Can I Use OpenLDAP with a Cloud RADIUS?
Network security is crucial for organizations today, and an important part of that security is the method of user authentication. Before cloud computing became prevalent, the LDAP protocol was a popular choice for authenticating and authorizing users for on-premise networks.
The question is – Has LDAP stood up to the test of time?
What is LDAP?

The Lightweight Directory Access Protocol, or LDAP, is a software protocol that provides user authentication for network resources. An LDAP server references a directory, containing information about users, attributes, and group policies. This technology made it easier for network admins to manage network resource access, in turn protecting company data.
Active Directory (AD), the most popular directory service, uses LDAP to communicate. OpenLDAP is often used in non-Windows systems.
What is OpenLDAP?
Just like AD, OpenLDAP was created due to the popularity of LDAP as it’s an open source implementation of LDAP. While AD added Kerberos and became the standard commercial directory service for Windows environments, OpenLDAP went on to be the leader in open source directory services.
OpenLDAP Use Cases
OpenLDAP is mostly used for technical solutions, like connecting users to Linux servers and applications. Because of LDAP’s flexibility, admins have configured many different Linux-based applications to authenticate via LDAP.
- Atlassian Jira & Confluence
- Docker
- Jenkins
- Kubernetes
OpenLDAP Drawbacks
Despite its overwhelming popularity among IT professionals, OpenLDAP can be challenging to implement.It’s not a feature that you can simply plug in. Implementation is a comprehensive and laborious process that involves determining what you need it to do and how to configure it on your network.
The benefits of OpenLDAP might also be a drawback for some. Due to its flexibility, OpenLDAP is more labor intensive for the IT team. Often, organizations will need a properly trained staff member solely dedicated to managing OpenLDAP.
OpenLDAP can be used as an identity provider, though that is also a heavy burden on the IT administrators. Admins would need to connect OpenLDAP to Windows and Mac systems and applications, both requiring their own authentication protocols.
Struggles of LDAP and On-Prem Legacy Systems
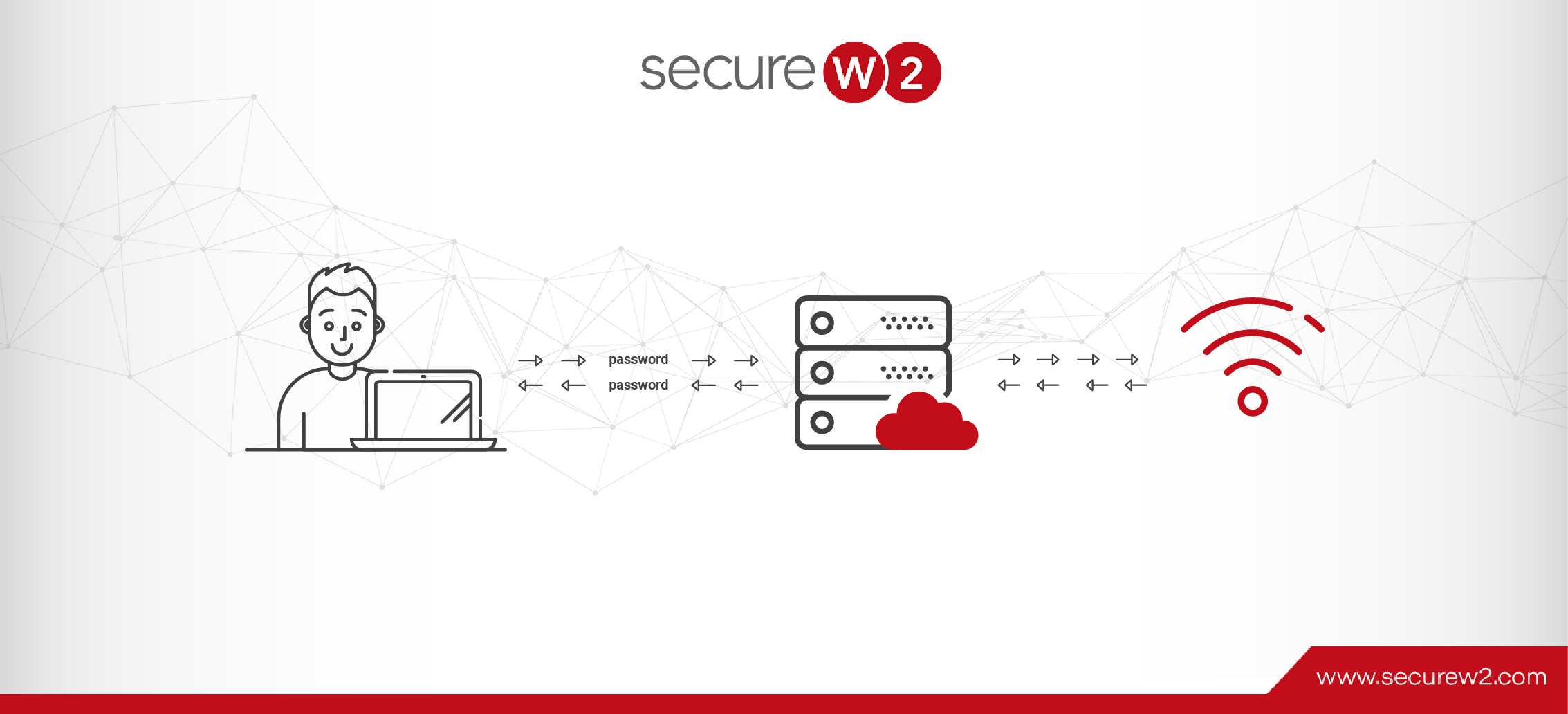
The introduction of the cloud meant trouble for LDAP systems.
For one, Azure AD doesn’t support LDAP, instead recommending Windows Admins configure Azure AD Domain Services (Azure AD DS) to connect with LDAP. It’s an incredibly laborious task. LDAP won’t be at its full potential, and traffic is unencrypted by default.
Another weak point is credential-based authentication, which is used by most infrastructures built around LDAP. Tasking end users with creating their own unique passwords is more secure than a shared password written on the whiteboard, but it’s still not a reliable security measure. Passwords are not a good source of identification because sharing passwords is common among colleagues. Employees can also be tricked into giving away their credentials via a phishing email, which have skyrocketed since the Covid-19 pandemic began.
Credential-based authentication protocols offer subpar security and user experience. EAP-TTLS/PAP, for example, doesn’t encrypt credentials, just the tunnel during a client-server connection. That tunnel is rendered useless by a man-in-the-middle attack. PEAP-MSCHAPv2 does encrypt data shared in the connection, but there’s a vulnerability in its encryption method which can be exploited.
Replace LDAP Credential Authentication with Certificates
Instead of authenticating users with credentials via LDAP, admins should use digital certificates. Certificates are better for identification purposes because they can be configured with user attributes and permissions, equipped to their devices, and track user network activity.
Provisioning a certificate to every network device is not a simple task because admins will need a Public Key Infrastructure (PKI), the framework for implementing and managing certificates. Luckily, there are turnkey Managed PKI solutions that improve network security without making management more complex. Admins can set up automatic certificate enrollment for all network devices using an onboarding software.
Cloud RADIUS and EAP-TLS Authentication
RADIUS was developed to centralize authentication for many different network devices and services, including routers, access points, switches, Wi-Fi, and VPN.
SecureW2’s Cloud RADIUS is an improved iteration of RADIUS with cloud capabilities and stronger network security. Instead of credentials, Cloud RADIUS is built around certificate-based authentication. Users are authenticated with certificates that are customized with user attributes and permissions. Once a certificate is created, it’s then distributed to a user’s device, serving as their identity.
Certificate-based EAP-TLS authentication eliminates over-the-air credential theft because user credentials are encrypted within the certificate. Both clients and servers are equipped with certificates, making them easier to identify.
Cloud RADIUS doesn’t require any forklift upgrades and can be set up in less than an hour. It comes with built-in redundancy so organizations can handle any high traffic events.
Secure LDAP Authentication with Cloud RADIUS
SecureW2 and Cloud RADIUS can work with LDAP, but it’s much easier to ditch LDAP in favor of SAML-based technology and completely migrate your network to the cloud. Cloud RADIUS improves RADIUS, strengthening network security and providing a better user experience. No more passwords, no more over-the-air credential theft.
Cloud RADIUS is available for organizations of all sizes at an affordable price, making it more cost-effective than on-prem legacy LDAP systems.