Can I Use Azure With A RADIUS Server?
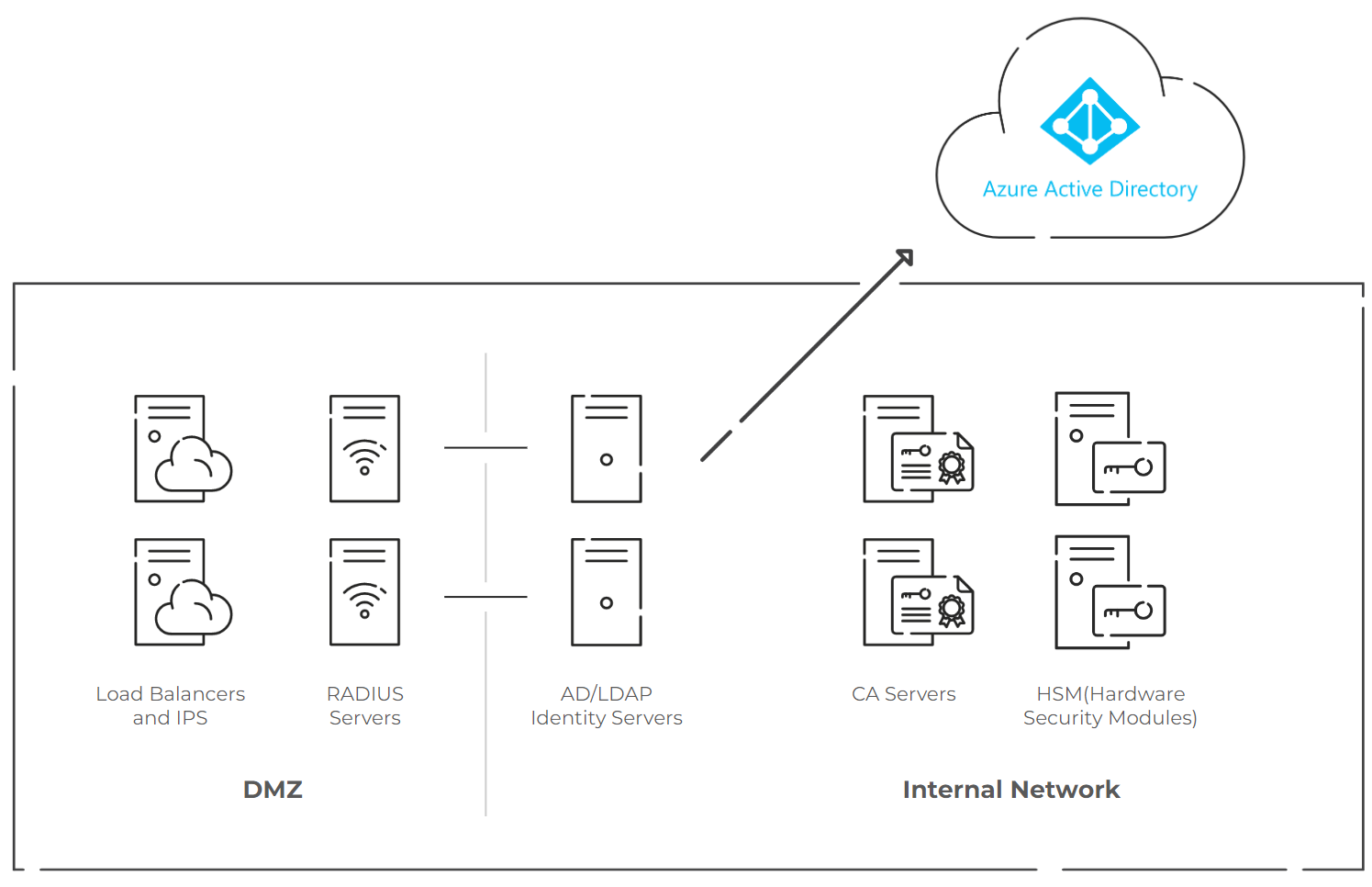
A RADIUS server is essential to network security since it is a gatekeeper, requiring user and device authentication before allowing access to wired networks, VPNs, or Wi-Fi. To carry out this function, an identity database, like Azure AD (Entra ID), one of the most popular cloud-based identity providers available today, must be connected to the RADIUS server.
Does Azure AD (Entra ID) have compatibility with a RADIUS server? The answer is simple: yes. Azure AD can easily interface with external RADIUS solutions, even though it lacks RADIUS capabilities by default. Organizations must consider employing on-premises technologies like Network Policy Server (NPS) or more contemporary cloud-native alternatives like Cloud RADIUS.
This article explains the ideal setup procedures, how RADIUS authentication functions with Azure AD (Entra ID), and why cloud-based solutions offer a more secure and scalable alternative. For WPA2-Enterprise Wi-Fi or other network access requirements, this article will demonstrate how to combine Azure AD with RADIUS.
How Does RADIUS Authentication Work with Azure AD (Entra ID)?
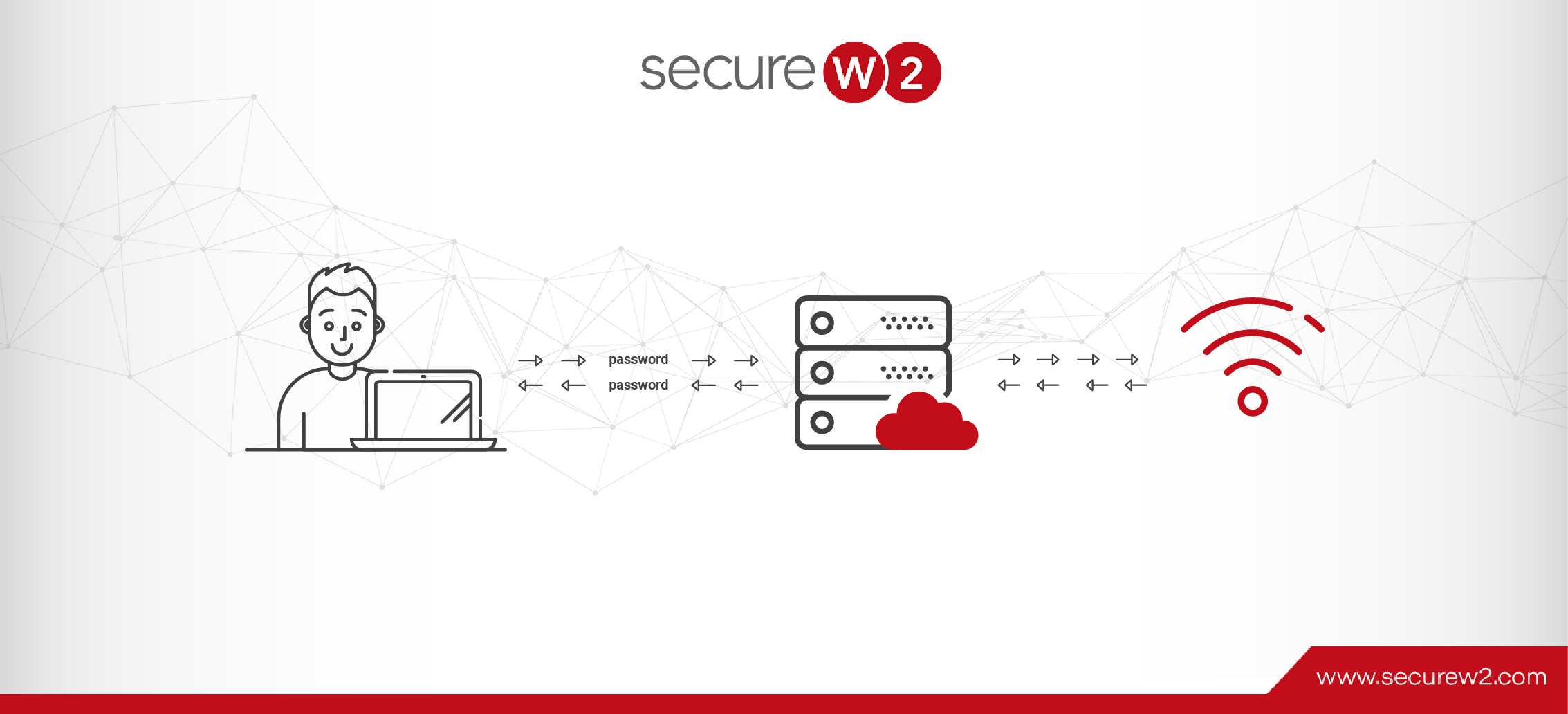
Integrating a RADIUS server with Azure AD (Entra ID) enables organizations to use cloud-based identity management to provide secure network access. RADIUS (Remote Authentication Dial-In User Service) server processes authentication requests from Radius clients and verifies users and devices attempting to access network devices (such as Wi-Fi access points) in identity platforms such as Azure AD, simplifying authentication requests.
How Does RADIUS Authentication Work with Azure AD (Entra ID)?
User Connection Request
When a user seeks to access a network resource, such as WPA2-Enterprise Wi-Fi, the network device sends an authentication request to the RADIUS server, which includes user credentials or certificates.
Identity Verification using Azure AD
The RADIUS servers pass this request to Azure AD (Entra ID), which validates the credentials or certificate against its directory. This step guarantees that the user is recognized by Azure AD, which centralizes identity management and maintains user status up to current throughout the organization.
Access granted or denied
Based on Azure AD’s verification response, the RADIUS servers either grant or deny the access requests. Access is given if the identification is legitimate and the permissions meet the organizational norms; otherwise, the user is barred from using the network.
Enhanced Security with Certificates
Using certificates for RADIUS authentication instead of passwords improves security since certificates are more difficult to steal or copy. Certificate-based authentication decreases the risk of credential theft and the threat of over-the-air password attacks in organizations that use Azure AD.
Dynamic Policy Enforcement with Azure AD (Entra ID) and Cloud RADIUS
Cloud RADIUS, our managed RADIUS solution, performs one extra step during RADIUS authentication when integrated with Azure AD. This extensive integration enables real-time identity verification and dynamic policy enforcement during authentication.
For instance, Cloud RADIUS can dynamically apply role-based policies and check user credentials or certificates against Azure AD (Entra ID). If a user’s status changes, such as when they are deactivated or allocated to a different role in Azure AD, their network access rights are immediately changed. This strengthens security and lowers administrative costs by guaranteeing that access limits always reflect the most recent organizational policy and user status.
Organizations may create a highly secure, adaptable network environment by combining Cloud RADIUS’s certificate-based authentication and dynamic policy application with Azure AD’s strong identity management. This integration promotes cloud-first initiatives by removing on-premise hardware requirements, providing scalable solutions, and simplifying Wi-Fi and network access restrictions.
Choosing an On-Premise or Cloud-Based RADIUS Solution for Azure AD (Entra ID)
Azure AD (Entra ID) can integrate with various external RADIUS systems. There are two typical approaches:
Network Policy Server & Entra ID
NPS is a Windows Server role that may function as a RADIUS server; however, integrating NPS with Azure AD (Entra ID) necessitates a hybrid configuration. To synchronize Azure AD with your on-premises Active Directory (AD) or Azure AD Domain Services (AD DS), you must first utilize Azure AD Connect. This hybrid arrangement is complicated and requires constant maintenance, making it less suitable for purely cloud-based settings.
Cloud RADIUS Alternatives to NPS
Cloud-native RADIUS services, such as SecureW2’s Cloud RADIUS, provide a smooth, contemporary integration with Azure AD (Entra ID). These solutions eliminate the need for on-premises servers and complicated sync setups, allowing seamless interaction with Azure AD. Organizations may create secure, flexible, and scalable network authentication without hardware or maintenance using a cloud RADIUS server.
How Do You Set Up a RADIUS Server for Azure AD (Entra ID)?
Configuring Cloud RADIUS for Azure AD (Entra ID)
Cloud RADIUS streamlines and improves the integration of RADIUS authentication with Azure AD (Entra ID). This is a concise summary of the procedure and its principal advantages:
Why Choose Cloud RADIUS for Azure AD?
Streamlined Deployment: Unlike traditional RADIUS solutions like NPS, Cloud RADIUS does not require on-site infrastructure or intricate synchronization tools. It uses Azure AD natively for user and device authentication, minimizing setup and maintenance burdens.
Augmented Security: Cloud RADIUS employs Azure AD’s OAuth API and incorporates SecureW2’s sophisticated Policy Engine. This facilitates dynamic real-time authentication and policy enforcement contingent upon user and device state, assuring a highly secure network.
Protocol Versatility: Cloud RADIUS accommodates several authentication protocols, including:
- EAP-TLS (certificate-based): The most secure approach, advised for contemporary organisations.
- PEAP-MSCHAPv2 (password-based): Beneficial for older or heterogeneous device settings.
Overview of the Setup Process
To set up Cloud RADIUS with Azure AD (Entra ID), adhere to these essential steps:
Create a SAML App in Azure AD:
- Register a new SAML application to facilitate the connection between Azure AD and Cloud RADIUS.
- Obtain the SAML information from Azure AD for integration purposes.
Configure SecureW2 for Attribute Mapping:
- Submit the Azure AD information to the SecureW2 portal.
- Associate features such as email, display name, and group membership for inclusion in certificate-based authentication procedures.
Set Up a RADIUS Lookup Application:
- Register an extra application in Azure AD for real-time RADIUS queries.
- Generate client secrets and allocate API access for this application.
Create and Configure Policies:
- Utilise SecureW2’s Policy Engine to establish authentication and role policies.
- Classify users and implement network access limitations according to their responsibilities or devices.
Test and Publish Network Profiles:
- Disseminate the network profile to provide effortless onboarding for end-users.
- Verify authentication to guarantee a seamless connection.
Each stage necessitates particular setups in Azure AD and the SecureW2 portal. For a comprehensive tutorial, read the complete documentation: SecureW2 Cloud RADIUS with Entra ID Integration.
This procedure guarantees safe, scalable, and policy-based RADIUS authentication designed for contemporary Azure AD systems.
Best Practices for Configuring a RADIUS Server with Azure AD (Entra ID).
To guarantee safe and efficient integration, consider the following recommended practices:
Switch to EAP-TLS for Enhanced Network Security
Organizations are increasingly turning to EAP-TLS as a substitute for PEAP-MSCHAPv2 because of its superior security and reliability. EAP-TLS prevents password-based vulnerabilities using digital certificates instead of user credentials like PEAP-MSCHAPv2. Phishing, brute-force attacks, and bad user practices can compromise passwords, putting networks at risk. EAP-TLS prevents man-in-the-middle attacks by forcing the server and client to confirm their identities with certificates.
Modern networks have operational benefits from EAP-TLS in addition to security. With SecureW2, organizations may automate certificate issuing and management for employees, contractors, and visitors. It is very scalable. This makes onboarding secure and smooth without manual password resets or complex password restrictions. Enterprises managing sensitive data choose EAP-TLS because it meets PCI DSS, HIPAA, and CMMC compliance standards. EAP-TLS improves network security, simplifies management, and protects infrastructure from new threats.
Network Isolation
Ensure your RADIUS server is on the same virtual network as Azure AD (Entra ID) or any other cloud directory solution. This configuration reduces latency and network concerns, allowing for more efficient authentication operations.
Utilize Secure Encryption with RadSec
RadSec (RADIUS over TLS) encryption provides additional security. RadSec protects critical information from interception by encrypting authentication data using TLS, maintaining the integrity of your network communications.
Automate Compliance Policies
Use Azure AD’s policy framework to enforce device compliance automatically. Setting policies that ensure devices satisfy particular requirements (for example, Intune policy compliance) allows you to restrict network access to trusted users and compliant devices, improving network security.
Integrating Azure AD (Entra ID) with Cloud RADIUS provides organizations with a modern, cloud-compatible RADIUS solution that eliminates the problems associated with on-premises settings while enabling secure, policy-driven network access. This technique is appropriate for organizations seeking a scalable and secure network authentication framework in a cloud-first environment.
Why Can’t You Use NPS with Azure AD (Entra ID)?
While Network Policy Server (NPS) is a popular RADIUS server for Active Directory environments, it could be better for modern cloud setups, particularly when connecting with Azure AD (Entra ID). Here’s why using NPS for Azure AD (Entra ID) network authentication might provide more problems than solutions.
Microsoft’s on-premise RADIUS solution, Network Policy Server (NPS), is built for Active Directory deployments. It offers centralized authentication and authorization for network access and is commonly used for WPA2-Enterprise Wi-Fi or VPN connections. While NPS works well in on-premise AD setups, it has difficulties interacting with Azure AD (Entra ID), designed for the cloud.
Microsoft introduced NPS Extensions to integrate Azure AD with Network Policy Server (NPS) for limited authentication. These extensions convert Azure AD tokens into NPS-compatible format, enabling interoperability. Enforcing MFA for RADIUS requests is the typical use case, adding security to VPNs and WPA2-Enterprise networks. These extensions are helpful for MFA but are not a complete solution for Azure AD integration.
1. Hybrid Setup Complexity
Using NPS with Azure AD (Entra ID) necessitates a hybrid configuration, which includes connecting with Azure AD Connect or creating Azure AD Domain Services. Because NPS uses on-premises Active Directory to authenticate users, it cannot connect directly with Azure AD. This constraint requires administrators to manage and synchronize an on-premises AD system in addition to Azure AD, which adds significant setup complexity, continuous synchronization needs, and the need for hybrid infrastructure, all of which many organizations want to reduce by shifting to the cloud.
2. Security and Scalability Issues.
NPS, as an on-premises system, lacks the inherent security and scalability features of cloud-based RADIUS alternatives.
Vulnerability Risks: To defend against vulnerabilities, on-premises NPS servers must get periodic security patches and upgrades. Unlike cloud-based systems, NPS lacks centralized security monitoring and automatic upgrades, increasing the risk of vulnerability to security attacks.
Limited Scalability: Scaling an NPS system can be tricky since it requires extra hardware and administrative resources. On the other hand, Cloud-based RADIUS solutions may grow dynamically to meet your organization’s demands without requiring physical infrastructure maintenance.
Benefits of Using a Managed RADIUS Solution over Building Your Own
Cloud RADIUS is a cloud-optimized alternative to NPS that integrates seamlessly with Azure AD (Entra ID) and offers security, scalability, and simplicity benefits.
Cloud-Optimized
Cloud RADIUS was designed to interface seamlessly with Azure AD (Entra ID) via OAuth and SecureW2’s Policy Engine, removing the requirement for on-premises infrastructure. This direct integration streamlines the authentication process and conforms with cloud-native security policies, reducing the complexity and restrictions of hybrid systems.
Simplified Setup
Cloud RADIUS enables organizations to employ certificate-based authentication without a hybrid NPS configuration. It interfaces directly with Azure AD (Entra ID), allowing the organizations to enable secure network access with a simple setup procedure that does not require Azure AD Connect or AD DS. This setup allows for rapid deployment while reducing the need for substantial technical skills or additional on-premises equipment.
Real-time Authentication and Policy Enforcement
Cloud RADIUS provides real-time identity checks using Azure AD (Entra ID) to ensure that user access status is always current. For example, if an employee’s status changes—such as when they leave the organization or their credentials are updated—Cloud RADIUS quickly enforces these changes, offering increased protection and lowering the danger of unauthorized access.
By switching to Cloud RADIUS, organizations may receive a cloud-compatible, scalable RADIUS solution that integrates with Azure AD (Entra ID), eliminating the challenges and vulnerabilities associated with employing NPS in a hybrid cloud environment.
Streamlining Azure AD (Entra ID) Integration with Cloud RADIUS
Azure AD (Microsoft Entra ID) integrates smoothly with a RADIUS server to improve network access control, providing a secure, cloud-based alternative to traditional on-premises systems. While utilizing NPS with Azure AD is feasible, the complicated hybrid setup and continuous maintenance make it less desirable. Instead, a cloud-native RADIUS solution, such as Cloud RADIUS, streamlines the process, improves security, and enables scalability for larger organizations. With its vendor-neutral capabilities, Cloud RADIUS makes an excellent Azure RADIUS solution option.
Try Cloud RADIUS by SecureW2 now. Our simple, scalable solution provides secure network authentication, removing the need for on-premise infrastructure and easing IT management.