
8 Cyberattacks that Could Happen if You Don’t Protect Layer 2
Cyberattacks are becoming more aggressive by the day. While getting everything on the cloud is a good practice, if your local network is not protected, your network is susceptible to cyberattacks.
You might think since your organization’s resources are all in the cloud, an attack on the local network will not put your network at risk. In reality, not protecting your layer 2 can have grave consequences, especially in a WPA2-PSK network. Once hackers gain access to your layer 2, all the layers are essentially compromised, and they can eventually crack passwords to access any and all information and applications in your network.
Pre-shared key or password-based authentication methods are not secure because they are distributed to everyone in the network and can be easily stolen or shared. In this article, we will discuss how layer 2, when not secured, can become an open gateway for hackers to infiltrate not just your local network but can also pave the way for them to access your resources in the cloud.
What Is Layer 2?
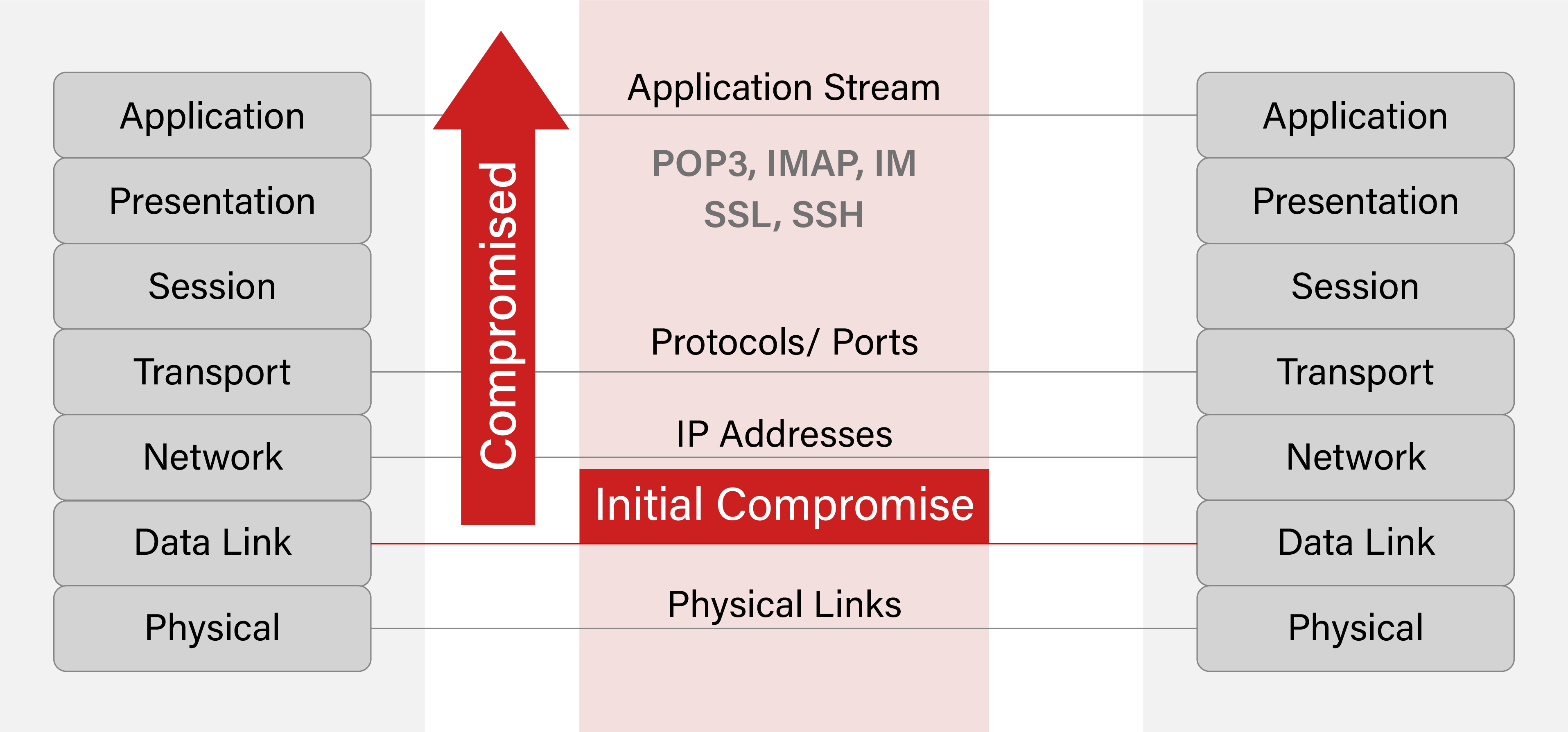
The data link layer of a network that facilitates data transfers between the physical links or devices and communication between switches is called layer 2. It is the 2nd layer of the Open Systems Interconnection (OSI) that helps boost network performance by facilitating high-speed connections between multiple devices.
The most common example of layer 2 or the data link layer is Ethernet. Devices used in an Ethernet network, such as network interface cards, switches, hubs, and bridges, are identified by a MAC (media access control) address. MAC addresses of any device are closely tied to the network interface cards and do not normally change unless the network interface card is changed.
OSI was designed to allow all the layers to work without one layer knowing how the other is working, and that makes it almost impossible to detect a layer 2 attack. The next section of this article discusses the vulnerabilities of layer 2 in a WPA2-PSK network.
Layer 2 Vulnerability With PSK Authentication
Protecting your layer 2 is crucial simply because it can be the perfect gateway for cyberattacks. Even if all your resources are in the cloud, the WPA2-PSK network still leaves room for hackers to infiltrate your layer 2, which can escalate and lead to you losing complete control over your network.
Pre-shared keys or passwords are not the safest way to protect your network. Passwords can be stolen physically as well as through over-the-air attacks like brute force attacks, phishing, a man-in-the-middle attack (MITM), or a rainbow table attack, to name a few. In that sense, a WPA2-PSK network is as good as an open network since it is not difficult for a hacker to crack a password.
If your layer 2 is not protected, anyone can access your Ethernet and carry out malicious attacks that cripple your network. Because each layer works without the knowledge of the other, even when layer 2 is compromised, users will not be aware until it’s too late since it will not impact the communication between the other layers.
What Is a Layer 2 Attack?
A layer 2 attack is when a hacker gains access to the Ethernet port with the intent to disable the network or compromise a user’s access to get passwords to log in to different applications in the network.
In a layer 2 attack, the hackers manipulate normal protocols, such as a switch’s ability to recognize a MAC address, and control Address Resolution Protocol (ARP-RFC 826) in order to manipulate end-station MAC address resolution or Dynamic Host Control Protocol (DHCP) server IP address assignments.
In a PSK environment, where anyone with a password can access the network, a layer 2 attack can cause considerable damage. Let’s look at some of the common layer 2 security attacks that can have devastating impacts on your network.
Address Resolution Protocol (ARP) Attacks
The Address Resolution Protocol (ARP) is used by all network devices connecting to an Ethernet network. ARP uses the target device’s IP address to find the MAC addresses for a destination device. ARP is not a secure method since it is based on the assumption that you can always trust the information.
An ARP attack is a man-in-the-middle (MITM) attack where a hacker device will pose as the actual device to communicate with the target device to access information.
MAC Address Flooding or Content Addressable Memory (CAM) Table Overflow
As its name suggests, in this type of attack, a switch is flooded with MAC addresses to the point where it exceeds the table limit. A switch has limited memory space to learn only a certain number of MAC addresses. Normally, once a switch learns a MAC address, it will send the packet intended for that address directly to that device instead of flooding it to the entire LAN.
However, at the time of the attack, the switch is flooded with MAC addresses. Once this limit exceeds, the switch floods packets to all ports in a virtual LAN (VLAN), and hackers can easily eavesdrop or sniff out network connections. This flooding also disrupts the normal flow of packets or stops the flow completely, ultimately becoming unusable.
Spanning Tree Protocol (STP) Attacks
The Spanning Tree Protocol (STP), used on LAN-switched networks, ensures the stability of the LAN by routing the network traffic through the most optimized path in order to terminate any potential loops within the network.
In an STP attack, the hacker will insert a new STP with the intent to interfere with the running of the actual STP. This will impact the overall traffic flow in the LAN and can compromise the overall security of the network.
Dynamic Host Configuration Protocol (DHCP) Spoofing
Most networks use Dynamic Host Configuration Protocol (DHCP) to communicate addresses and other critical information to clients. Spoofing of DHCP or losing control over it can have a grave impact on network security.
In this type of layer 2 attack, the hacker pretends to be the legitimate DHCP server by introducing a rogue DHCP server to the network. When clients request an address, the spoofed server responds first and establishes a connection with the client. Once the connection is established, the attacker can assign any address they want. The hacker can then take control of any device they choose as a gateway to your network and be able to steal any information they want without being detected.
Double Tagging
Double tagging is a type of virtual local area network hopping (VLAN hopping) attack where an attacker exploits the system of some switches, removing the outer tag for packets with a double tag (if the outer tag matches the native VLAN) to add or modify tags.
Virtual LANs security on LANs is provided by diverting traffic into different traffic lanes. At the time of transmitting traffic between switches, except for the native VLAN, traffic from all other VLANs are “tagged” with an IEEE 802.1q tag. In cases where there are multiple tags, some switches remove the outer tag when they match the native VLAN. This allows hackers to send traffic from one VLAN to the other. However, this can happen only after the hacker already has access to one of the VLANs of the network.
Media Access Control (MAC) Spoofing
A Media Access Control (MAC) spoofing attack is when a device uses the MAC address of another device with malicious intent to divert the traffic of the targeted device to the attacking device. The purpose of this can be anything from attempting to act as the target device or server to carrying out a denial-of-service attack.
A MAC spoofing attack is similar to someone taking control of your phone number to route all calls to a different number.
Switch Spoofing
Switch spoofing is another form of a virtual LAN (VLAN) hopping attack that is used to send traffic to another VLAN.
In this form of attack, the attackers try to connect a rogue switch to the network to set up a trunk. If they are successful, they can then divert traffic from multiple VLANs to the rogue switch, thereby taking control of the traffic and access to view information. Switch spoofing can be mitigated by disabling dynamic trunking.
Cisco Discovery Protocol (CDP)/Link Layer Discovery Protocol (LLDP) Reconnaissance
The Cisco Discovery Protocol (CDP)/Link Layer Discovery Protocol (LLDP) Reconnaissance has similar functionality, with the latter being the industry standard. They are protocols that are used to discover other devices and to advertise themselves in order to obtain or share information such as the OS version, IP address, etc.
This information is used by network engineers to enhance troubleshooting efficiency, especially in large networks. But they can be exploited by an attacker to obtain critical information about devices that they are listening to.
How Certificate-Based WPA2-Enterprise Can Secure Your Network Against Layer 2 Attacks
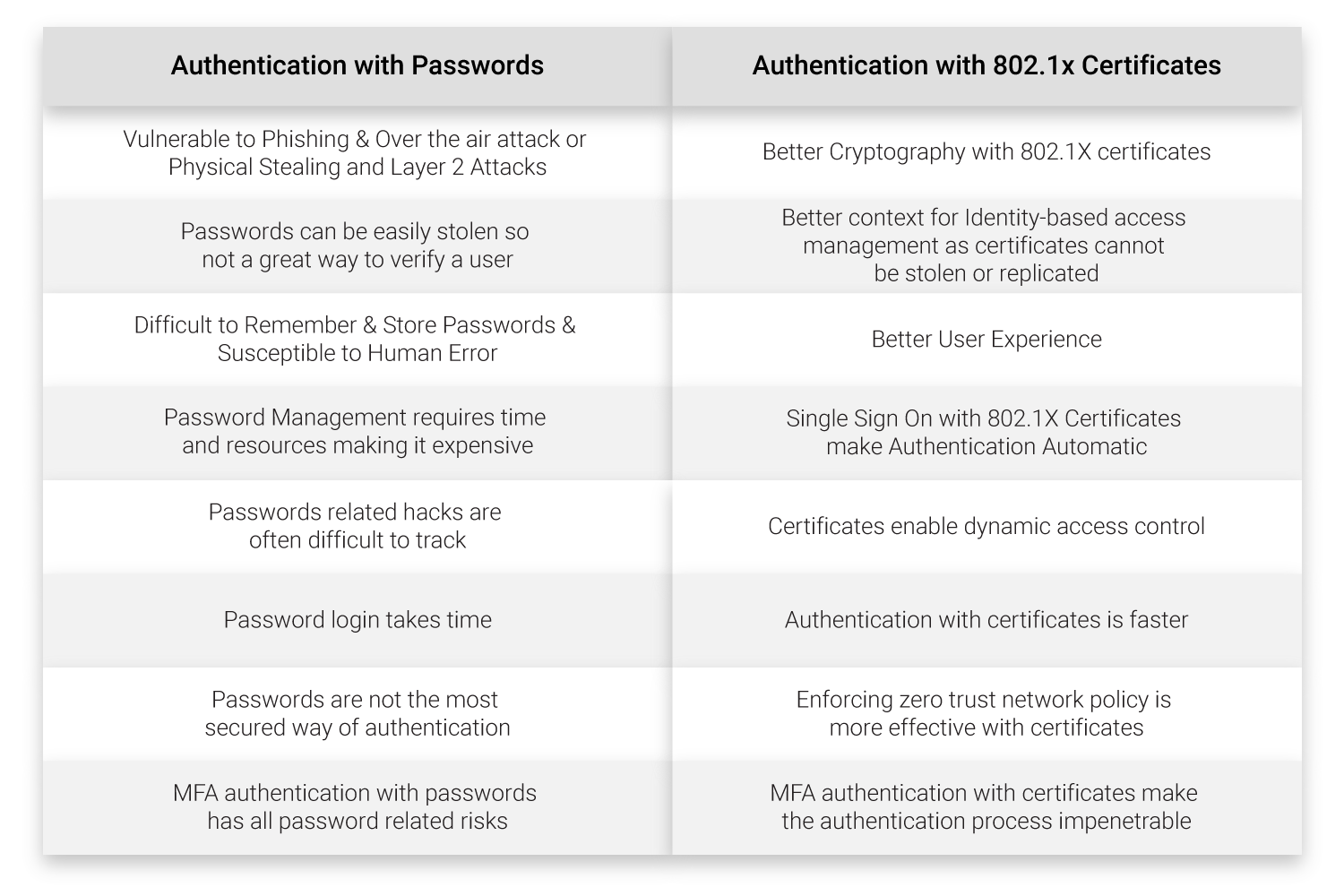
Certificate-based authentication is the best way to protect your network and mitigate layer 2 attacks. Here are some reasons why you should consider shifting to Certificate-Based WPA2 Enterprise:
- Improved User Experience
- Increased Identity Context
- Secure Authentication
Improved User Experience
With passwords, there is always the risk of a disgruntled employee sharing their password or a hacker cracking passwords to gain entry to your layer 2 to carry out any of the above-mentioned attacks. Certificates eliminate the need for human interaction, making them a seamless process of authentication with no room for human error.
Certificate-based authentication provides a better user experience and nullifies any password-related disconnects. You no longer have to reset your password periodically, worry about password reset tickets, or how to store passwords for different applications — all of which are gateways hackers can exploit to carry out layer 2 attacks such as CDP and LLDP that can cause extensive damage to your business.
Increased Identity Context
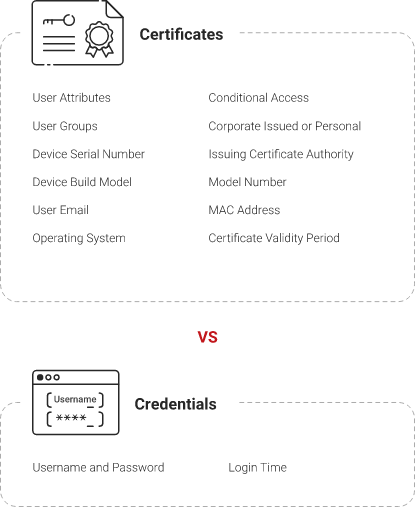
Certificates provide a better identity context than passwords. With certificates, you will know who is in your network since access will be granted only after verifying that all the information (unique to the client) stored in the certificates matches. With passwords, the only information provided during authentication is the username and passwords, and they can be easily stolen or stored, leaving room for spoofing or MITM attacks.
Your enterprise network is better protected with certificates since you have visibility over all your BYOD and managed devices. That eliminates the risk of spoofing attacks on your layer 2, such as MAC spoofing, switch spoofing, or DHCP spoofing.
You can take your network security for layer 2 one step further with Cloud RADIUS. It is the only EAP-TLS RADIUS in the industry that can do a real-time look-up with your cloud identity to get the most current status of a certificate. This enables it to dynamically stop any unauthorized access requests even before they can access your network.
Secure Authentication
X.509 certificates use public key infrastructure (PKI) that has two keys: public and private keys. The public key is not a secret and is shared openly, whereas the private key is stored in the device.
Authentication happens when a public key and private key handshake is successful, a key match that is a complicated algorithm and is almost impossible to crack. This match is done on both the server and client ends when their respective private keys have to match with the public key in order to establish a connection.
The private key is not sent over the air at any point during the authentication process. Therefore, there is nothing for a person to intercept, even if they are listening to the network. Certificates eliminate the risk of almost all layer 2 attacks because with certificate-based authentication, there are no passwords to steal and, therefore, no way for any unauthorized access to your layer 2.
Switch to Certificate-Based EAP-TLS to Mitigate Layer 2 Attacks
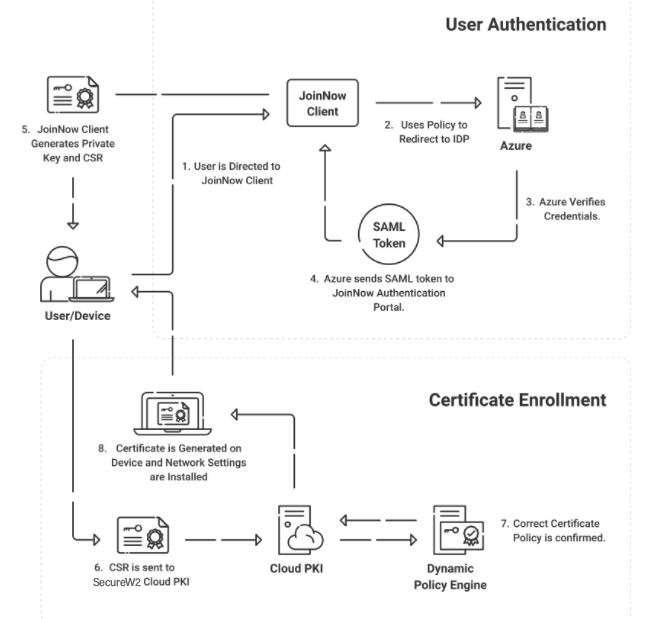
Securing your resources in the cloud is not enough. To make your network impenetrable, it is crucial to move away from passwords. Switching to certificate-based authentication may sound like a daunting task, but with the right solution, it can be a seamless process.
SecureW2’s managed PKI solutions are designed to work with your cloud solutions and can automate the entire lifecycle management of certificates for managed devices and BYOD. Our JoinNow MultiOS is perfect for onboarding BYOD devices with the click of a few buttons, and our managed device gateways can automatically distribute certificates to managed devices.
SecureW2’s Cloud RADIUS is a dynamic EAP-TLS RADIUS designed for passwordless certificate-based authentication that can perform real-time look-ups with your cloud identities, such as G-Suite, Okta, and Azure. It is a single-pane management software for all your network security needs. No matter the size of your organization, we provide customized solutions that best meet your needs. Click here to learn more about pricing.




