
Configure Cloud RADIUS for X.509 Certificate Authentication
In today’s swiftly evolving digital landscape, it is impossible to overstate the importance of comprehensive network security. Certificates for authentication have emerged as a preferable alternative to standard passwords as businesses seek to secure their resources and applications.
To use certificates securely, however, a trustworthy authentication method is required; this is where RADIUS comes in. Organizations may take network security to the next level by integrating Cloud RADIUS with X.509 certificates.
In this article, we’ll go into the specifics of this power couple, examining their interplay and providing a detailed setup approach for enabling X.509 certificate authentication. Let’s discover how to use this formidable security tool fully.
Understanding Cloud RADIUS
What Is Cloud RADIUS?
RADIUS has been extensively embraced by enterprises to administer user authentication and authorization for network access. With the increasing adoption of cloud computing, many organizations consider implementing cloud-based RADIUS servers to oversee network security. This section’ll explore the advantages of employing a cloud-based RADIUS server to enhance network security.
Cloud RADIUS Server Security Benefits
Here are some of the major advantages of Cloud RADIUS:
- Scalability
- Improved Security
- Reduced Costs
- Better Performance
- Easier Management
Scalability
Scalability is a key advantage of cloud-based RADIUS servers like Cloud RADIUS. It is less expensive and simpler to administer than a network of physically distributed servers. Remote employees may easily log in from anywhere globally, thanks to Cloud RADIUS.
Improved Security
Unlike on-premises servers, cloud-based RADIUS servers offer better security. Cloud service providers use strong security procedures like network security, data protection, and multi-factor identification. On-premises computers can be hacked or have their power cut off, so they need extra security.
Reduced Costs
Incorporating a cloud-based RADIUS server into your infrastructure can substantially reduce costs. Leveraging a cloud provider enables mitigating costly hardware, software licenses, and maintenance expenses typically incurred with on-premises solutions.
Better Performance
Due to the availability of redundant servers in various worldwide locations, cloud-based RADIUS servers may provide superior performance versus on-premises servers. Due to the global nature of cloud providers’ server networks, RADIUS servers may be strategically located to improve latency to end users. Organizations may reduce user-experience-degrading latency and boost network efficiency with the help of this technology.
To elaborate, businesses no longer need to set up a RADIUS server locally at each office, thanks to cloud-based companies like SecureW2 that provide redundant servers in different time zones. This method allows for optimal network performance and low latency without organizations needing to build several copies of physical servers in different places.
Easier Management
Cloud-based RADIUS servers streamline operations. Cloud providers provide RADIUS server setup, monitoring, administration tools and APIs. Remote server access allows network security management and quick reaction to security breaches.
Cloud-based RADIUS servers and managed RADIUS services have different administration and maintenance requirements. Our managed RADIUS solution handles software patches, upgrades, and maintenance, relieving customers of those chores. This removes the need for clients to construct and manage their own RADIUS server, making it easy.
Cloud RADIUS Components
The RADIUS-based remote access environment consists of three primary components:
- Access Client
- Network Access Server
- RADIUS Server
The Access Client can be an individual who initiates a dial-up connection to a Service Provider network for accessing various internet sites, commonly known as the User role. The Access Client can also function as a hardware component, such as an ISDN or dial-on-demand router, which facilitates network connectivity for numerous users within a small office or home office environment.
A Network Access Server (NAS) is a specialized networking device that identifies and manages connection requests from external sources beyond the network perimeter. Upon receipt of the user’s connection request, the NAS may initiate an initial access negotiation with the user, utilizing either PPP or SLIP protocols.
The initial access negotiation establishes specific data points such as the username, password, NAS device identifier, NAS port number, and other relevant information. Once the Network-Attached Storage (NAS) receives the data, it will forward it to the Remote Authentication Dial-In User Service (RADIUS) server for authentication purposes.
The RADIUS server will authenticate the request and grant authorization for services rendered over the established connection. The RADIUS server employs a process of cross-referencing information from the Network Access Server’s request with records in a reputable and established database.
Upon successful matching, the RADIUS server will grant user access. Failure to meet the system’s criteria will result in user rejection. The NAS will make a connection determination based on the RADIUS server’s response, either allowing the user’s connection (“accept packet” or “accept user”) or denying the user’s connection attempt (“reject packet” or “reject user”).
Then, upon successful transaction completion, the Network Attached Storage (NAS) system securely transmits the accounting data to the Remote Authentication Dial-In User Service (RADIUS) server for documentation purposes. The RADIUS server may subsequently store or forward this data to facilitate accurate billing for the rendered services.
Enhancing Security With X.509 Certificate Authentication
Introduction to X.509 Certificates
X.509 certificates serve as a crucial means of digital authentication for both users and servers during online communication. Additionally, these certificates hold immense potential for use in various other valuable applications.
Digital certificates enable secure communication between users and servers by leveraging vital public infrastructures to facilitate the encryption and decryption of sensitive, identifiable information. The X.509 certificate is the globally recognized industry standard for online identity authentication and offers robust defense against malicious impersonators. X.509 certificates provide reliable and impregnable online connections, from email communications to browser access.
Advantages of X.509 Certificate Authentication
X.509 certificates have several advantages:
- Secure communication: X.509 certificates serve as a crucial mechanism for enabling a robust and secure mode of communication between two entities. They accomplish this by providing reliable encryption and authentication and preventing unauthorized access or data interception.
- Digital identity verification: X.509 certificates provide a highly secure and reliable method for verifying the digital identity of various entities, including individuals, organizations, and devices. This ensures the authenticity and integrity of the information or transaction by verifying its source as credible and trustworthy.
- Interoperability: The utilization of X.509 certificates is prevalent and acknowledged by diverse applications and platforms, ensuring interoperability between different systems. This guarantees that the certificate can be employed in a variety of environments.
- Scalability: Implementing X.509 certificates enables effortless scalability for large-scale deployments, enabling organizations to securely handle and verify many users or devices.
- Compliance: Adherence to security and privacy standards necessitates organizational compliance with industry regulations mandating the utilization of X.509 certificates.
- Flexibility: X.509 certificates have adaptability, as they can be tailored to incorporate supplementary data or extensions, empowering entities to add prerequisites or information at their discretion.
In cybersecurity, X.509 certificates are a highly dependable means of establishing trust and guaranteeing secure communication and digital identity authentication across various applications and sectors.
RADIUS Authentication Flow
Passwords are an alternative to certificates that may be used with RADIUS; however, even though this is technically possible, it is not encouraged due to security concerns. Certificates provide a higher degree of verification and are more resistant to the typical dangers faced in information.
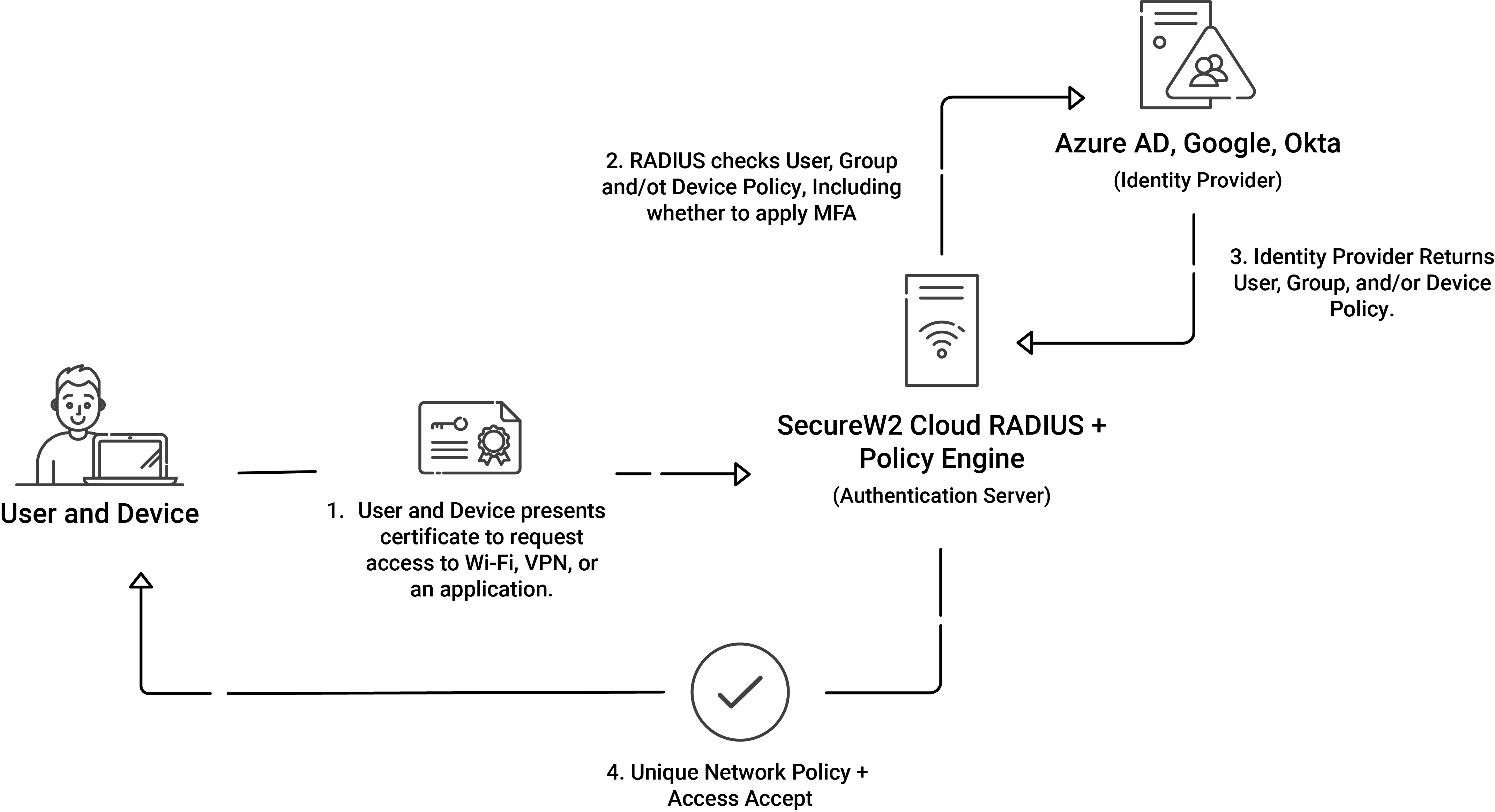
The RADIUS authentication process, while using certificates, entails multiple steps to ensure a secure connection between the client device and the server.
- The initial phase involves the client device initiating a connection request to an access point.
- Upon initiating the connection request, a Transport Layer Security (TLS) handshake protocol ensues between the client and the server. In this handshake, the server transmits its certificate, which encompasses a public key utilized to validate the server certificate.
- The process of validating the server certificate involves a comparison of the public key with its corresponding private key by the client. The verification process includes an assessment of the server certificate’s CA against the trusted root store.
- Upon receipt of the request, the client duly transmits its certificate, which encompasses its public key, to the server. The server undergoes a similar validation procedure to verify the legitimacy of the client certificate.
- On successful validation, the server proceeds to authenticate the client, granting it network access based on the established trust.
- Upon successful authentication, the RADIUS server performs authorization to ascertain the specific resources that the client is permitted to access. The grant of approval is contingent upon the policy rules configured within the directory or on the certificates.
Implementing these measures guarantees a robust and trustworthy authentication mechanism within a RADIUS framework between the client and server.
How to Configure Cloud RADIUS for X.509 Certificate Authentication
Depending on your RADIUS provider, you may need to take different steps to set up Cloud RADIUS for X.509 certificate authentication. However, certificates can be easily integrated into Cloud RADIUS because of its specialized architecture. This section cover the basics of setting up certificate-based authentication using a common Identity Provider (IDP) like Azure AD and Cloud RADIUS’s PKI services.
Configuring Cloud RADIUS for X.509 Certificate Authentication can generally be broken into three phases:
- A PKI, such as SecureW2’s, that is tied to your Identity Provider.
- Utilizing a Cloud RADIUS service that is also tied to your infrastructure.
- If you use one, integrate your PKI with your MDM (Such as Intune, Jamf, Google, etc.).
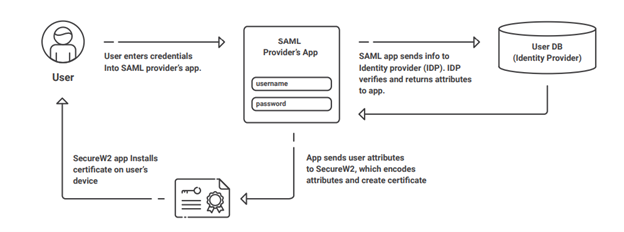
However, each phase has its own individual steps you’ll need to take. As a prerequisite, you may also need to configure a SAML application in Azure AD since this application is used by our BYOD onboarding technology, JoinNow MultiOS.
For the following example configuration steps, we’ll discuss configuration if you are using Azure AD for your IDP and Intune for your MDM.
Step 1: Configure SecureW2 PKI Services and Certificate Attribute Mapping
Configure Attribute Mapping in SecureW2
SecureW2’s attribute mapping settings may be adjusted in the Administration Portal under Identity Management > Identity Providers. To map properties like “upn,” “email,” and “displayName,” among others, you’ll need to edit the IDP and go to the Attribute Mapping tab. Set the URLs as the remote attributes. Set the group map property and assign Object ID values from the Microsoft Azure Portal to map local and distant groups. Finally, create and revise the settings.
Update the Profile Policy in SecureW2
SecureW2’s policy profile can be edited under the Administration dashboard’s Policy Management > Profile area. To change the Identity Provider (IDP) a profile uses, edit the policy and go to the Settings page. When you’re done making changes, click the Update button.
Update the User Role Policy in SecureW2
SecureW2’s policy on user roles can be modified using the portal’s Management > Policy Management > User Roles menu. Choose the Identity Provider (IDP) you want to use from the dropdown menu and save your changes to the DEFAULT ROLE POLICY 1’s Conditions tab. When you’re done making adjustments, click Update.
Add a User Role Policy in SecureW2
SecureW2’s Add Role button is in the Policy Management > User Roles sub-menu. Simply give this new file a name and hit the Save button. Then, save the policy by going to the Conditions tab, choosing an Identity Provider from the list, and clicking Update.
Add an Enrollment Policy in SecureW2
The Add Enrollment Policy button is in SecureW2’s Enrollment section. To give your new account a title, please use the Name form. Select the user role from the User Role list and the device role policy from the Device Role list in the Conditions tab. When you’re ready, click Update to put the rule into effect.
Republish Your Network Profile
Go to Device Onboarding > Network Profiles in SecureW2 and then choose Publish or Republish next to the profile you want to update. Please wait between 60 and 90 seconds while we submit your changes. If the download was successful, you may access the Wi-Fi wrapper package by selecting View and then clicking the JoinNow button. Launch the downloaded file, sign in with your Azure credentials if required, and verify that you were successfully enrolled and connected.
For a deeper understanding of these points, refer to this guide.
Step 2: Integrate With Your Identity Provider (IDP) by Creating an App in Azure for RADIUS Lookup
SecureW2 provides a streamlined integration process with prominent SAML and LDAP IDPs for user authentication and certificate enrollment. It is recommended to adhere to the integration guides offered by SecureW2 for seamless integration with your preferred Identity Provider (IDP). Common integration alternatives encompass LDAP, Google Apps, Active Directory, Azure AD, and Okta.
As an example, we’ll explain how you configure this if your organization uses Azure AD.
New App Registration
Sign into Azure, then go to App Registrations to add a new registration for your app. Select New Registration and then set up the new app registration as needed.
Create a Client Secret
Navigate to the Manage menu, then choose Certificates & Secrets to generate a client secret for use with Azure. Click New Client Secret and give the secret a name in the Description box. Select a due date, and then hit Add. In the Value field, you’ll see the newly produced client secret. Remember that if you lose it, there is no way to get it back.
Create a Provider URL and Client ID
Azure’s Overview page is where you may get your application (client) ID and provider URL. To be used later. Also, be sure to copy your tenant ID from the Directory. Replace “Directory (tenant) ID” with your own Directory (tenant) ID in the following URL format: https://login.microsoftonline.com. Put this service provider’s URL in your bookmarks.
API Permissions
Under the Manage tab, click on API Permissions to allow the app to access your Azure directory. To provide access, choose the Add a Permission option. Once you’ve added the necessary rights, you can finish setting them up by selecting Grant Admin Consent For Your Organization.
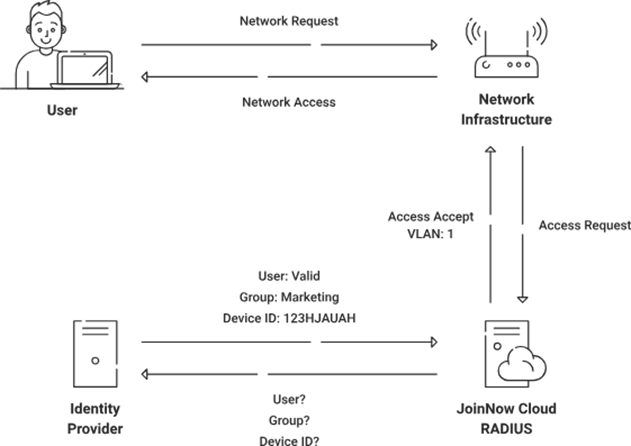
Step 3: Enroll Users for Certificates
a. Create an Onboarding SSID to facilitate the BYOD Self-Service Certificate Enrollment process.
We recommend employing SecureW2’s JoinNow suite, a top-tier solution for configuring devices to enable self-enrollment of X.509 certificates. Establish an Open Service Set Identifier (SSID) for onboarding, leading users through a streamlined enrollment procedure, guaranteeing a seamless and secure experience.
b. Apply Gateway APIs for the automated enrollment of managed devices in certificate management.
Implement SecureW2’s Managed Device Gateway APIs to optimize the enrollment procedure for managed devices. The APIs mentioned above facilitate the automated registration of machine and user certificates across all supervised devices, effortlessly integrating with prominent MDM software.
c. Installing Intermediate and Root CA Certificates to a RADIUS Server
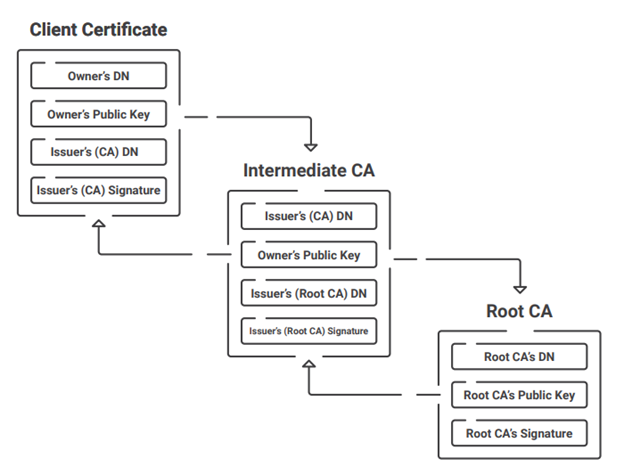
Installing the Root and Intermediate CA certificates from SecureW2’s PKI, the JoinNow Cloud Connector, is required to allow precise certificate authentication on the RADIUS server. Here’s how it works:
● Set up the Secure SSID.
Configure a secure SSID using certificate authentication and WPA2-Enterprise for the highest level of protection. Clients may connect to the SSID quickly and securely after enrolling in certificates.
● Integrate SecureW2’s PKI with your RADIUS server.
Add the SecureW2 PKI’s Root and Intermediate CA certificates to the trusted list in the RADIUS server settings. This enables the RADIUS server to authenticate clients who provide their certificates.
● Set up your RADIUS server’s authentication and authorization policies.
Specify the authentication protocol to be used (such as EAP-TLS or PEAP-MSCHAPv2) when defining the authentication policy on the RADIUS server. Configure the authorization procedure after successful authentication, which may include delivering an “Access-Accept” message or dividing the client into groups according to other regulations.
Simplifying RADIUS Configuration for Enhanced Network Security
In conclusion, setting up a RADIUS (AAA) server in the cloud using SecureW2 gives a simplified and effective X.509 certificate authentication method. Organizations may create a robust and secure network authentication framework using SecureW2’s extensive PKI capabilities, easy interaction with identity providers, and user-friendly certificate enrollment procedures.
With SecureW2’s Cloud RADIUS solution, there aren’t any hassles with installing and managing on-premise RADIUS servers. SecureW2 offers a customizable solution catering to your unique architecture and can interface with major RADIUS servers seamlessly.
Experience Cloud RADIUS benefits and features. Discover how our sophisticated features and industry-leading support can improve network security and authentication.
Get in touch with us to learn more about how our Cloud RADIUS service can improve your company’s authentication procedures.