A High-Level Analysis of Various Encryption Algorithms Used in Wireless Security
Data encryption encodes data, making it hidden and inaccessible to an unauthorized user. Encryption is more common than we think. Data is transmitted as ciphertext whenever we access our email or applications, log in to a website, or connect to a VPN. This protects data from an interceptor who could gain access to a network with malicious intent.
Encrypting wireless networks is crucial when connecting to a network or website, as an unsafe or malicious link can lead to data and credential leaks. Wi-Fi Protected Access (WPA), developed by the Wi-Fi Alliance, ensures Wi-Fi security is more effective than its predecessor, Wired Equivalent Privacy (WEP).
Since the late 1990s, multiple iterations of wireless security standards, such as WPA, WPA2, and WPA3, have been used for better encryption and authentication. This article will explain why encryption algorithms are used in wireless security and how they help safeguard your wireless connections for a more robust and secure network.
Understanding Different Wireless Encryption Standards
Wireless networks are commonly encrypted using two main algorithms. The first is the Stream Cipher, which converts plaintext to cyphertext bit-by-bit. With the Stream cipher, encryption begins with an encryption key fed into the bit generator. It generates an 8-bit keystream, which initiates the encryption process.
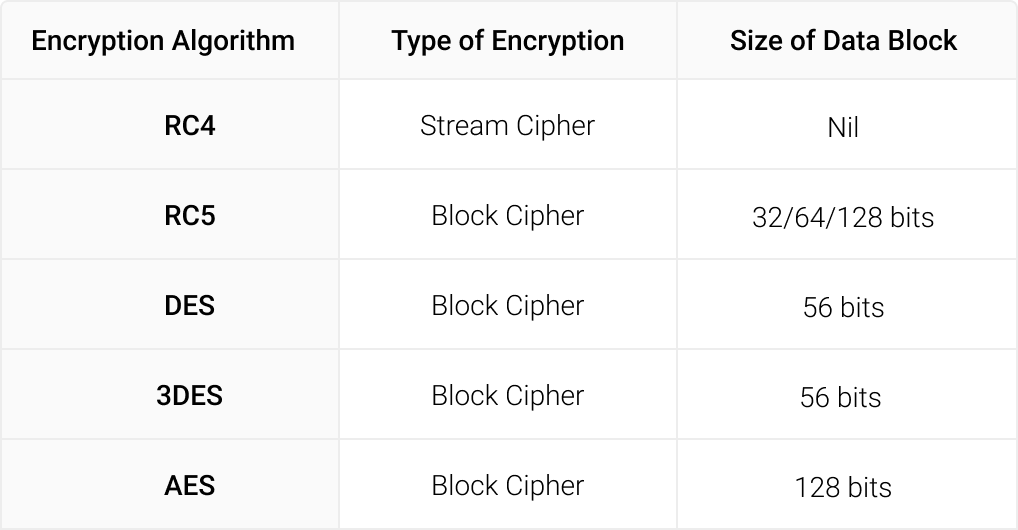
The Block Cipher works on a fixed-size chunk of data with a fixed encryption key and encrypts data in blocks to maximize security. Here are some encryption algorithms used by a wireless network.
In wireless networks, the most commonly encountered encryption algorithms are RC4 and AES. The most prevalent wireless network security standards are WEP, WPA, WPA2, and WPA3.
Wired Equivalent Privacy (WEP)
Wi-Fi Alliance developed the first encryption type, WEP, the first wireless protocol for authentication and encryption of Wi-Fi networks, based on the RC4 algorithm. WEP encrypts traffic using a 64-bit or a 128-bit key in hexadecimal, wherein all the data going back and forth is encrypted using the same key. As time passed, the same key usage became a security flaw despite the increase in the key size, and hackers could crack the key using tools in their systems. WEP was declared obsolete due to security flaws in 2004, but some administrators still use it on their routers, especially for older, unsupported devices.
Wi-Fi Protected Access (WPA)
Wi-Fi Protected Access (WPA) replaced WEP in 2003 and offered significant enhancements for key encryption and user authentication. WPA uses the Temporal Key Integrity Protocol (TKIP), which changes the key every time a system uses it. TKIP prevents a hacker from using his key to match the system’s key on a secure wireless network. It was eventually succeeded by the Advanced Encryption Standard (AES).
WPA uses the 256-bit key from the 64-bit and 128-bit keys used in WEP, but it is still vulnerable to attacks as it is password-protected.
Wi-Fi Protected Access 2 (WPA2)
WPA2 was introduced in 2004 to address the security flaws present in WPA and has two modes::
- The WPA2-PSK mode, which is suited for home setup and relies on passkeys for authentication.
- The WPA2-Enterprise mode, which supports digital certificates or individualized credentials for users and is suited for organizational use.
WPA2 mainly uses the Counter Mode Cipher Block Chaining Message Authentication Code Protocol (CCMP), based on the AES algorithm, for robust Wi-Fi security, authentication, and verification. However, WPA2 is still vulnerable to key reinstallation attacks (KRACK), in which a hacker can pose as a clone network and force a user to connect to a malicious network to steal data and credentials to decrypt the key.
The WPA2-PSK mode protects a Wi-Fi network with a single pre-shared key, which can be stolen or manipulated easily. However, WPA2-Enterprise mode supports digital certificates that are phishing-resistant compared to passwords.
EAP-TLS Process in WPA2- Enterprise Protocol
EAP-TLS supports digital certificates for passwordless authentication, offering robust Wi-Fi security compared to passwords and pre-shared keys. Digital X.509 certificates are phishing-resistant as they cannot be duplicated or stolen. EAP-TLS also uses client-server or mutual authentication, where the client authenticates the server and vice-versa. This makes EAP-TLS the most secure authentication protocol for users and devices on a network. WPA2-Enterprise enhances Wi-Fi security by supporting EAP-TLS encryption for certificate-based authentication and a Cloud RADIUS for mutual authentication.
EAP-TLS reduces the risk of a MITM attack to almost zero due to mutual server authentication and digital certificates. It also enhances the user experience, as a digital certificate can be created once and stays in the system until it is revoked, unlike passwords, which need periodic resets and can lead to disconnects.
Wireless Protected Access 3 (WPA3)
WPA3 is the latest Wi-Fi security protocol, created in 2018, and is technically superior to WPA2. It uses the Galois/ Counter Mode Cipher Block Chaining Message Authentication Code Protocol (GCMP) 256-bit encryption compared to the 128-bit encryption used in WPA2. WPA3 also addressed the KRACK vulnerability of the WPA2 protocol by patching the four-way handshake with the Simultaneous Authentication of Equals (SAE) feature. SAE transmits the credentials in a one-time message rather than a multi-way conversation, eliminating reusing pre-shared keys.
As of 2020, the Wi-Fi Alliance has mandated the support of WPA3 for all wireless devices seeking wireless support.
Comparing WEP, WPA, WPA2 And WPA3
WPA uses the RC4 stream cipher for encryption but is enhanced by TKIP for more secure encryption. WEP and WPA use the same encryption algorithm, RC4 encryption, while WPA2 uses the CCMP algorithm for a robust Wi-Fi connection. WPA3 uses the AES-CCMP deployed by homes and organizations to protect and encrypt classified data and credentials. WPA and WPA2 use the 4-way handshake for Wi-Fi connections, giving rise to the KRACK vulnerability.
The SAE handshake in WPA3 authenticates a device through a one-time conversation to protect a network from attacks. This method properly authenticates a device onto a network to protect connections from being attacked.
Which Wi-Fi Protocol Should You Use for Your Organizational Needs?
If you have unsecured wireless networks, a hacker can easily steal your credentials or data, resulting in loss of goodwill, compliance issues, and millions of dollars in fines. To protect your wireless routers, you should understand the differences between the various security types. WEP is an obsolete Wi-Fi security type that you should avoid, especially in a business setting. WPA is a stronger form of encryption but is vulnerable to key reinstallation attacks, making it a risky choice for enterprise Wi-Fi security.
WPA3 is a relatively newer protocol that has yet to be widely adopted, as there is little support for it. WPA2 is a widely used Wi-Fi protocol that supports smartphones, wireless routers, laptops, and IoT devices. WPA2-PSK uses pre-shared keys to secure your network and is unsuitable for organizational or business use. The WPA2-Enterprise uses digital certificates, considered the gold Wi-Fi security standard.
Digital X.509 certificates are phishing-resistant, as they cannot be stolen or duplicated. They are unique to each user and device and are populated with unique attributes for identity context, enabling network administrators to monitor who and what is connecting to their network.
Deploy WPA2-Enterprise for Your Wireless Networks With Digital Certificates For Robust Security
The WPA2-Enterprise supports digital certificates for superior 802.1X authentication, and SecureW2 makes certificate-based authentication a breeze. Setting up a PKI to manage certificates can be cumbersome, but our cloud-based PKI is designed for easy deployment. It is vendor-neutral and integrates seamlessly with your existing MDM and identity providers.
Our managed Cloud PKI facilitates end-point distribution of digital certificates to all your users and devices with user-friendly, zero-touch onboarding software. SecureW2 offers a Cloud RADIUS to enable passwordless authentication to verify network access requests and ensure that your network policies are applied in real-time with any cloud identity provider like Entra ID (Azure AD), Google, Okta, and OneLogin.
Click here for robust passwordless solutions against Wi-Fi vulnerabilities and unauthorized users.