
Access Control Paradigms Compared: RBAC vs PBAC vs ABAC
What Is Network Access Control
Network Access Control (NAC) is exactly what it says – the implementation of access control in a restricted network. It is a paradigm of networking security tools and applications to provide robust protection by rejecting unauthorized users and devices from gaining access to private networks and secured domains.
It’s comprised of everything from physical security tokens like the Yubikey to the sprawling virtual infrastructure of public key infrastructure (PKI). NAC implementation is the process of setting up controls to identify, authenticate, and allow users to access the network at varying levels.
Advantages Of Network Access Control System
NAC is your best tool to execute a Zero Trust Network Architecture as it allows organizations to set well-defined procedures and rules to authorize and authenticate users on a network.
- An organization can use Role Based Access Control or Attribute Based Access Control as paradigms for network access control, in addition to VLANs to segregate users with similar requirements onto separate networks.
- As a network administrator, NAC would allow you to use authentication methods like Multi-Factor Authentication (MFA) in place of passwords and IP-based authentication.
- NAC tools like Public Key Infrastructure (PKI) enhance the identity context of authentication. This would make way for better identification assurance compared to passwords.
The process of determining the level of access in an organization has been evolving and has changed a lot from the 1980s to the present day. In this article, we chalk out the various access control paradigms like the RBAC, PBAC, and ABAC, then compare them to each other and talk about the best solutions to set up access-based control for your organization.
What is Role-Based Access Control
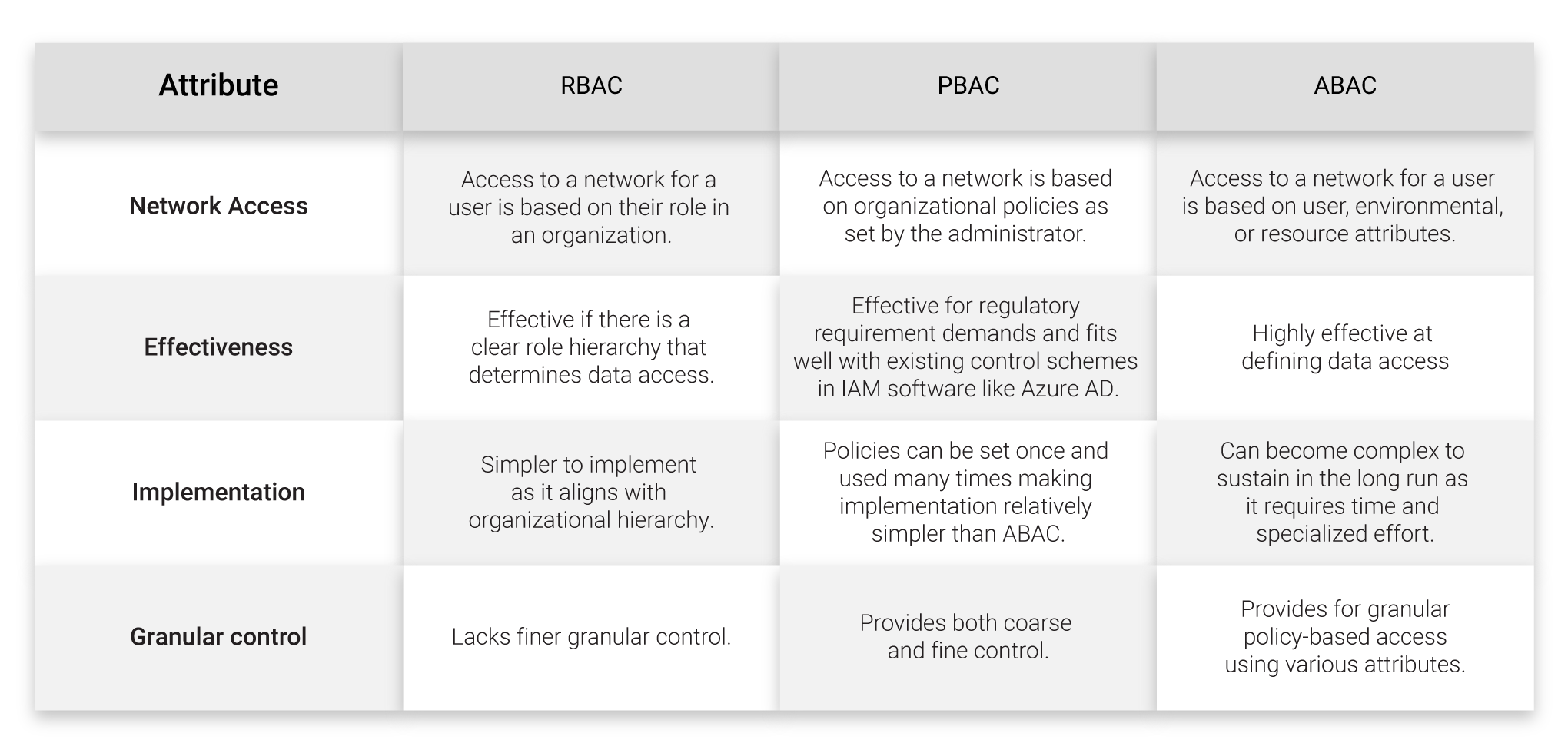
Role-Based Access Control (RBAC) assigns permissions to users based on the designated roles in an organization. An engineer should not need to access the payroll information, likewise, a payroll executive probably doesn’t need access to software source code. Restricting access to only the users who require it is an effective way to mitigate damage in the event of a breach
Organizations find it hard to implement RBAC in situations where there are inter-company or intra-company transfers. A human resource executive could be shifted to the engineering department, or an employee could be fired from a company – in which case revoking their access immediately is necessary.
What is Policy-Based Access Control
Policy-Based Access Control sets policies to manage user access to data and systems. In a PBAC setting, the roles of each user are integrated with specific policies to establish access privileges. A manager may have a defined role and specific access policies are pre-set for this role. Upon setting up roles, users are subsequently added to these roles. The policies can be set once and implemented many times, making it relatively simple.
Some organizations handle extremely sensitive data, and any little lapse can lead to regulatory violations for companies resulting in fines and penalties. A certificate-less authentication would be a perfect solution for companies looking to implement PBAC as policy rules can be set at the time of issuing certificates at the outset.
What is Attribute-Based Access Control
The term Attribute-Based Access Control is pretty self-explanatory as it applies access policies based on very granular attributes for precise decision-making. A directory (or X.509 digital certificate) can store information like name, email address, geographical location, or environmental attributes like the AP from which you are accessing the network, time, device, and the last time of authorization.
However, applying attribute-based control may be difficult for an organization as some directories limit the types of information that can be stored about a user. X.509 certificates, on the other hand, can be encoded with any type of information – you can create custom attributes to tailor ABAC policies to your precise need.
Comparing RBAC, PBAC, and ABAC
Implementing Effective Network Access Control
Network Access Control is perceived to be tedious and perhaps complex to set up. However, SecureW2 provides a comprehensive NAC suite with all the tools and software needed to configure 802.1X EAP-TLS authentication and simplify the management of user certificates across networks. With SecureW2s 802.1X EAP-TLS authentication, you can customize user certificates and assign them access controls at the outset.
Click here to know the pricing options to unlock network control options for your organization.




