Management Software.. etc) is created using our simple Getting Started Wizard.
- Identity Provider Integration
- SecureW2 Integrates with every major LDAP and SAML IDP to authenticate users and enroll them for certificates. Below are some of our integration guides on how SecureW2 integrates with Identity Providers:
- Active Directory / LDAP
- Google Apps
- Active Directory Federation Services
- Okta
- SecureW2 Integrates with every major LDAP and SAML IDP to authenticate users and enroll them for certificates. Below are some of our integration guides on how SecureW2 integrates with Identity Providers:
- Getting Users Enrolled for Certificates
- Set up Onboarding SSID for BYOD Self-Service Certificate Enrollment
- Users can easily enroll themselves for 802.1x and certificates and get their devices configured for secure network access using the JoinNow Suite; our Best-in-Class Onboarding Software. They can use it to set up their devices from the comfort of their own home, or you can configure an Open SSID to redirect users to the JoinNow Onboarding Solution to ensure the enrollment process goes off without a hitch.
- Using Gateway APIs to Auto-Enroll Managed Devices for Certificates
- Rather than manually enrolling every managed device for a certificate, use our Managed Device Gateway APIs to automatically enroll all your managed devices, through any major MDM software, for machine and/or user certificates.
- Set up Onboarding SSID for BYOD Self-Service Certificate Enrollment
- Configuring the RADIUS Server
- Integrating SecureW2 PKI Services with a RADIUS Server
- Our PKI services integrate cleanly with all major RADIUS servers. We can work with your existing infrastructure to make implementation totally painless. No RADIUS infrastructure? No problem, SecureW2 comes built in with our Cloud RADIUS. Click here to read more about our RADIUS Solutions.
- Integrating a Meraki AP with a RADIUS Server
- Once you’ve figured out your RADIUS set up, the SecureW2 JoinNow Suite can configure your RADIUS server to integrate seamlessly with Meraki AP. Below is a step-by-step guide.
- Integrating SecureW2 PKI Services with a RADIUS Server
Configuring an Open SSID for Self-Service Certificate Enrollment
Setting up EAP-TLS authentication on your 802.1x network is easier if you create an Onboarding SSID, especially for new devices that have previously never connected to a network. When users enroll for a certificate on the Onboarding SSID, they are redirected to the SecureW2 landing page.
In lieu of using an Onboarding SSID, users can use mobile data to enroll for a certificate when using applicable devices. From here, the OS is detected and a client is deployed that is specific to the OS. The client then configures the device by installing the Wi-Fi certificate and appropriate network settings required to authenticate via EAP-TLS. Lastly, their device is migrated to the Secure SSID.
In the past, the process of loading certificates into users’ devices was incredibly difficult, but the SecureW2 onboarding process requires just a few steps. It takes the burden off the IT department to onboard every network user, but still allows them to monitor the Wi-Fi onboarding process.
Once certificate authentication is complete, users can automatically connect to the network without the hassle of password-related disconnects caused by password change policies.
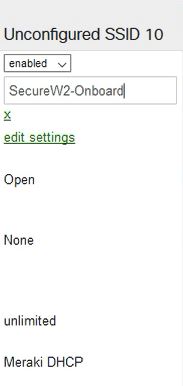
Configuring your SSIDs
- Login to the Meraki Dashboard
- After selecting your Organization and your Network, select Wireless to configure your SSIDs
- To create a new SSID, select an unconfigured SSID and switch it from disabled to enabled
- Rename the SSID to configure it, and click Save Changes
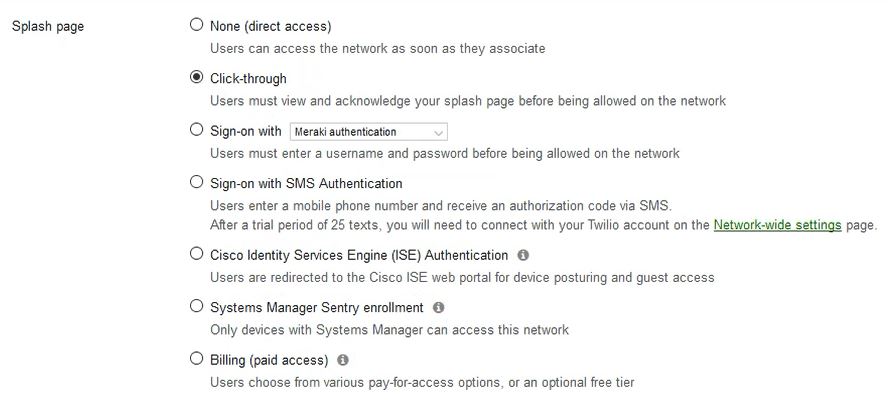
Configure Access Point to use Splash Page
- Select Wireless again, and choose Access Control
- Set the Network Access to Open (no encryption)
- Under the Splash Page section, select Click-through
This process will set the redirect to go to the SecureW2 landing page.
Configure a Walled Garden
When implementing a BYOD system, it’s vital to keep corporate data and personal data separate and protected. A proven method has been utilization of a walled garden. Instituting a walled garden keeps corporate data stored in a secure application that is separated from personal data. This creates insurance for the corporation that their sensitive data will not be breached.
For an Onboarding SSID, you need to allow onboarding related resources. For example, the MultiOS solution uses an Android application to configure Android devices for WPA2-Enterprise, so we need to allow access to the Play Store on our Onboarding SSID.
Another example is the Apple CNA can get in the way of WPA2-Enterprise configuration. The CNA is prompted when an Apple device can’t contact certain Apple servers, so we need to allow contact in order to prevent the CNA from popping up.
We control what resources can be accessed on the Onboarding SSID by using a Walled Garden. It allows network administrators to control access to certain sites and applications, steering network users away from potentially harmful situations.
To configure the Walled Garden:
- Select Wireless again
- Go to the Firewall & traffic shaping settings, and make sure your SSID is selected
- Under the Layer 3 firewall rules section, you will need to:
- Input the rules that allow the firewall through to SecureW2 resources (See Chapter 2: Firewall Rules in the JoinNow MultiOS Deployment Guide in the management portal)
- The last policy you need to add is to deny 0.0.0 to clarify to the firewall that someone can’t be abusing this open SSID just to access the internet
- Save Changes
Setting up the redirect to the SecureW2 landing page
The last thing you’ll need to configure is the redirect. Under Wireless:
- Click on Splash Page
- Double check that the SSID is the same as the one you configured earlier
- In the Custom Splash URL section, input the Onboarding Landing Page URL from SecureW2, and click Save Changes
Now you have your Onboarding SSID all configured! In the next section, we’ll look at how to integrate SecureW2 RADIUS with Meraki APs.
Integrating the SecureW2 RADIUS with Meraki Access Points
Now that we’ve configured the onboarding SSID that will enroll users for a certificate, we need to setup the secure SSID. This SSID needs to be configured for EAP-TLS WPA2-Enterprise authentication. It also needs be integrated with a RADIUS server, which in this case will be the SecureW2 RADIUS server, that will authenticate the users’ certificate and authorize them for network access.
Configuring your SSIDs
- Create another SSID by selecting an un-configured SSID and then enabling it
- Rename the SSID (make sure it is the same name as the SSID in the Network Profile)
- In your Network Profile, when you click Edit, you should see the SSID section, and the name you entered should match
- Scroll down and click Save Changes
Setting up the RADIUS Information
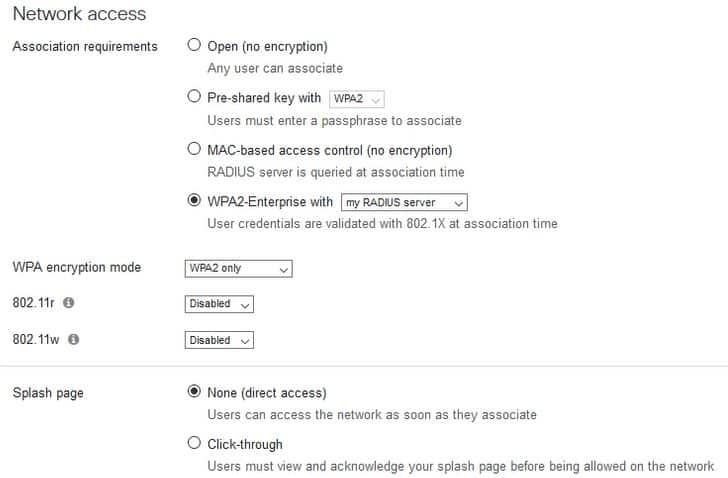
Now, you need to enter in the RADIUS information:
- Under Wireless, select Access control
- Under Network access change it from the default value of Open (no encryption) to WPA2 Enterprise with my RADIUS server
- For the WPA encryption mode, select WPA2 only
- In the Splash page section, leave it set to None (direct access)
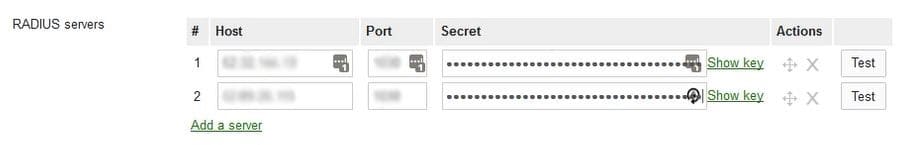
You can find the details about Your RADIUS when you go to AAA Management and AAA Configuration. Here you will see a Primary IP Address, Secondary IP Address, Port Number and a Shared Secret.
- Under RADIUS Servers, click the green link to Add a server
- Enter in the Primary IP Address, Port Number, Shared Secret respectively
- You will need to perform the same steps for the Secondary IP Address by entering the Secondary IP Address, Port Number, Shared Secret
- Scroll down and click Save changes
And that’s it; you’re on your way to a more secure wireless network!
Leverage SecureW2s PKI Solutions For a Robust EAP-TLS Network
An EAP-TLS digital certificate-based authentication eliminates the risks of over-the-air credential theft that could arise from a password-based network. EAP-TLS also requires mutual authentication, i.e., the client and the server need to authenticate themselves through their certificates, preventing them from accessing spoofed access points. However, digital certificates need a PKI to manage the whole process of certificate distribution, renovation, and renewal.
SecureW2’s Connector PKI makes managing certificates on an organizational network easy. It integrates with all major MDMs and identity providers to seamlessly distribute certificates to managed devices. SecureW2s JoinNow MultiOS lets you distribute certificates to unmanaged devices accessing your network to eliminate the chances of misconfiguration, which would otherwise lead to connecting to a spoofed endpoint, putting the whole network at risk of data theft.
Finally, SecureW2s CloudRADIUS lets you leverage EAP-TLS with any Access Point, including Meraki, for a digital certificate-based authentication for a secure, user-friendly, efficient network. If you’re ready to start, SecureW2 has affordable solutions for organizations of all shapes and sizes. Click here to learn more about our pricing.
FAQ
Yes, Meraki supports RADIUS.
Meraki devices are listed as a supported vendor for WPA2-enterprise with Dynamic RADIUS. With Meraki, devices can send RADIUS Access requests and accounting messages via proxy and forward the messages to the RADIUS server. Some attributes like Username, NAS-IP address, NAS-Port, and Called-Station ID are in the Access-Request messages sent from the Meraki Access Point to the client RADIUS server.
The commonly used EAP configuration in a Meraki Cloud RADIUS configuration is the PEAP-MSCHAPv2. However, the Meraki platform also supports an EAP-TLS configuration that supports digital certificates.
To configure Radius authentication with Meraki access point:
- Log into the Meraki dashboard. Go to Wireless-Access Control.
- Under Network Access, change it to WPA2 Enterprise with “my RADIUS server” from the default value Open (no encryption).
- Select WPA2 for WPA encryption mode.
- Leave the default option to None (direct access) on the Splash page.
- Next, we set up the RADIUS Information
- Add RADIUS in the RADIUS server section.
- Add Primary and Secondary IP addresses, Port numbers, and shared secrets for RADIUS details.
- Save changes.
These steps will ensure you have set your Meraki Access points for WPA2-Enterprise 802.1X authentication. This will provide a more secure network that supports EAP-TLS configuration for passwordless authentication.
CloudRADIUS is vendor-neutral and can integrate with any Access point, including Meraki. RADIUS timeout specifies the number of seconds a RADIUS server waits for a response before moving on to the next RADIUS server. You can set a custom timeout in the Meraki dashboard; the default maximum timeout is 10 seconds.
CloudRADIUS can also enforce real-time user and device lookup against identity providers like Google, Okta, and Azure, to name a few. With RADIUS-based authentication on a Meraki Access Point, it can be designed to provide robust 802.1X passwordless authentication.
The RADIUS server, or the AAA server, plays a critical role in 802.1X Wi-Fi authentication. It authenticates users, authorizes network access, and monitors network activity. It acts as a “security guard” to the network, checking the credentials of every user or device. Access to the RADIUS server is granted only if the credentials or certificate are valid; otherwise, access is denied.
The RADIUS server can also enforce policies for appropriate access control that determines who gets access to what on a network. It helps you segment users based on their groups into separate VLANs for granular access control and monitoring of users and devices. A CloudRADIUS server is best used with digital certificates. A digital X.509 certificate has unique attributes like email ID, username, device ID, MAC address, and user groups. A device with a certificate presents itself to the RADIUS server, which is cross-checked with the identity provider before applying the relevant policies. You can also authenticate users from different organizations to the RADIUS.
Thus, a RADIUS server ensures that only authorized users can access the network, are set in proper VLANs as per access policies, and are monitored accurately. Our CloudRADIUS integrates with Meraki Access Point for EAP-TLS authentication for superior digital certificate-based 802.1X authentication for superior network security.
CloudRADIUS provides enhanced security by enabling 802.1X authentication, which encrypts every user session to prevent attacks like MITM and credential theft and secures confidential information. RADIUS servers also verify and re-verify information whenever a user tries to connect to a network to limit damage by intruders. CloudRADIUS is cloud-based, eliminating the need for on-premise RADIUS servers, thus reducing costs and maintenance activities.
SecureW2s CloudRADIUS is vendor-neutral and integrates with all major MDMs and identity providers for real-time authentication and user look-up without needing forklift upgrades. It is built for WPA2-Enterprise with EAP-TLS authentication that facilitates digital certificate-based authentication for enhanced user experience and a secure wireless network. The CloudRADIUS is easy to set up with a secure SSID for WPA2-Enterprise and out-of-the-box deployment.
With CloudRADIUS, you can also set real-time access policies for access restrictions adhering to security and compliance norms. Overall, it enhances network posture and provides a better user experience for a fraction of the cost of setting up an on-premise RADIUS server.
RadSec is an 802.1X transport protocol for transporting RADIUS packets through Transmission Control Protocol (TCP) and Transport Layer Security (TLS). It secures communication between a RadSec client and server through an encrypted TLS tunnel, resulting in a more secure connection than a RADIUS server.
RadSec improves the security of Meraki wireless networks by encrypting RADIUS packets, preventing man-in-the-middle attacks, and ensuring that data transmissions are secure even when connected to insecure networks or during roaming. In environments where devices transition between different networks, RadSec facilitates secure hand-offs, reducing the risk of exposure during network switches. RadSec server certificates can be validated by clients, preventing devices from connecting to the wrong server and exposing themselves to potentially hostile networks.